Quick and Dirty way to unpacking SManager Chinese APT tool.

This blog is my last blog in series of Analysis of SManager. I had planned to write more blogs on unpacking for our infosec. community. Hope you like this one.
If you haven’t read my previous blogs on SManager Chinese APT Tool then go head and read them. I’m mentioning them in here.
It’s SManager Loader analysis:
It’s SManager analysis:
Reversing APT Tool : SManager (Unpacked)
Here we go for unpacking SManager Tool.
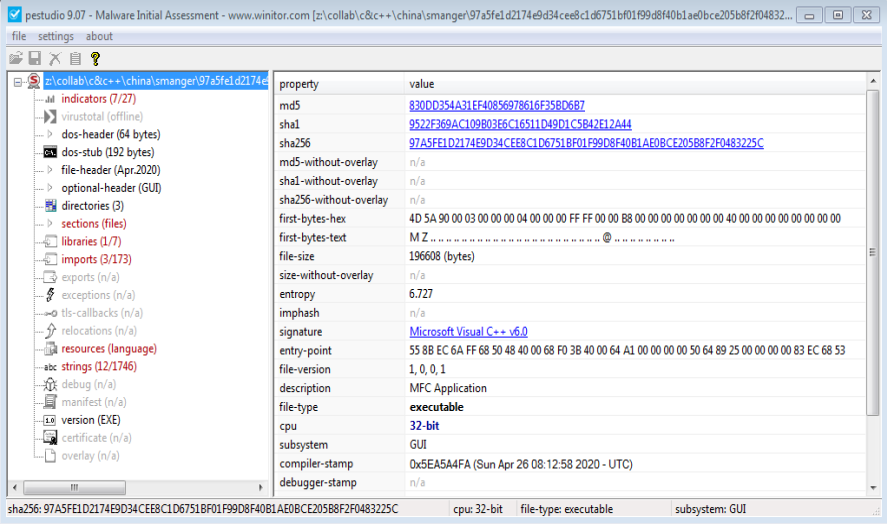
File Information:
Here look carefully, Entropy is high around 6.727. Its the 32bit malware loader which we have to hammer down to SManager executable.
Fire Up x32dbg & settling down it for debugging.
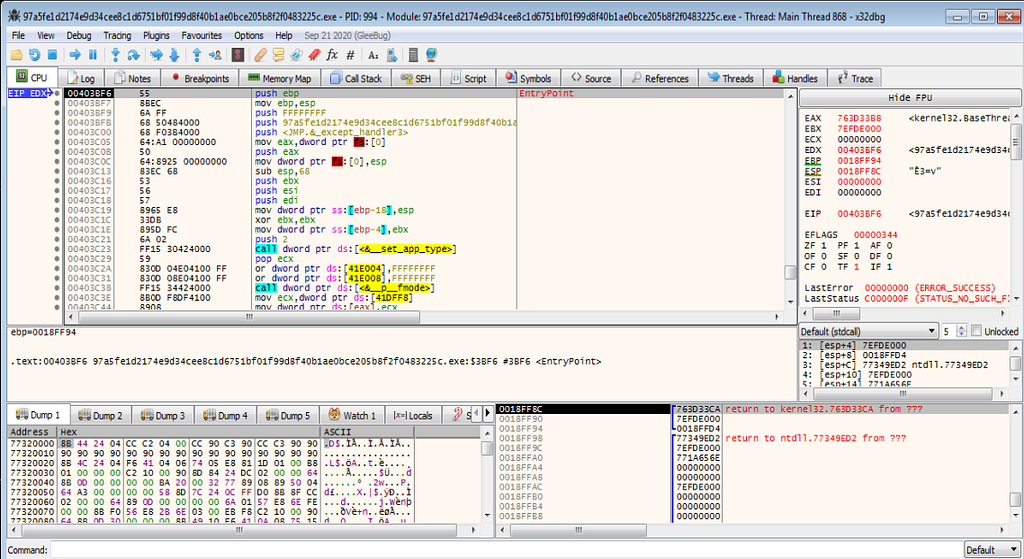 Look like x32dbg is being loaded up now.
Look like x32dbg is being loaded up now.Uncheck the System BreakPoints in Settings by going into the Options -> Preferences and save it.
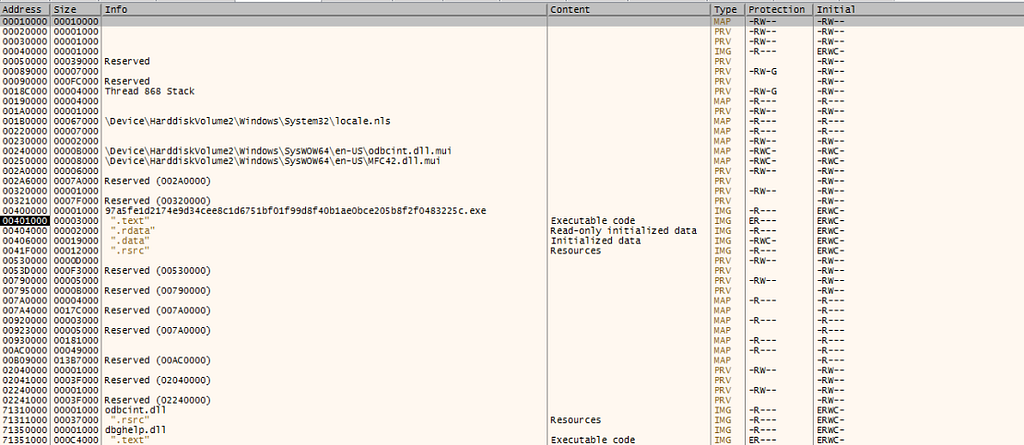 Memory Map is quiet useful for us in unpacking SO focus on that.
Memory Map is quiet useful for us in unpacking SO focus on that.Setting Up Breakpoints
Type in the command palate at the bottom of x32dbg for setting up breakpoints.
 Command Palate.
Command Palate.Format of typing will be like:
bp <_____________>
Example: bp VirtualAlloc .
Some for the process injection and some for the self injection.
….:- VirtualAlloc
…..:- VirtualProtect
…..:- ResumeThread
…..:- CreateProcessInternalW
…..:- WriteProcessMemory
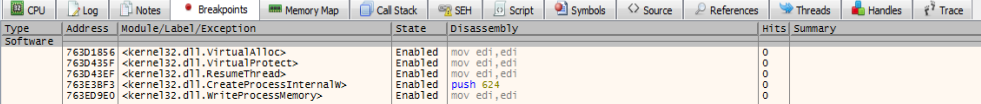 Breaking Points Setting Up.
Breaking Points Setting Up.Unpacking SManager
Click on “Run to User Code” from the tool icons present in just below of Menu Bar.
 Move the cursor above icons and what these tools icons does will be shown.
Move the cursor above icons and what these tools icons does will be shown.After that hit at the Run from this same tool bar shown above.
It will hit x32dbg at the “CreateProcessInternalW”.
 BreakPoint hits at the CreateProcessInternalW.
BreakPoint hits at the CreateProcessInternalW.Hit Run again after that. And now you will be see that “ResumeThread” will be hit.
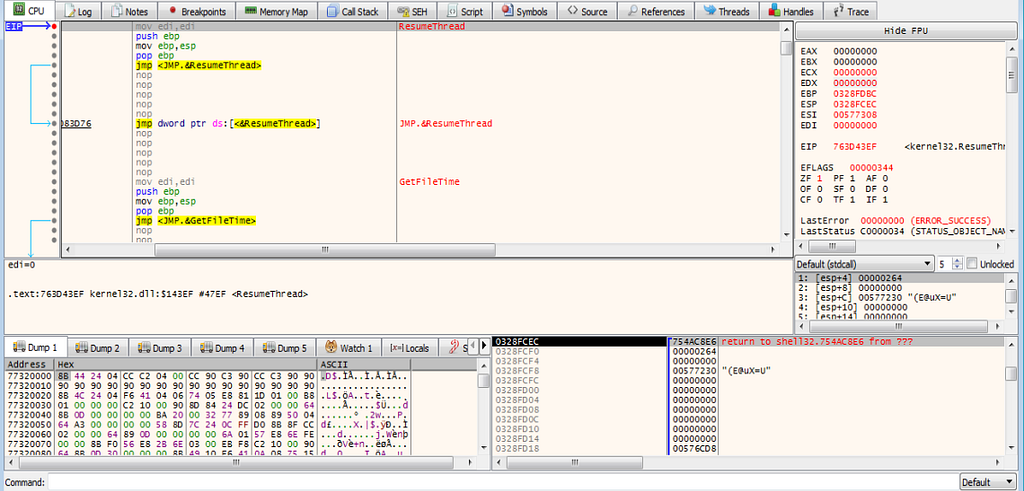 BreakPoint hits at the ResumeThread.
BreakPoint hits at the ResumeThread.Hit the Run again & this time also x32dbg will also be hit at the CreateProcessInternalW.
This hit is useful. See Carefully and focus.
We got the SManager unpacked binary location on disk.
 SManager Executable is the %temp% directory.
SManager Executable is the %temp% directory. Locating SManager binary by typing %temp%.
Locating SManager binary by typing %temp%.Checking Up the Proper Executable
Fire Up PE Studio.
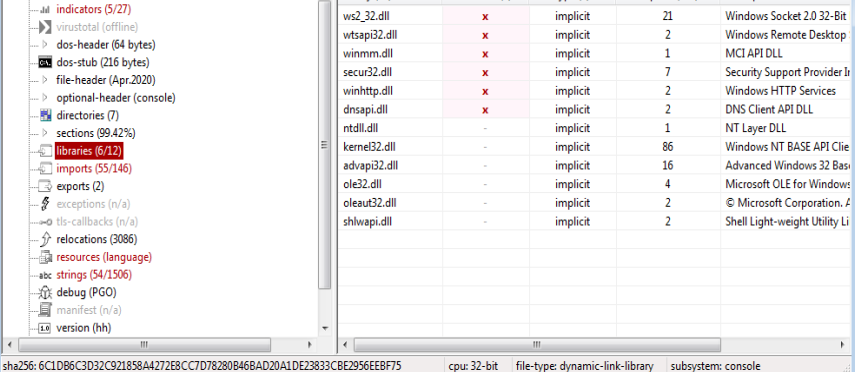 PE Studio View of SManager Library.
PE Studio View of SManager Library.Fire Up PE Bear.
 PE Bear View of SManager.
PE Bear View of SManager.Reference for Tools:
x32dbg , PEStudio, PEBear.
Thank you for reading.
Article Link: https://medium.com/@0xthreatintel/how-to-unpack-smanager-apt-tool-cb5909819214?source=rss-a15183055fd6------2