Goblin Panda changes the dropper and reuses the old infrastructure
I found a new dropper c580d77722d85238ed76689a17b0205b4d980c010bef9616b8611ffba21b142e with the same signature of others. But it changes the exploitation. Before, it uses the ole package to drop a 8.t file in %appdata% and decode two files, a legit file and an backdoor (PlugX, newcore rat, sysfader…).
Now it’s a big object ole mapped in memory and one PE is used to drop the files.
RTF exploit
Now we have four object oles in the RTF.
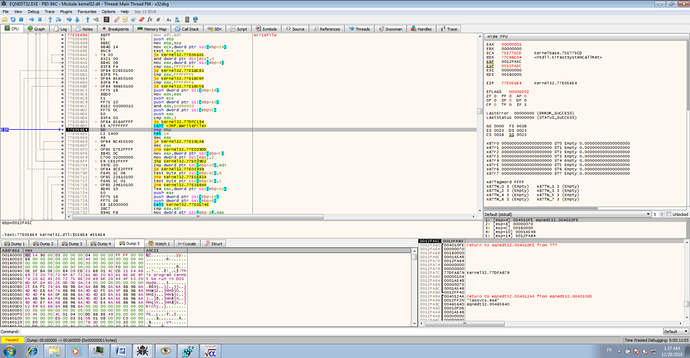
this RTF exploits again the CVE-2017_1882 on eqnedt32.exe.
The biggest object is a new exe to overwritten the first eqnedt32.exe . This PE is decoded by the shellcode of the exploit and executes this PE.
It’s the same algorithm of the exploit targeting Vietnam.
Just the init key has changed.
Dropper
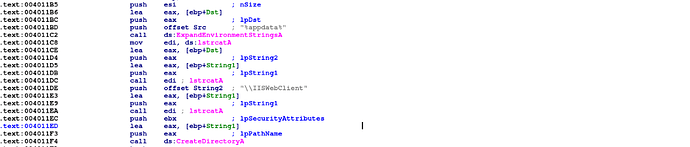
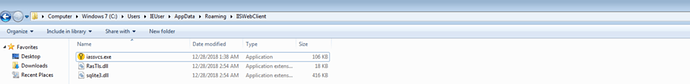
the PE creates a directory in %appdata% named IISWebClient
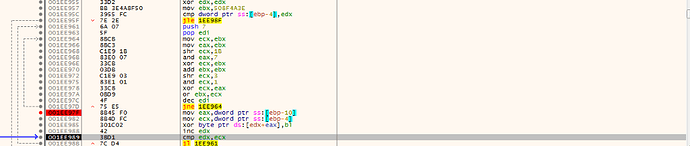
After, it decrypt a buffer in the address space of the executable with a xor.
After the decoding, the PE decompresses and drops three files on the disk: iassvcs.exe developed and signed by Symantec, sqlite3.dll signed by the av 360 and RasTls.dll the backdoor.
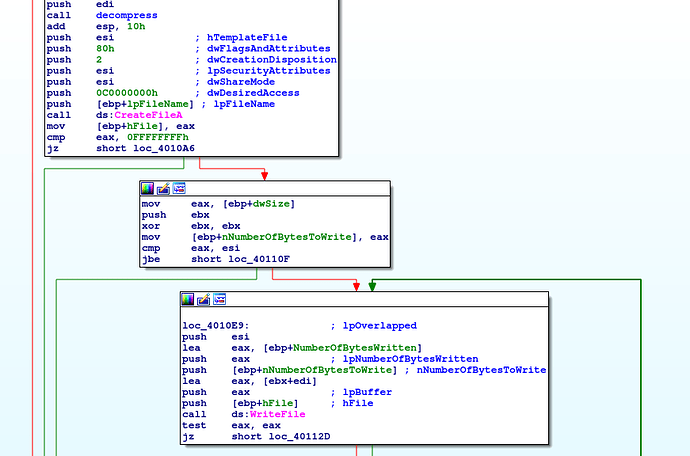
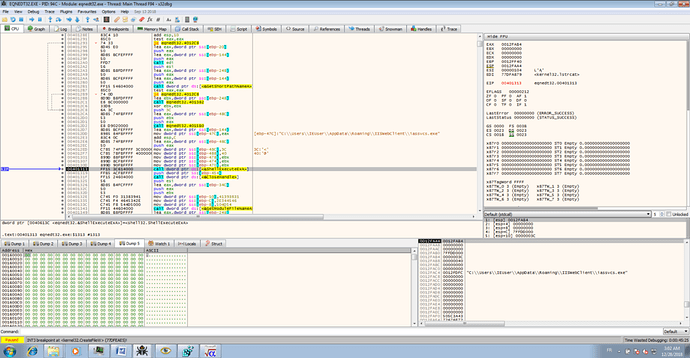
The first step is to call dropfile
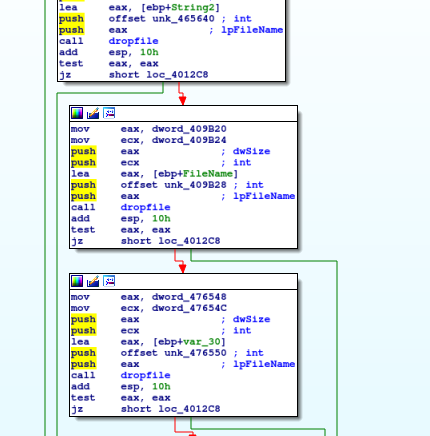
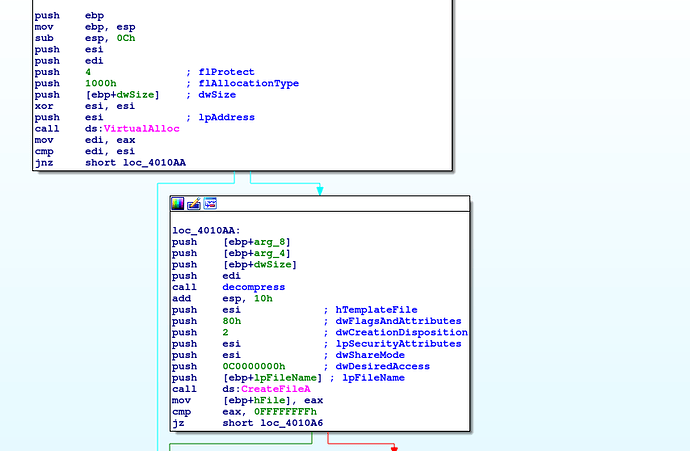
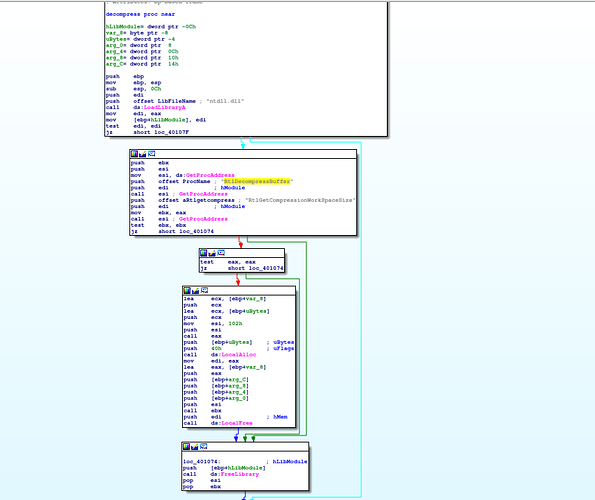
In this function the first step is to allocate at 0016000 a memory page and to decompress the file before writing on the disk.
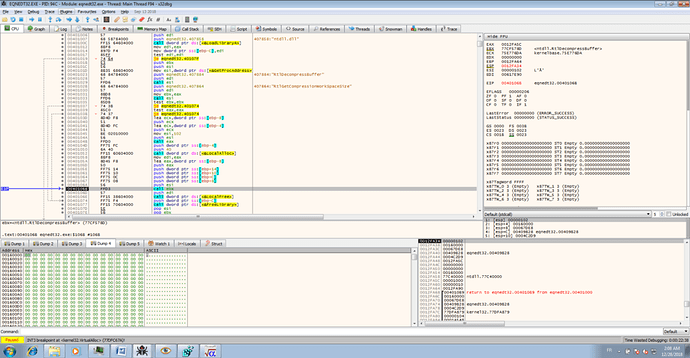
the function decompress loads dynamically the function RtlDecompressBuffer and use it.
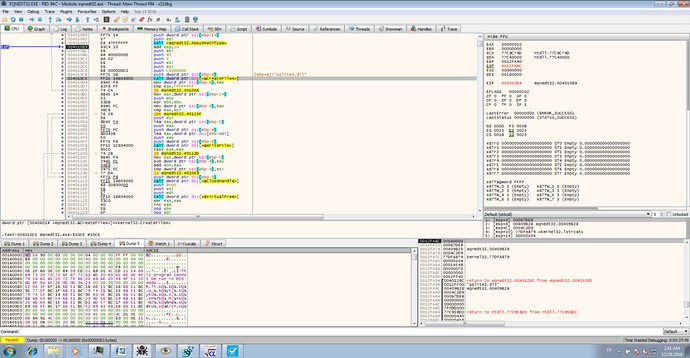
In the debugger, theses steps are:
CreateFileDecompressWrite the buffer on the disk after decompressingAnd the dropper execute the iassvcs.exe to make a side loading and make the persistence.
at each executable or cmd line, the executable is reloaded.
In a second part, I’ll analysed the backdoor.
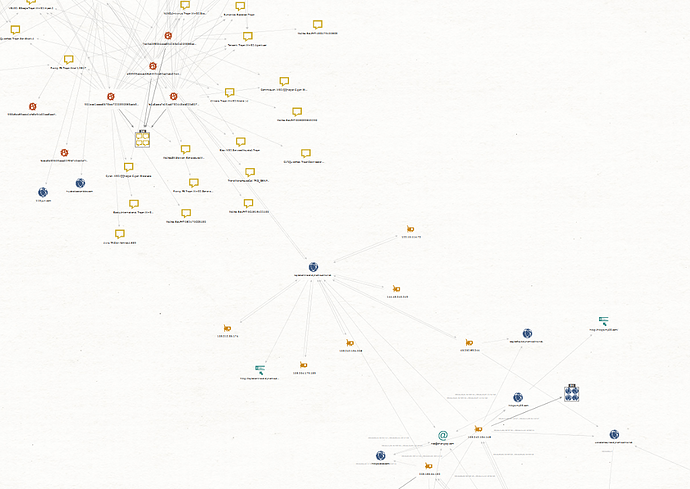
Threat Intelligence
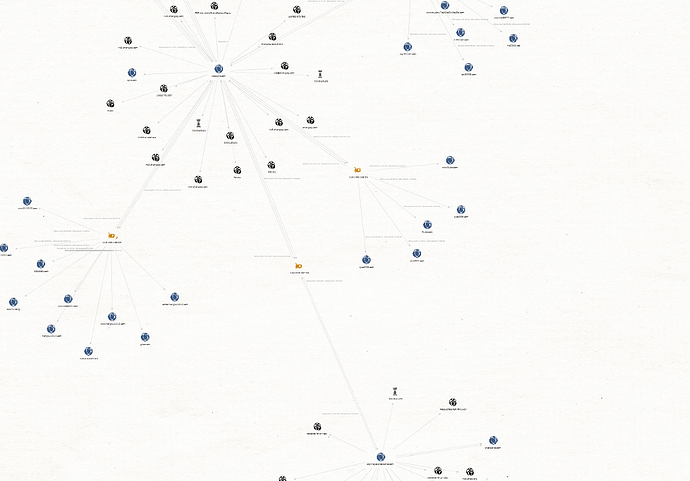
the backdoor contacts hxxps://skylineqaz.crabdance.com/
the domain resolves 154.223.167.20. This IP is very interesting because it connects with tele.zyns.com and old infrastructures used by chinese APT or DDOS Chinese team against the ancient soviet republics.
Also, the name of domains show the targets is energy and telecom sectors.
they find uzwatersource.dynamic-dns.net used by Icefog connected by the 150.129.80.184 to tele.zyns.com
uzwatersource.dynamic-dns.net connects to tajikstantravel.dynamic-dns.net by 45.252.63.244.
The domain tajikstantravel.dynamic-dns.net connected to ddos infrastructure chinese.
Another thing is the dropper what has submitted by an ID coming of the Kazakhstan. So Goblin Panda targets it ?
IOCs
the dropper:
dropper “c580d77722d85238ed76689a17b0205b4d980c010bef9616b8611ffba21b142e”
sha256 c580d77722d85238ed76689a17b0205b4d980c010bef9616b8611ffba21b142e
sha1 398fb04ce9b2e30bce932590e0b86b594c8a97ea
md5 30528dc0c1e123dff51f40301cc03204
Dropped executable file
sha256 C:\Users\admin\AppData\Roaming\IISWebClient\RasTls.dll eb0b848f18d8002aaf59faca18b28941df67dc46891868b96fa4daf03018d148
sha256 C:\Users\admin\AppData\Roaming\IISWebClient\iassvcs.exe f9ebf6aeb3f0fb0c29bd8f3d652476cd1fe8bd9a0c11cb15c43de33bbce0bf68
sha256 C:\Users\admin\AppData\Roaming\IISWebClient\sqlite3.dll e342eefb43249a3a1b62b8622f7c94fc391c0488bdae7e1909e37cb125029f1c
DNS requests
domain skylineqaz.crabdance.com
domain xn — ylineqaz-y25ja.crabdance.com
Connections
ip 154.223.167.20
HTTP/HTTPS requests
url https://skylineqaz.crabdance.com/
tele.zyns.com 103.242.134.146 150.129.80.184 ( Goblin Panda, Icefog)
uzwatersource.dynamic-dns.net 150.129.80.184 (Icefog)