Cloud first has been the official U.S. federal government strategy since the early 2000s. Since then, agencies have been adopting cloud for many of the same reasons as their commercial counterparts. However, when it comes to securing hybrid and public federal clouds, agencies have historically relied upon an abundance of people and point products. This is problematic at cloud scale – more people and dozens of point products simply do not work.
In response to this challenge, I am excited to announce that Prisma Cloud has been added to Palo Alto Networks Government Cloud Services, which has achieved the designation of “In Process” for the Federal Risk and Authorization Management Program (FedRAMP).
This important milestone will help U.S. government agencies securely adopt public and hybrid cloud by eliminating complexity and delivering consistent security and compliance controls across the entire cloud native technology stack and software development lifecycle.
Stronger Together
Over the past two years, Palo Alto Networks has strengthened its cloud security portfolio by acquiring several industry-leading cloud security companies. These include:
| Product | Key capabilities | DHS Continuous Diagnostics and Mitigation (CDM) Mapping |
| Evident.io | API-based cloud security and compliance |
|
| RedLock | API-based cloud threat detection and response |
|
| Twistlock | Container security and compliance |
|
| PureSec | Serverless security |
|
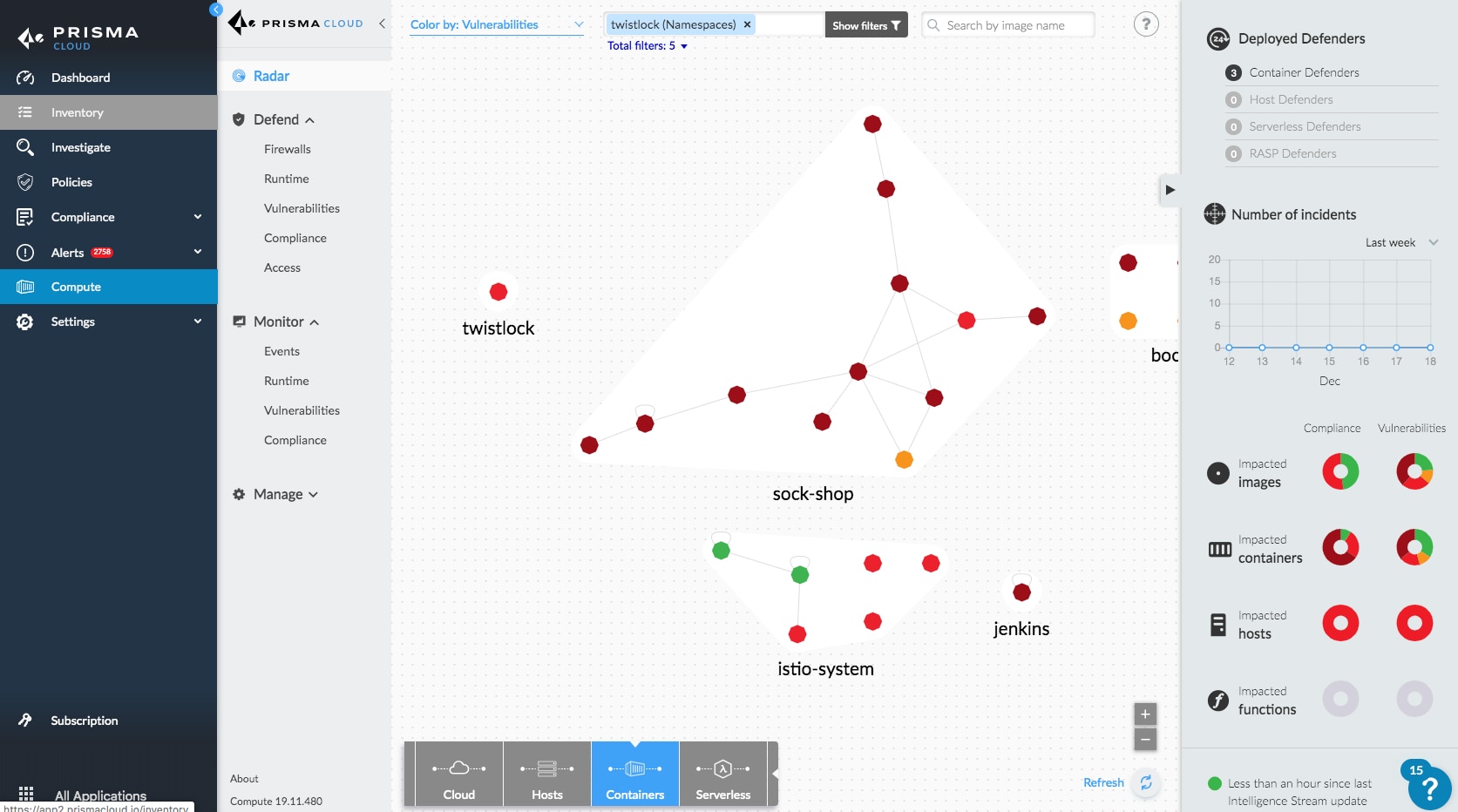
Figure Z – Unified Prisma Cloud Enterprise dashboard
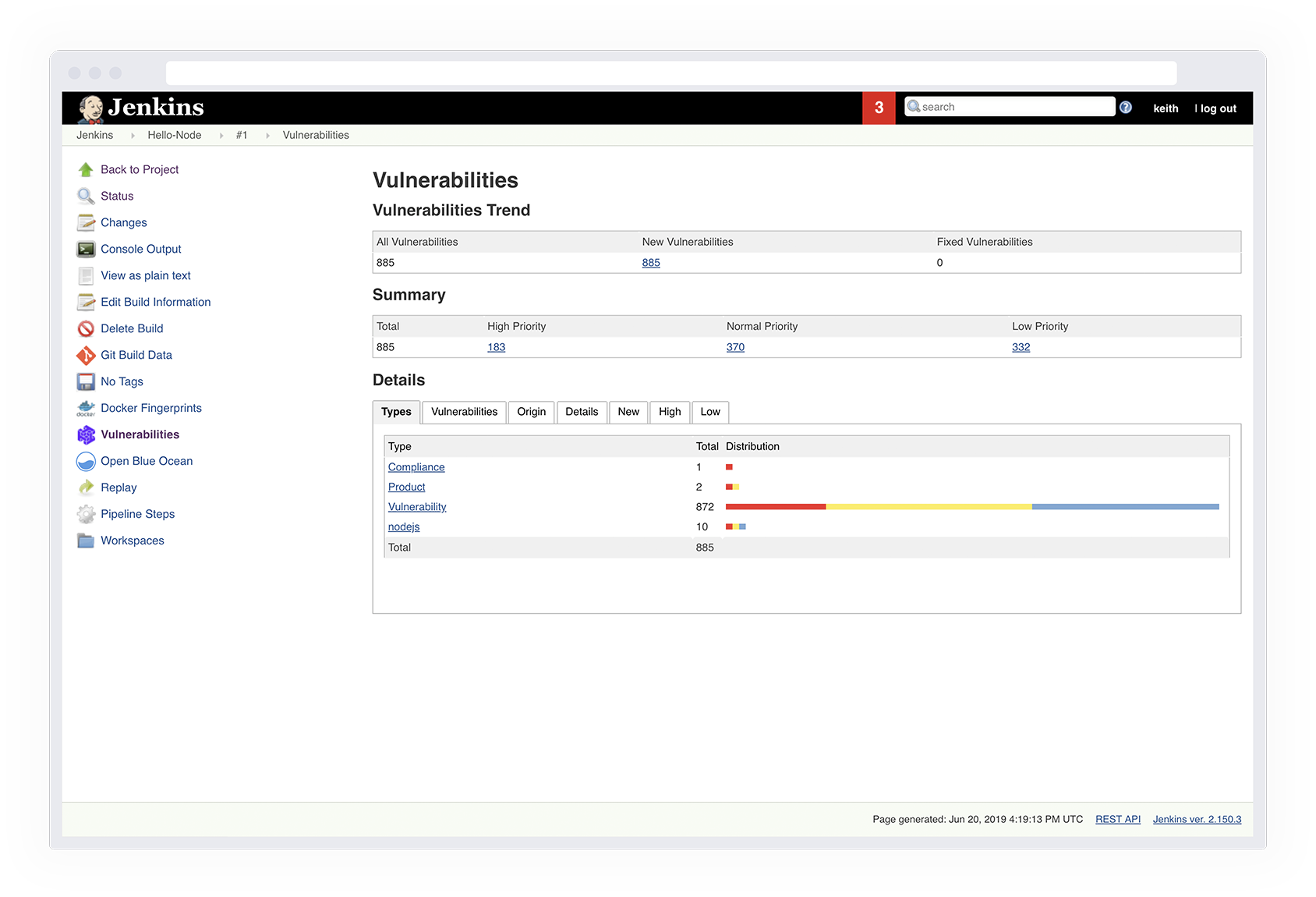
All of the above technologies have been integrated into a unified cloud native security platform, Prisma Cloud. Building on this good news is that many government organizations are already benefiting from Prisma capabilities today. They are implementing VM-Series virtual firewalls, Twistlock and PureSec (now Prisma Cloud Compute Edition, part of Prisma Cloud) to secure network traffic, protect containers and serverless functions and enable DevSecOps. Agencies who use Agile software development practices have integrated Prisma Cloud Compute Edition into their continuous integration workflows to find and fix security problems before they ever make it into production. These powerful capabilities allow developers to see vulnerability status every time they run a build (Figure X), without having to run a separate tool or use a different interface. Security teams can set policies that act as quality control gates to ensure only remediated images progress down the pipeline into production.
Figure X – Prisma Cloud Compute Edition securing the C/CD pipeline
Flexible Deployment Options
Prisma Cloud Cloud Compute Edition has the flexibility to run locally in Federal data centers and/or in any tenant of the major cloud platforms including Alibaba, Azure, GCP and AWS. This also means that data sovereignty issues are typically not in play as the platforms can be installed by customers directly in their cloud tenant. When combined with VM-Series virtual firewalls, agencies are able to reap the benefits of Prisma Cloud today while the cloud-delivered service works toward a FedRAMP Moderate Agency Authorization.
| Platform | FedRAMP Applicable? | Data Sovereignty | SaaS Option? |
| Prisma Cloud Enterprise Edition (formerly RedLock, Evident, Twistlock and PureSec) | Yes | Ability to run in specific regions | Yes |
| Prisma Cloud Compute Edition (formerly Twistlock and PureSec) | No | Ability to run on-premises or in any cloud tenant | Yes, Prisma Cloud Enterprise |
| VM-Series virtual firewalls | No | Ability to run on-premises or in any cloud tenant | No |
With Palo Alto Networks cloud capabilities, agencies can achieve their missions while improving their cyber resilience with a preventive approach, accelerated incident response and better management of the increasing volume, variety and velocity of cyberattacks across cloud environments.
Learn more about how Palo Alto Networks and its cloud products, including Prisma Cloud, can help secure federal networks.
The post Getting Cloud Smart: Security for Hybrid and Public Federal Clouds appeared first on Palo Alto Networks Blog.
Article Link: http://feedproxy.google.com/~r/PaloAltoNetworks/~3/1vQB1fulE7k/