Kaiji is a Linux malware that targets cloud servers
Last week we detected a new Kaiji variant. It was undetected by all 63 engines in VirusTotal at the time. So how did we detect it?

Genetic Analysis of new Kaiji variant
First, some background on Kaiji. Kaiji is a Linux malware discovered last year. It targets Linux cloud servers and spreads via SSH brute forcing. Kaiji’s main purpose is to compromise servers and make them part of a botnet used to conduct distributed denial-of-service (DDoS) attacks.
Interestingly, the malware was written from scratch which is rare to see among DDoS botnets. Attackers normally derive their tools from popular and tested open-source malware code (Mirai for example) or ready-made tools that they can buy easily on the black market (like BillGates).
A few months after our publication, Kaiji was in the news again, infecting misconfigured Docker servers to carry out DDoS attacks. Docker servers are relatively convenient to deploy in the cloud, making them a popular choice for enterprises but also an attractive target for attackers.
Docker security best practices. This guide provides tips for better Docker container security from development onto the runtime environment.
Detecting Malware Mutations
How did we detect this new Kaiji variant when no one else did? The answer is code reuse.
43db5e57f657c0a9568b4dd73586bf8d in VirusTotal
After last year’s publication exposing Kaiji’s operations, the detection rate of their tools started to go up among other security solutions. Mission accomplished. Kaiji had to undergo changes in order to fly under the radar while continuing operations.
With this latest variant, the authors behind Kaiji have reimplemented most of their code. This allowed the malware to bypass all Antiviruses in VirusTotal. However, they did reuse some code from previous Kaiji versions. About 8% of the new variant’s code was reused from older Kaiji samples according to its genetic analysis report.
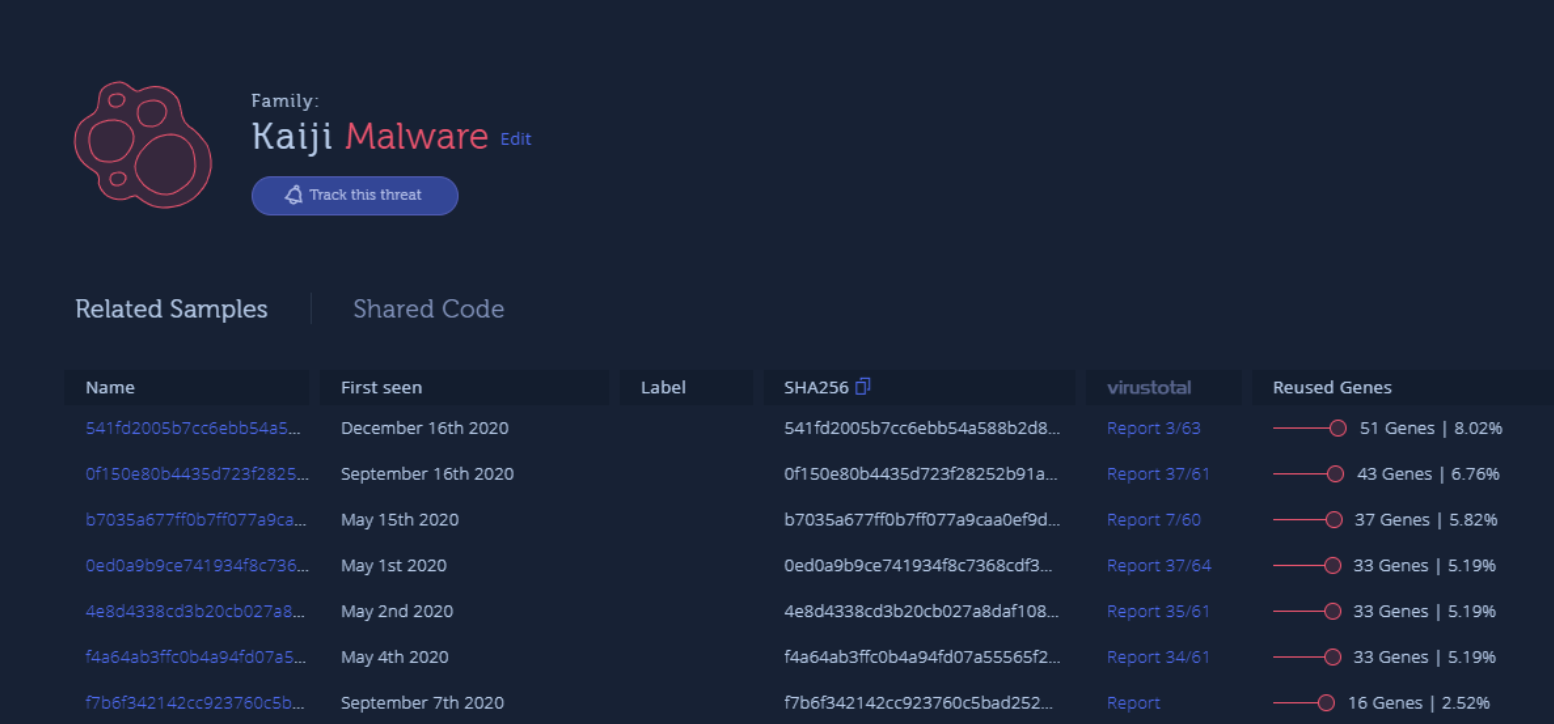
New Kaiji variant shares code with previous versions
This is the most dramatic code mutation we have tracked in Kaiji so far and we expect the malware will continue to evolve its tools to evade traditional solutions.
A New Way to Detect Threats
We detect mutations of threats by recognizing even the slightest amount of code reuse. This technology is helping security teams protect their cloud workloads and accelerate daily incident response processes. 8% code reuse may not seem like a lot but it was enough to detect this threat as Kaiji.
It’s not to say that traditional detection methods aren’t effective. It’s just that threats are getting more advanced. Signature-based detection depends on an actively maintained record of unique threat identifiers. This can be useful for detecting common threats. Yet in the case of Kaiji, cutting-edge malware often evades signature-based detection until multiple parties identify and confirm it.
The same applies for anomaly-based detection. This approach detects suspicious behavior. It can, however, be evaded by attacks which are designed to mimic normal behavior. Threat detection based solely on behavioral indicators can provide a false sense of security if an attack doesn’t generate any noise, posing the risk that the threat can infiltrate the network without being identified.
Malware developers are much like normal developers. They suffer from the same challenges and reuse already written code to make their lives easier and deploy tools faster.
What if Malware Rewrites Code from Scratch?
This is a considerable undertaking that expends the developer’s time and money. It’s more likely that they will rewrite some or most of the code from scratch but not do a complete retooling like what happened in this Kaiji example.
Ultimately, if an attacker is forced to rewrite their code from scratch that means we did our job as defenders. Once the code has been indexed it is significantly harder for attackers to launch an attack in the future without going detected. Our security solutions also highlight unique, never-before-seen code, crucial for detecting threats written from scratch.
Fastest to Detect Linux Threats
Protect your cloud environments against the latest Linux cloud threats. Give our free community edition a try. We provide runtime security for Linux servers, VMs, containers, Kubernetes, and more.
We’d be happy to show you a demo and also have lab environments available for you to try. Simulate backdoors, malware, cryptominers and Living-off-the-Land (LotL) attacks on the cloud.
The post Kaiji Goes Through Update but Code Reuse Detects It appeared first on Intezer.
Article Link: https://www.intezer.com/blog/cloud-security/kaiji-goes-through-update-but-code-reuse-detects-it/
