
Several German DAX companies were spied on by a hacker group called WinNTI in mid-2019. The German Federal Office for the Protection of the Constitution (BfV) assumes that the German industry will be an attractive target for ongoing waves of attacks.
In December 2019, the BfV published a Cyber Brief with hints on current attack campaigns and sent it to many German industrial companies, discussing the facts and explaining a technical analysis of the WinNTI approach.
How can Panda Adaptive Defense 360 (AD 360) help with certain attack scenarios?
We will answer you some questions which refer to the potential attack campaigns indicated by the BfV.
- How is an Unknown Dropper classified in a process chain?
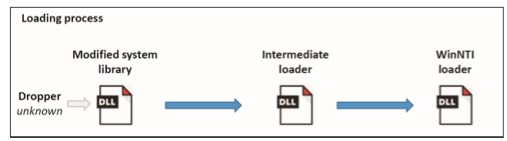
AD360 does not recognize the process as trustworthy, and therefore automatically keeps track of its execution. Whether a process is malicious or not depends on the examination of the source code. With AD360, the process is classified as “malicious” and the attack is already blocked.
- In case an advanced dropper was not stopped before: Is AD360 then able to stop the malware loading process?
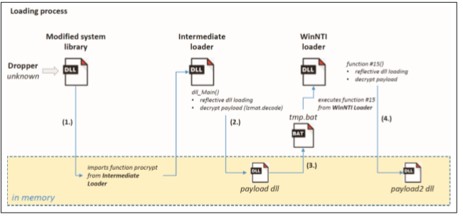
At this advanced stage, AD360 would become active again. Since, as shown in the figure above, the process “payload.dll” is unknown again because it has been changed. AD360 will automatically block it. The tmp.bat is also unknown and is blocked by AD360.
- How would Panda deal with the modified Payload2 dll variant (Figure 3 of the BfV cyber letter)?
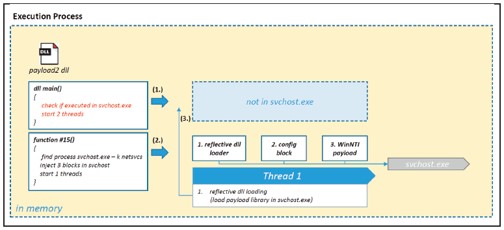
This step of the execution process is completely obsolete, since payload.dll was already recorded in the previous step. The listed “reflective dll loading” shell code (shown in the figure under (3.)) is subjected to a source code check.
- Does this also mean that the following attack of the kernel driver is no longer applicable (Figure 7 of the Cyber letter of the BfV)?
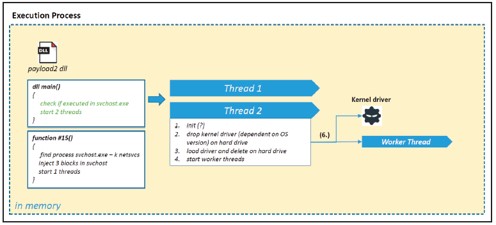
The attack described in the Cyber Brief in Figure 7, is a similar approach to Meltdown or Spectre as described in 2018. Here, the process execution would also be monitored and blocked.
- How can Panda protect against MITRE ATT&CK?
Currently, Panda Adaptive Defense knows about 20,000 different attack patterns. At the beginning of April 2020, AD will be developed further by including the Yara rules.
Conclusion
Panda Adaptive Defense already scans all processes automatically and blocks them until they are classified as “trusted” or removes those interactions that have been classified as “malicious”. Approved processes continue to be monitored in real time (dynamic exploit protection) and will be blocked if a “malicious” behavior is classified.
Traditional antivirus programs are unable to detect the dropper, as no file-based malware files are required. The attack is carried out almost entirely using Windows applications or files that have been certified as Windows native files by mistake. Many antivirus solutions only touch operating system files marginally or even not at all in order to prevent them from disturbing the running operating process.
The post German commercial companies in hacker focus – Panda protects you appeared first on Panda Security Mediacenter.
Article Link: https://www.pandasecurity.com/mediacenter/business/german-companies-hacker-focus/