It’s no secret that there’s a gender gap in the tech industry. Only 20% of tech jobs in the U.S. are held by women despite women making up more than half the workforce. In addition, women hold a lower share of computer science jobs than they did in the 1980s. With a predicted 3.5 million job openings expected in the cybersecurity industry by 2021, this is an industry that women should be informed about.
One issue that is deterring women from entering the cybersecurity field is a lack of programs and education offered. A study showed that 52% of females felt that no cybersecurity programs or activities were offered to them while only 39% of male respondents felt the same way.
Teaching STEM to Girls
To help bridge this gap, action should be taken to start teaching these STEM topics to girls at a young age. Recently, The Girl Scouts have mirrored this belief and taken steps to promote STEM activities within their framework. They specifically focus on cybersecurity and plan to introduce a series of 18 cybersecurity badges.
The Boy Scouts have had the cyber chip since 2012, which promotes Internet safety. To earn this award, the member must read about Internet safety, sign an Internet safety pledge and give a lesson to their troop about safe Internet practices. However, the Girl Scouts only recently created a set of cybersecurity badges that will teach young girls how computers and the Internet work. They will then apply concepts of safety and protection to their everyday technology use.
Other organizations such as Girls Who Code and Girls Go Cyberstart are working to close this gender gap as well by teaching cybersecurity skills and encouraging girls to create a network within the tech field.
10 Cybersecurity Lessons to Teach Kids
Whether you’re the parent of a Girl Scout who is working toward the cybersecurity badge or want to teach your daughter about the importance of cybersecurity, we have tips and tricks to help you teach them how computers work and how to stay safe online. Each lesson also includes an activity that should be suitable for all ages.
1. Finding Out How Computers Read Information
Computers read information similarly to how humans read books, but they have their own language. This language is called binary code and instead of a 26 letter alphabet, it uses two numbers: 0 and 1. Different patterns of these numbers will spell out different instructions for the computer to follow.
Activity: Binary Code Name Tags
To help kids understand binary code, we have an exercise that will let them put it into practice. Take a look at the UTF-8 binary code and use it to create a name tag.
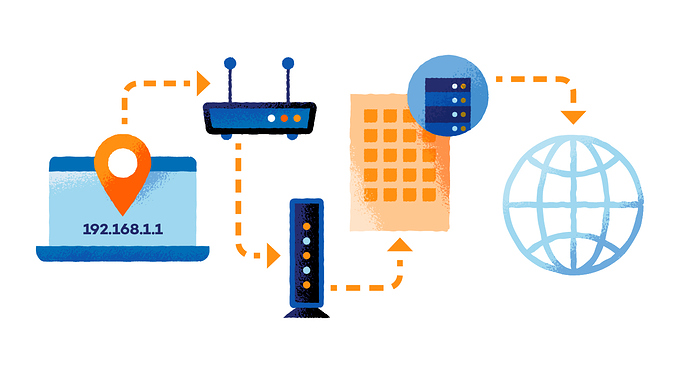
2. Discover How Networks Work
Electronic devices such as desktop computers, laptops, tablets and smartphones are all linked together on a network. To understand what a network is, it may be helpful to learn the right vocabulary.
- IP address: This is an identification number that’s assigned to each electronic device.
- Router: This is a networking device that is in the form of a small box. It connects all your electronic devices in one place and allows them to join the same network.
- Modem: This is a device that provides access to the Internet.
- Internet Service Provider (ISP): This is a company that provides your Internet service.
- Internet: This is a worldwide system of computer networks.
For more clarity, Khan Academy has a video series on how the Internet works.
Activity: Network Scavenger Hunt
To understand these pieces of the network puzzle, have kids find the following:
- Find the IP address of your device. You can find your public IP address by Googling “what is my IP address.”
- Find where your WiFi router is located in your house.
- Find out the name of your Internet service provider. Compare with your friends in other neighborhoods to see if they have the same one.
3. Find Out What Protocols Are And How to Create One
A protocol is a procedure or a system of rules that explain how something should be done. For example, a stop light has three colors. We have decided that red means stop, yellow means slow and green means go. When we see these colors, we know what action to take. When computers share data, they also have a set of rules or protocols that they follow.
Activity: Identifying Protocols Throughout the Day
Discuss what a protocol is and then have kids focus on protocols throughout their day. When they identify one, have them write it down. Then discuss what they found and how they help our society run.
4. Explore Computer Communication Protocols
When you meet someone, you shake their hand to introduce yourself. The same thing happens when the computer’s host is connecting with the server. This handshake has a three-step protocol.
Step 1: A request is sent out.
Step 2: The request is received and interpreted.
Step 3: The request is accepted and the message can be sent.
Activity: Act It Out
Create a scenario where two people act out the computer handshake. Person #1 is the computer’s host. Person #2 is the server. Person #1 makes a paper airplane. They then must try to throw the paper airplane at person #2 who is across the room to get their attention. Once the plane hits (or catches their attention), person #2 can receive the paper airplane and understand that person #1 wants their attention. Person #1 notices that they now have person #2’s attention and can start a conversation.
5. Find Out What Malware Is
Malware is software that is harmful to electronic devices. Its name comes from the words “malicious” and “software.” There are many different types of malware, including:
- Viruses
- Worms
- Trojan horse
- Spyware
- Adware
- Ransomware
Activity: Word and Definition Pairing
Download this word and definition pairing activity to find out if they know what each term means. Then discuss the terms, which one they think is most threatening and if they have ever experienced or heard of any of these happening.
6. Create and Protect a Username
When you create a profile or account on an application, you are usually required to make a username. Do you usually use your real name? Creating a unique username that is not your real name is a good way to protect your identity. This way strangers online won’t know who you are.
Activity: Uncovering Usernames
Have the kids write down the usernames they use. Discuss if these usernames protect their identity. Create a list of new usernames that they can change them to if necessary.
7. Create and Protect a Password
Password protection is something everyone, not just kids, struggles with. It’s important to teach kids the importance of choosing a password that will keep their accounts safe.
When making a password, they should keep these tips in mind:
- Use at least 8 characters (14 is best!).
- Use a variety of numbers, letters (lower and upper case) and symbols.
- Don’t use predictable capitalization. Instead of just capitalizing the first letter, scatter capitalization throughout.
- Don’t use the same password for multiple accounts.
- Don’t use your name or anyone else’s name.
- Don’t use words from the dictionary.
- If you can’t come up with a good password, use a secure password generator.
- Change your password every 10 weeks.
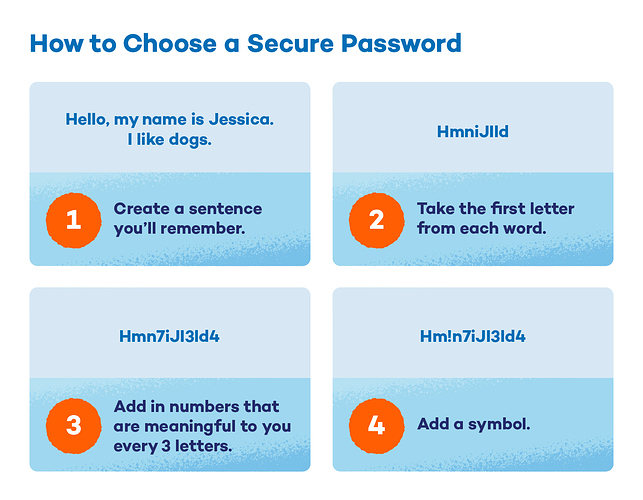
Activity: Creating Secure Passwords You’ll Remember
To teach kids how to make secure passwords that they will remember, start with a sentence they will remember.
Ex: Hello, my name is Jessica. I like dogs.
Then take the first letter from each word.
Ex: HmniJIld
Then add in numbers that are memorable to you every 3 letters. For this example, let’s say Jessica’s address is 734.
Ex: Hmn7iJI3ld4
Lastly, add in a symbol.
Ex: Hm!n7iJI3ld4
This will create a secure password that can be remembered later on. Practice creating this type of password. If you have trouble remembering passwords, it can also be helpful to have a password manager on your device.
8. Discover How You Share Information and What to Share
Kids should learn and understand the importance of being selective about what they share online. You wouldn’t tell a stranger on the street personal information (like where you live or go to school) and the same goes for strangers online.
Some of these strangers online are actually hackers, posing to be someone else. A hacker uses their computer skills to solve a problem with technology. Hackers can use this skill for good, to find weaknesses in a system and fix or protect them. On the other hand, there are bad hackers who are criminals that will use this skill to find out information about someone and use it against them.
Activity: Think Like A Hacker
To help kids understand the information they are sharing, have them analyze their own social media through the eyes of a hacker. If they don’t have a social media account, try looking at a friend or family members.

9. Information Online Lasts Forever
Information that you post online lasts forever. Even if you delete a post or a photo, the information is stored on the cloud and can be found. This means that every time you post online, you are adding to your digital footprint.
Activity: What Does Your Digital Footprint Look Like?
To help kids understand their digital footprint, have them Google themselves to see what comes up. Discuss if they would be embarrassed if their grandparents, teachers, future college or future employer saw what came up.
10. Who Can You Trust Online?
Not everyone online is who they say they are. It’s easy for someone to hide behind a screen. For example, if you receive an email saying that you won a prize, there’s a good chance it’s someone pretending to be the company. If you click on this type of email it could infect your device with malware or the person could steal your personal information.
Activity: Do You Know Who To Trust Online Quiz
To teach kids about who they can trust online, discuss the warning signs of a suspicious email.
Some warning signs to look out for:
- You don’t recognize the sender name
- The subject line looks like spam
- It doesn’t address you by name and instead uses a vague introduction like “Dear customer”
- It’s offering something that’s too good to be true
- There are grammatical errors
- It’s asking for personal information like your full name, phone number or address
- There is a suspicious link in the email (don’t click it!)
To help solidify the understanding of these warning signs, have them take an online safety quiz.
These lessons and activities are ones that we should be teaching from a young age. Once you go over them with your daughter, pass them on to friends, family or your school to help increase safe technology use and encourage women to pursue a career in cybersecurity. For an extra layer of protection on your computer, check out Panda Security’s Panda Dome, an antivirus to help protect your family’s digital life.
The post Girls in Tech: 10 Cybersecurity Lessons to Teach Kids appeared first on Panda Security Mediacenter.
Article Link: https://www.pandasecurity.com/mediacenter/technology/girls-in-tech/