Phishing is one of the main cybersecurity threats targeting Internet users. Today we will describe how these attacks work and how not to become a victim.
Emails from trusted companies
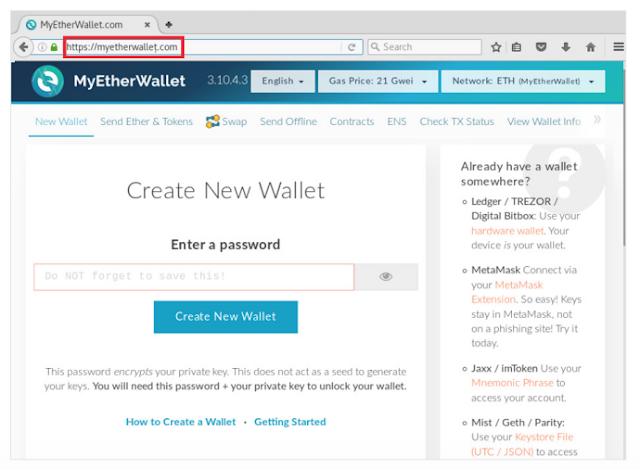
Attackers often target customers of a particular company. They impersonate that company and reach out to its customers, asking them to click a link to a fake website, where they are tricked into entering their credentials.In the case of financial services, hackers can steal money from victims' accounts. Such attacks are conducted regularly. For example: in one all too typical case a few years back, attackers hit users of MyEtherWallet, a popular cryptocurrency wallet. Users received an email that accounts were blocked due to a software update, and therefore must click a link to regain access.
Trusting users landed on a website identical to the original myetherwallet.com. The only difference was that the last letter "t" in the URL had been replaced by a visually similar Unicode character ("ţ").
Such a tiny detail does not usually catch the eye, so one must always stay vigilant. Even if a message seems to come from a company you know, be careful about clicking links. If you have any doubt about whether an email is legitimate, contact the company right away via a phone number or email address indicated on the official website. And if you need to go to a page often, bookmark it instead of accessing it via email links.
Attacks via corporate email
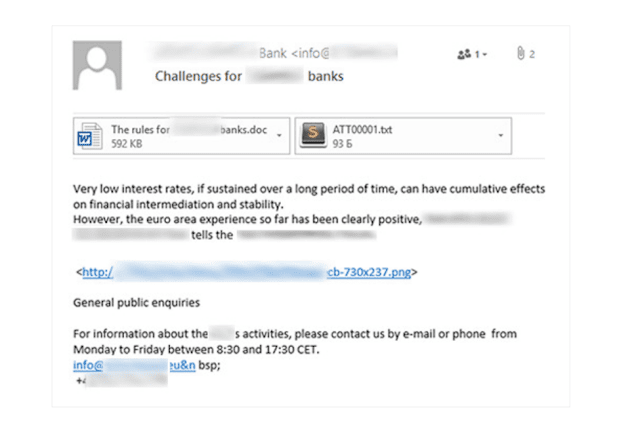
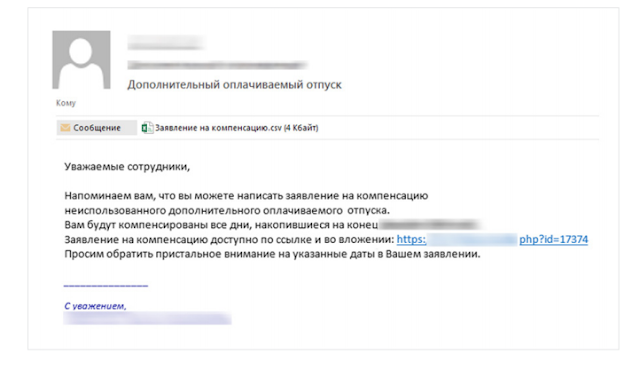
Fake domains are a simple and effective tool for phishing. However, criminals keep inventing more sophisticated techniques. One of them is to use employee email addresses to conduct attacks. In such cases, hackers usually are targeting an entire organization. To gain a foothold on a company's infrastructure, they might send emails posing as contractors or colleagues.They spice up messages with enticing subject lines—"bonuses," "reward," "wage increase," "vacation"—to immediately catch the attention of employees, who then download malicious attached files.
The Cobalt3 group has used such phishing messages as an initial vector in attacks on infrastructure. In some cases, messages were sent from the addresses of employees of real banks and integrators, whose infrastructure had been hacked. The messages usually came during working hours and looked quite credible.
In order not to fall victim to such attacks and prevent attackers from entering a company's network, employees should think twice before opening each message. Are you supposed to receive lists of employees' wages? Why did you get this message? If in doubt, do not download the attached file—instead, show it to an IT or security specialist.
Attacks on social media profiles
Email is not the only way in for attackers, who increasingly target social media profiles. Social networks enable attackers to reach out to employees of a target company. If hackers manage to infect a device from which a victim connects to corporate Wi-Fi, they will be able to penetrate the corporate network.Users with poor security awareness may use social networks to discuss business issues or even send sensitive documents. Even worse, employees sometimes use the same (or very similar) password for social networks and their work accounts.
This has worked to the advantage of the SongXY group, which participated in attacks against industrial companies and government institutions in CIS countries in 2017. The attackers surfed social networks for profiles of employees and sent messages to them.
A security assessment by Positive Technologies revealed that over 70 percent of tested employees responded to emails from potential attackers, and 21 percent followed unsafe links.
Social networks should not be used to discuss work issues, especially with strangers. Neither are they a good place to send or receive sensitive files.
Phone phishing
Hackers do not limit themselves to just the Internet when attacking home users and employees. Phone conversations remain one of the simplest, tried-and-true instruments for social engineering.The Internet is full of stories about clients who were called by someone supposedly from their bank, who tricked them into revealing their account credentials or a one-time code from an SMS message.
On occasion, office employees receive calls from "technical support staff" who request credentials used to access various programs or persuade the employees to open malicious links. A classic example: an attacker calls early Sunday morning and offers the employee a choice. Something has gone wrong, so the employee must either come to the office ASAP or simply give the username and password to the caller so the "support staff" can deal with the issue on their own.
By catching victims unaware and taking advantage of their momentary confusion, an attacker can obtain information of interest or trick users into performing certain actions. It is vital to remember that such attacks can and do happen. Do not rush to follow instructions just because someone claims to be from the bank or technical support. Real bank employees will never ask for your usernames or passwords. They do not ask for one-time codes from SMS messages.
Article Link: http://blog.ptsecurity.com/2019/06/four-ways-to-phish-how-to-avoid-falling.html