Targeted attacks
The leap of a Cycldek-related threat actor
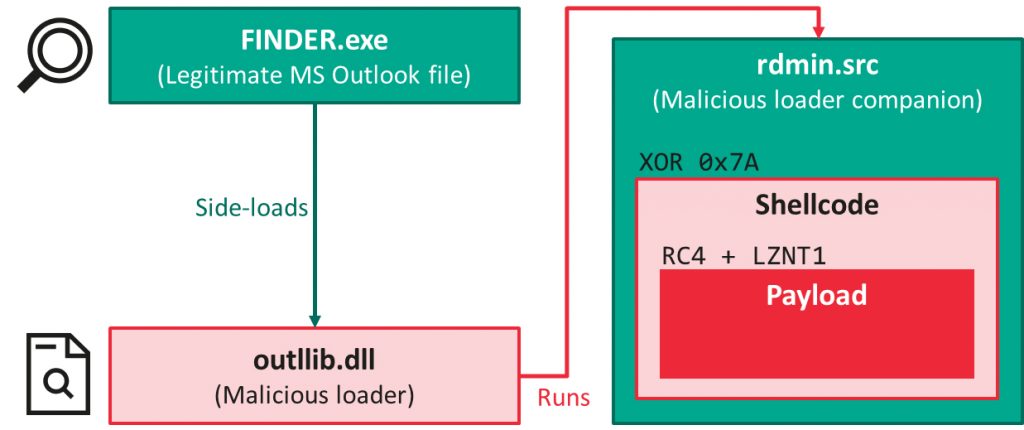
It is quite common for Chinese-speaking threat actors to share tools and methodologies: one such example is the infamous “DLL side-loading triad”: a legitimate executable, a malicious DLL to be side-loaded by it and an encoded payload, generally dropped from a self-extracting archive. This was first thought to be a signature of LuckyMouse, but we have observed other groups using similar “triads”, including HoneyMyte. While it is not possible to attribute attacks based on this technique alone, efficient detection of such triads reveals more and more malicious activity.
We recently described one such file, called “FoundCore”, which caught our attention because of the various improvements it brought to this well-known infection vector. We discovered the malware as part of an attack against a high-profile organization in Vietnam. From a high-level perspective, the infection chain follows the expected execution flow:
However, in this case, the shellcode was heavily obfuscated – the technical details were presented in the ‘The leap of a Cycldek-related threat actor‘ report. We found the loader for this file so interesting that we decided to base one of the tracks of our Targeted Malware Reverse Engineering course on it.
The final payload is a remote administration tool that provides full control over the victim machine to its operators. Communication with the server can take place either over raw TCP sockets encrypted with RC4, or via HTTPS.
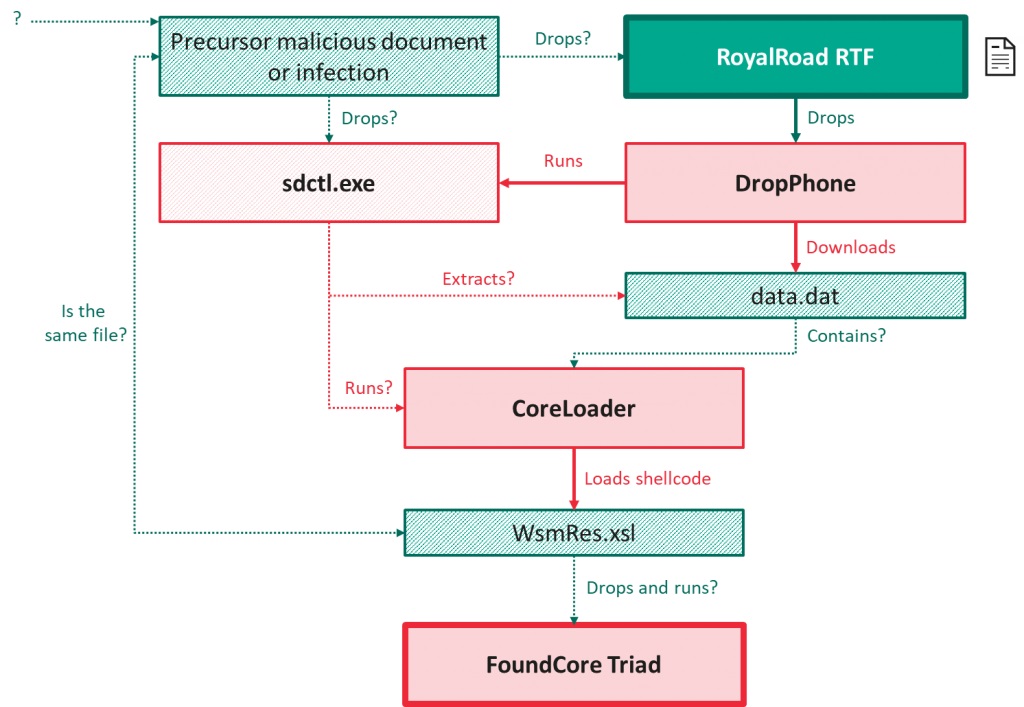
In the vast majority of the incidents we discovered, FoundCore executions were preceded by the opening of malicious RTF documents downloaded from static.phongay[.]com – all generated using RoyalRoad and attempting to exploit CVE-2018-0802. All of these documents were blank, suggesting the existence of precursor documents – possibly delivered by means of spear-phishing or a previous infection – that trigger the download of the RTF files. Successful exploitation leads to the deployment of further malware – named DropPhone and CoreLoader.
Our telemetry indicates that dozens of organizations were affected, belonging to the government or military sector, or otherwise related to the health, diplomacy, education or political verticals. Eighty percent of the targets were in Vietnam, though we also identified occasional targets in Central Asia and Thailand.
While Cycldek has so far been considered one of the least sophisticated Chinese-speaking threat actors, its targeting is consistent with what we observed in this campaign – which is why we attribute the campaign, with low confidence, to this threat actor.
Zero-day vulnerability in Desktop Window Manager used in the wild
While analyzing the CVE-2021-1732 exploit, first discovered by DBAPPSecurity Threat Intelligence Center and used by the BITTER APT group, we found another zero-day exploit that we believe is linked to the same threat actor. We reported this new exploit to Microsoft in February and, after confirmation that it is indeed a zero-day, Microsoft released a patch for the new zero-day (CVE-2021-28310) as part of its April security updates.
CVE-2021-28310 is an out-of-bounds (OOB) write vulnerability in dwmcore.dll, which is part of Desktop Window Manager (dwm.exe). Due to the lack of bounds checking, attackers are able to create a situation that allows them to write controlled data at a controlled offset using the DirectComposition API. DirectComposition is a Windows component that was introduced in Windows 8 to enable bitmap composition with transforms, effects and animations, with support for bitmaps of different sources (GDI, DirectX, etc.).
The exploit was initially identified by our advanced exploit prevention technology and related detection records. Over the past few years, we have built a multitude of exploit protection technologies into our products that have detected several zero-days, proving their effectiveness time and again.
We believe this exploit is used in the wild, potentially by several threat actors, and it is probably used together with other browser exploits to escape sandboxes or obtain system privileges for further access.
You can find technical details on the exploit in the ‘Zero-day vulnerability in Desktop Window Manager (CVE-2021-28310) used in the wild‘ post. Further information about BITTER APT and IOCs are available to customers of the Kaspersky Intelligence Reporting service: contact [email protected].
Operation TunnelSnake
Windows rootkits, especially those operating in kernel space, enjoy high privileges in the system, allowing them to intercept and potentially tamper with core I/O operations conducted by the underlying OS, like reading or writing to files or processing incoming and outgoing network packets. Their ability to blend into the fabric of the operating system itself is how rootkits have gained their notoriety for stealth and evasion.
Nevertheless, over the years, it has become more difficult to deploy and execute a rootkit component in Windows. The introduction by Microsoft of Driver Signature Enforcement and Kernel Patch Protection (PatchGuard) has made it harder to tamper with the system. As a result, the number of Windows rootkits in the wild has decreased dramatically: most of those that are still active are often used in high-profile APT attacks.
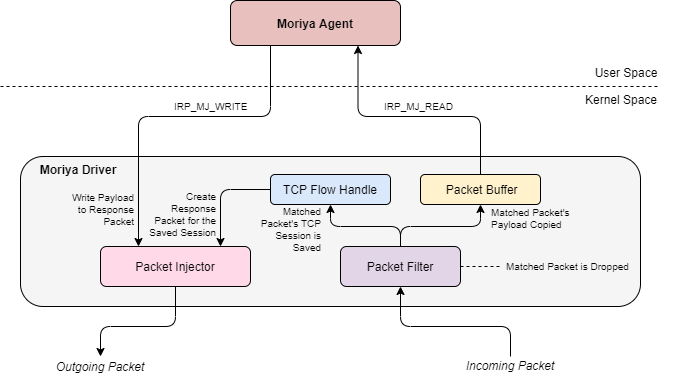
One such example came to our attention during an investigation last year, in which we uncovered a previously unknown and stealthy implant in the networks of regional inter-governmental organizations in Asia and Africa. This rootkit, which we dubbed “Moriya”, was used to deploy passive backdoors on public facing servers, facilitating the creation of a covert C2 (Command and Control) communication channel through which they can be silently controlled.
This tool was used as part of an ongoing campaign that we named “TunnelSnake“. The rootkit was detected on the targeted machines as early as November 2019; and another tool we found, showing significant code overlaps with the rootkit, suggests that the developers had been active since at least 2018.
Since neither the rootkit nor other lateral movement tools that accompanied it during the campaign relied on hardcoded C2 servers, we could gain only partial visibility into the attacker’s infrastructure. However, the bulk of the detected tools besides Moriya, consist of both proprietary and well-known pieces of malware that were previously in use by Chinese-speaking threat actors, giving a clue to the attacker’s origin.
PuzzleMaker
On April 14-15, Kaspersky technologies detected a wave of highly targeted attacks against multiple companies. Closer analysis revealed that all these attacks exploited a chain of Google Chrome and Microsoft Windows zero-day exploits.
While we were not able to retrieve the exploit used for Remote Code Execution (RCE) in the Chrome web-browser, we were able to find and analyze an Escalation of Privilege (EoP) exploit used to escape the sandbox and obtain system privileges. This EoP exploit was fine-tuned to work against the latest and most prominent builds of Windows 10 (17763 – RS5, 18362 – 19H1, 18363 – 19H2, 19041 – 20H1, 19042 – 20H2), and exploits two distinct vulnerabilities in the Microsoft Windows OS kernel.
On April 20, we reported these vulnerabilities to Microsoft and they assigned CVE-2021-31955 to the Information Disclosure vulnerability and CVE-2021-31956 to the EoP vulnerability. Both vulnerabilities were patched on June 8, as a part of the June Patch Tuesday.
The exploit-chain attempts to install malware in the system through a dropper. The malware starts as a system service and loads the payload, a “remote shell”-style backdoor, which in turns connects to the C2 to get commands.
We weren’t able to find any connections or overlaps with a known threat actor, so we tentatively named this cluster of activity PuzzleMaker.
Andariel adds ransomware to its toolset
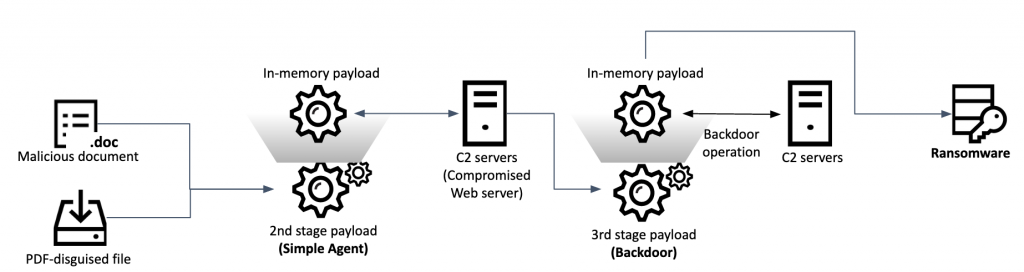
In April, we discovered a suspicious Word document containing a Korean file name and decoy uploaded to VirusTotal. The document contained an unfamiliar macro and used novel techniques to implant the next payload. Our telemetry revealed two infection methods used in these attacks, with each payload having its own loader for execution in memory. The threat actor only delivered the final stage payload for selected victims.
During the course of our research, Malwarebytes published a report with technical details about the same series of attacks, which attributed it to the Lazarus group. However, after thorough analysis, we reached the conclusion that the attacks were the work of Andariel, a sub-group of Lazarus, based on code overlaps between the second stage payload in this campaign and previous malware from this threat actor.
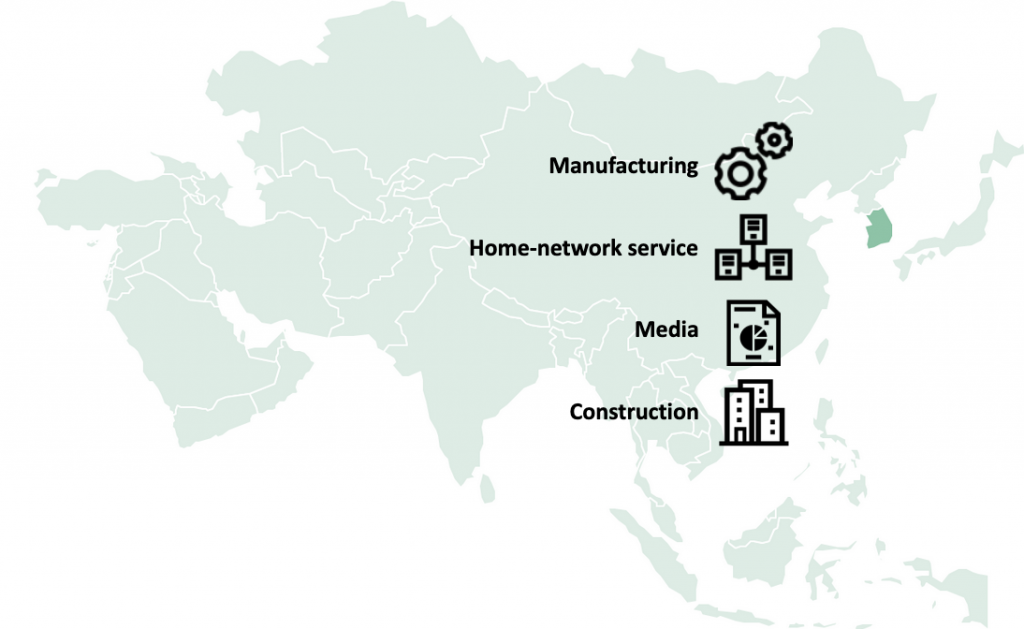
Historically, Andariel has mainly targeted organizations in South Korea; and our telemetry suggests that this is also the case in this campaign. We confirmed several victims in the manufacturing, home network service, media and construction sectors.
We also found additional connections with the Andariel group. Each threat actor has a characteristic habit when they interactively work with a backdoor shell in the post-exploitation phase of an attack. The way Windows commands and their options were used in this campaign is almost identical to previous Andariel activity.
Notably, in addition to the final backdoor, we discovered one victim infected with custom ransomware, underlying the financial motivation of this threat actor.
Ferocious Kitten
Ferocious Kitten is an APT threat actor that has targeted Persian-speaking individuals who appear to be based in Iran. The group has mostly operated under the radar and, as far as we know, has not been covered by security researchers. The threat actor attracted attention recently when a lure document was uploaded to VirusTotal and went public thanks to researchers on Twitter. Since then, one of its implants has been analyzed by a Chinese threat intelligence firm.
We were able to expand on some of the findings about the group and provide insights into the additional variants that it uses. The malware dropped from the lure document, dubbed “MarkiRAT”, records keystrokes, clipboard content, and provides file download and upload capabilities as well as the ability to execute arbitrary commands on the victim’s computer. We were able to trace the implant back to at least 2015, along with variants intended to hijack the execution of Telegram and Chrome applications as a persistence method.
Ferocious Kitten is one of the groups that operate in a wider eco-system intended to track individuals in Iran. Such threat groups aren’t reported very often; and so are able to re-use infrastructure and toolsets without worrying about them being taken down or flagged by security solutions. Some of the TTPs used by this threat actor are reminiscent of other groups that are active against a similar set of targets, such as Domestic Kitten and Rampant Kitten.
Other malware
Evolution of JSWorm ransomware
While ransomware has been around for a long time, it has evolved over time as attackers have improved their technologies and refined their tactics. We have seen a shift away from the random, speculative attacks of five years ago, and even from the massive outbreaks such as WannaCry and NotPetya. Many ransomware gangs have switched to the more profitable tactic of “big-game hunting”; and news of ransomware attacks affecting large corporations, and even critical infrastructure installations, has become commonplace. Moreover, there’s now a well-developed eco-system underpinning ransomware attacks.
As a result, even though the number of ransomware attacks has fallen, and individuals are probably less likely to encounter ransomware than a few years ago, the threat to organizations is greater than ever.
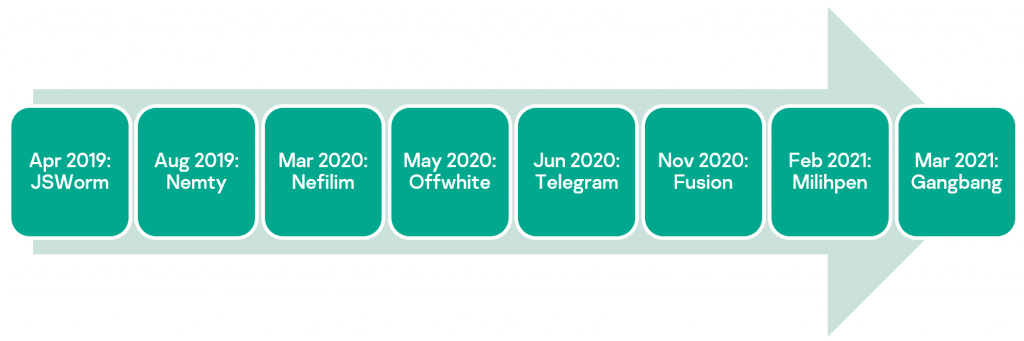
We recently published analysis of one such ransomware family, named JSWorm. This malware was discovered in 2019, and since then different variants have gained notoriety under various names such as Nemty, Nefilim, Offwhite and others.
Each “re-branded” version has included alterations to different aspects of the code – file extensions, cryptographic schemes, encryption keys, programming language and distribution model. Since it emerged, JSWorm has developed from a typical mass-scale ransomware threat affecting mostly individual users into a typical big-game hunting ransomware threat attacking high-profile targets and demanding massive ransom payments.
Black Kingdom ransomware
Black Kingdom first appeared in 2019; in 2020 the group was observed exploiting vulnerabilities (such as CVE-2019-11510) in its attacks. In recent activity, the ransomware was used by an unknown adversary for exploiting a Microsoft Exchange vulnerability (CVE-2021-27065, aka ProxyLogon). This ransomware family is much less sophisticated than other Ransomware-as-a-Service (RaaS) or big game hunting families. The group’s involvement in the Microsoft Exchange exploitation campaign suggests opportunism rather than a resurgence in activity from this ransomware family.
The malware is coded in Python and compiled to an executable using PyInstaller. The ransomware supports two encryption modes: one generated dynamically and one using a hardcoded key. Code analysis revealed an amateurish development cycle and the possibility of recovering files that have been encrypted with Black Kingdom with the help of the hardcoded key. At the time of analysis, there was already a script to recover files encrypted with the embedded key.
Black Kingdom changes the desktop background to a note that the system is infected while it encrypts files, disabling the mouse and keyboard as it does so.
*************************** | We Are Back ? ***************************We hacked your (( Network )), and now all files, documents, images,
databases and other important data are safely encrypted using the strongest algorithms ever.
You cannot access any of your files or services .
But do not worry. You can restore everthing and get back business very soon ( depends on your actions )before I tell how you can restore your data, you have to know certain things :
We have downloaded most of your data ( especially important data ) , and if you don’t contact us within 2 days, your data will be released to the public.
To see what happens to those who didn’t contact us, just google : ( Blackkingdom Ransomware )
| What guarantees ?
We understand your stress and anxiety. So you have a free opportunity to test our service by instantly decrypting one or two files for free
just send the files you want to decrypt to ([email protected]
| How to contact us and recover all of your files ?
The only way to recover your files and protect from data leaks, is to purchase a unique private key for you that we only posses .
[ + ] Instructions:
1- Send the decrypt_file.txt file to the following email ===> [email protected]
2- send the following amount of US dollars ( 10,000 ) worth of bitcoin to this address :
[ 1Lf8ZzcEhhRiXpk6YNQFpCJcUisiXb34FT ]
3- confirm your payment by sending the transfer url to our email address
4- After you submit the payment, the data will be removed from our servers, and the decoder will be given to you,
so that you can recover all your files.Note
Dear system administrators, do not think you can handle it on your own. Notify your supervisors as soon as possible.
By hiding the truth and not communicating with us, what happened will be published on social media and yet in news websites.Your ID ==>
FDHJ91CUSzXTquLpqAnP
After decompiling the Python code, we discovered that the code base for Black Kingdom has its origins in an open-source ransomware builder available on GitHub. The group adapted parts of the code, adding features that were not originally presented in the builder, such as the hardcoded key. We were not able to attribute Black Kingdom to any known threat group.
Based on our telemetry, we could see only a few hits by Black Kingdom in Italy and Japan.
Gootkit: the cautious banking Trojan
Gootkit belongs to a class of Trojans that are extremely tenacious, but not widespread. Since it’s not very common, new versions of the Trojan may remain under the researchers’ radar for long periods.
It is complex multi-stage banking malware, which was initially discovered by Doctor Web in 2014. Initially, it was distributed via spam and exploits kits such as Spelevo and RIG. In conjunction with spam campaigns, the adversaries later switched to compromised websites where visitors are tricked into downloading the malware.
Gootkit is capable of stealing data from the browser, performing man-in-the-browser attacks, keylogging, taking screenshots, and lots of other malicious actions. The Trojan’s loader performs various virtual machine and sandbox checks and uses sophisticated persistence algorithms.
In 2019, Gootkit stopped operating after it experienced a data leak, but has been active again since November 2020. Most of the victims are located in EU countries such as Germany and Italy.
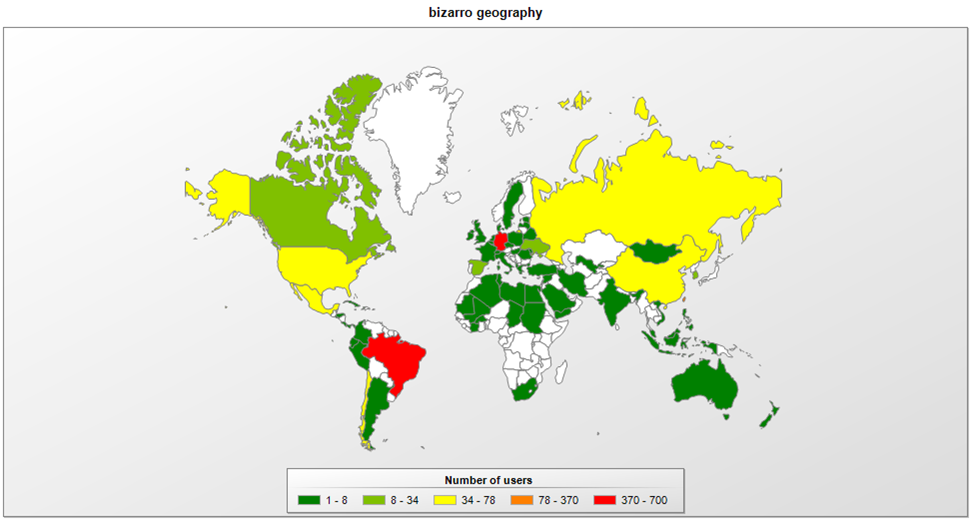
Bizarro banking Trojan expands into Europe
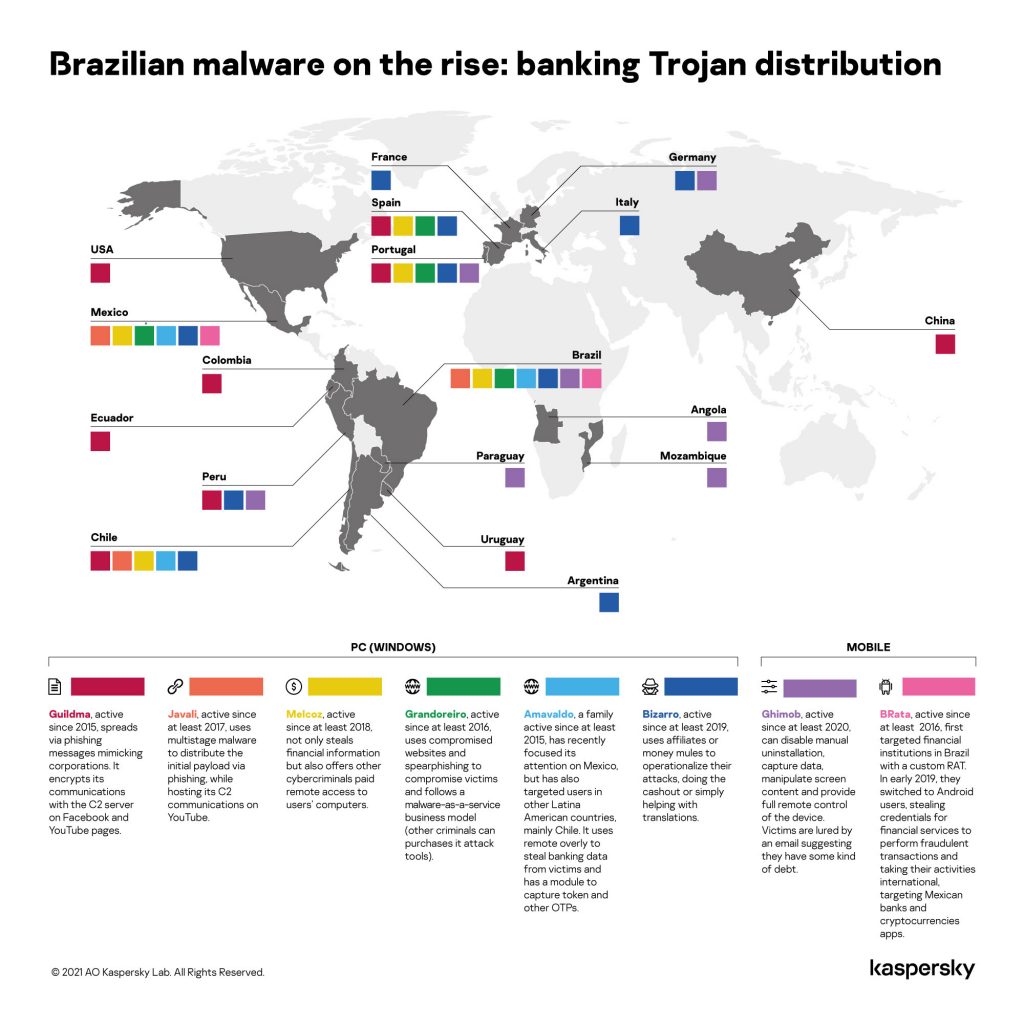
Bizarro is one more banking Trojan family originating from Brazil that is now found in other parts of the world. We have seen people being targeted in Spain, Portugal, France and Italy. This malware has been used to steal credentials from customers of 70 banks from different European and South American countries.
As with Tetrade, Bizarro uses affiliates or recruits money mules to cash out or simply to help with money transfers.
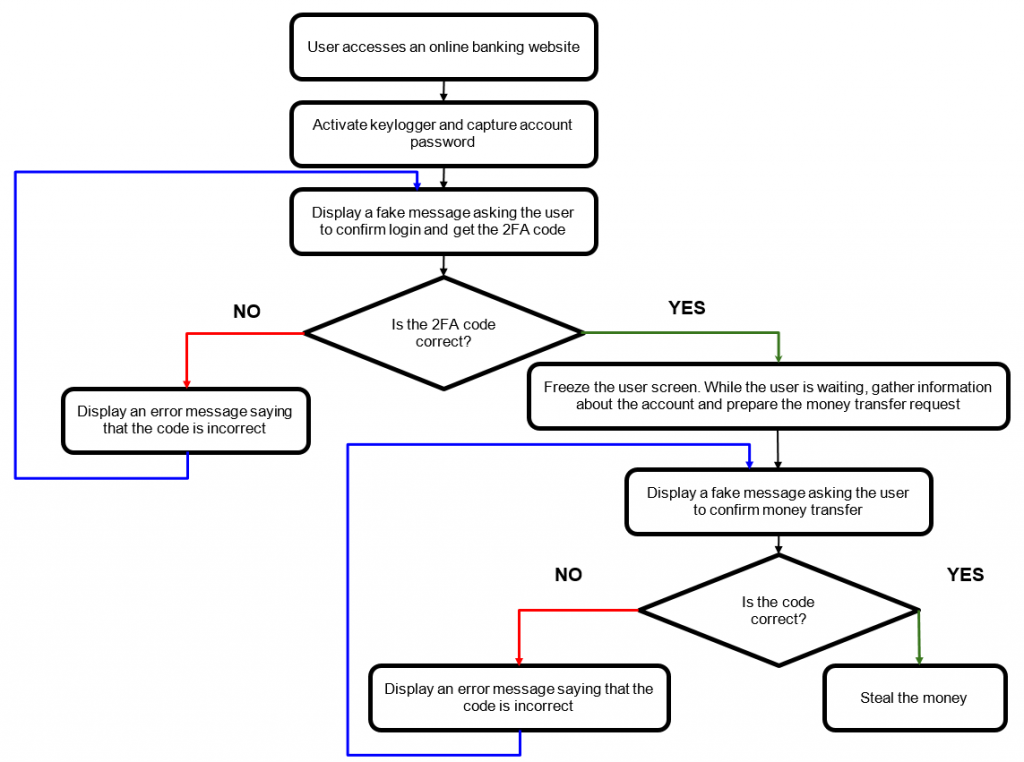
Bizarro is distributed via MSI packages downloaded by victims from links in spam emails. Once launched, it downloads a ZIP archive from a compromised website. We observed hacked WordPress, Amazon and Azure servers used by the Trojan for storing archives. The backdoor, which is the core component of Bizarro, contains more than 100 commands and allows the attackers to steal online banking account credentials. Most of the commands are used to display fake pop-up messages and seek to trick people into entering two-factor authentication codes. The Trojan may also use social engineering to convince victims to download a smartphone app.
Bizarro is one of several banking Trojans from South America that have extended their operations into other regions – mainly Europe. They include Guildma, Javali, Melcoz, Grandoreiro and Amavaldo.
Malicious code in APKPure app
In early April, we discovered malicious code in version 3.17.18 of the official client of the APKPure app store, a popular alternative source of Android apps. The incident seems to be similar to what happened with CamScanner, when the app’s developer implemented an adware SDK from an unverified source.
When launched, the embedded Trojan dropper, which our solutions detect as HEUR:Trojan-Dropper.AndroidOS.Triada.ap, unpacks and runs its payload, which is able to show ads on the lock screen, open browser tabs, collect information about the device, and download other malicious code. The Trojan downloaded depends on the version of Android and how recently security updates have been installed. In the case of relatively recent versions of the operating system (Android 8 or higher) it loads additional modules for the Triada Trojan. If the device is older (Android 6 or 7, and without security updates installed) it could be the xHelper Trojan.
We reported the issue to APKPure on April 8. APKPure acknowledged the problem the following day and, soon afterwards, posted a new version (3.17.19) that does not contain the malicious component.
Browser lockers
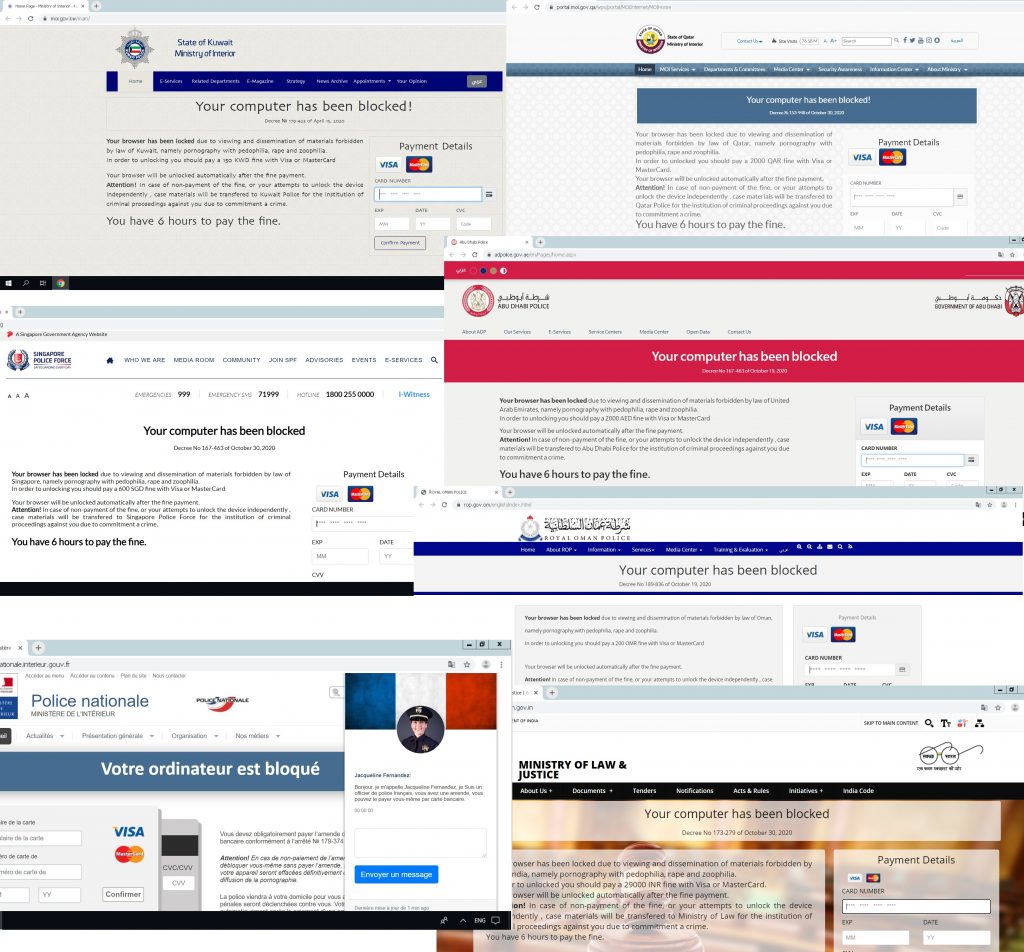
Browser lockers are designed to prevent the victim from using their browser unless they pay a ransom. The “locking” consists of preventing the victim from leaving the current tab, which displays intimidating messages, often with sound and visual effects. The locker tries to trick the victim into making a payment with threats of losing data or legal liability.
This type of fraud has long been on the radar of researchers, and over the last decade there have been numerous browser locking campaigns targeting people worldwide. The tricks used by the scammers include imitating the infamous “Blue Screen of Death” (BSOD) in the browser, false warnings about system errors or detected malware, threats to encrypt files and legal liability notices.
In our report on browser lockers, we examined two families of lockers that mimic government websites.
Both families spread mainly via advertising networks, primarily aimed at selling “adult” content and movies in an intrusive manner; for example, through tabs or windows that open on top of the visited site when loading a page with an embedded ad module (pop-ups), or after clicking anywhere on the page (click-unders).
These threats are not technically complex: they simply aim to create the illusion of having locked the computer and intimidate victims into paying money. Landing on such a page by mistake will not harm your device or compromise your data, as long as you don’t fall for the cybercriminals’ smoke-and-mirror tactics.
Malware targets Apple M1 chip
Last November, Apple unveiled its M1 chip. The new chip, which has replaced Intel processors in several of its products, is based on ARM architecture instead of the x86 architecture traditionally used in personal computers. This lays the foundation for Apple to switch completely to its own processors and unify its software under a single architecture. Unfortunately, just months after the release, malware writers had already adapted several malware families to the new processor.
Attempted supply-chain attack using PHP
In March, unknown attackers tried to carry out a supply-chain attack by introducing malicious code to the PHP scripting language. The developers of PHP make changes to the code using a common repository built on the GIT version control system. The attackers tried to add a backdoor to the code. Fortunately, a developer noticed something suspicious during a routine check. Had they not done so, the backdoor might have allowed attackers to run malicious code remotely on web servers, in around 80 per cent of which (web servers) PHP is used.
Article Link: IT threat evolution Q2 2021 | Securelist