Author: HOTSAUCE | S2W TALON
Executive Summary
- LockBit ransomware was previously known as ABCD ransomware and belonged to the Maze ransomware cartel, but started independent activity in September 2019 as the Maze gang announced its retirement.
- Instead of rebranding the existing name like other ransomware groups, LockBit updated its own brand to 2.0 in June 2021, and now updated to LockBit 3.0 in June 2022.
- The Beta version of LockBit 3.0 was first mentioned while recruiting web pentesters on an underground forum on March 30, 2022.
- The “Affiliate Rule” is more detailed than any other RaaS group, and as the Conti ransomware ceased operations, it is speculated there will be a shift between affiliates with LockBit.
- LockBit seems to be trying to strengthen external attacks and OPSEC by starting their own Bug Bounty Program.
LockBit 3.0 Major Updates
- Removed all existing victim lists uploaded to LockBit 2.0 leak site
- Changed LockBit icon to 3.0 and updated new victim list
- Added Twitter redirecting link
- Updated “WEB SECURITY & BUG BOUNTY”
- Updated “MIRRORS” Links(Blog Mirror 10/ File server 24 / chat server 9 )
- Updated “AFFILIATE RULES”
- Updated “HOW TO BUY BITCOIN”
1. Beta test for LockBit 3.0
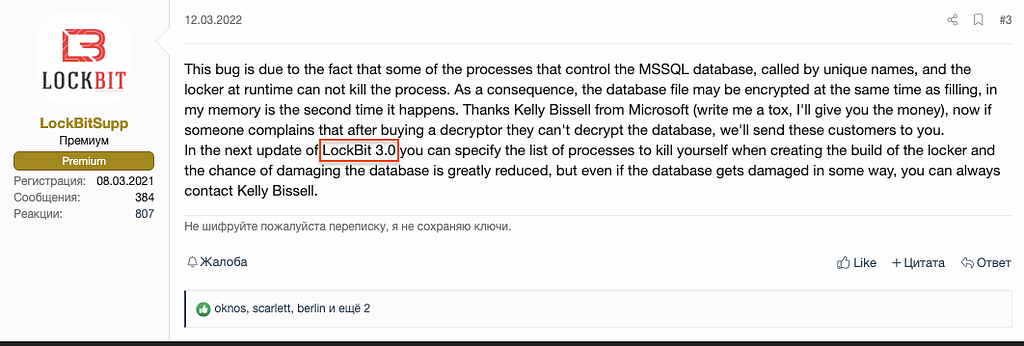
- (March 12, 2022) LockBit mentioned a bug that the MSSQL DB process could not be terminated during the encryption, and in the next release of LockBit 3.0 will be solved the bug by specifying a list of processes to be killed.
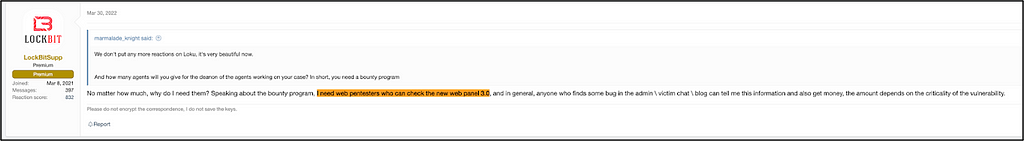
- (March 30, 2022) The Beta version of LockBit 3.0 was first mentioned while recruiting web pentesters on an underground forum on March 30, 2022.
- Tox Messenger Profile Changes
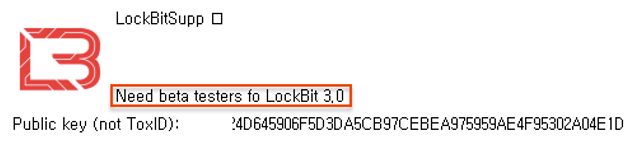 Tox Profile before the 3.0 release
Tox Profile before the 3.0 release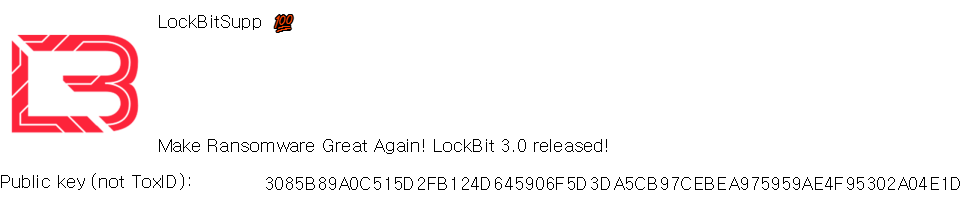 Tox Profile after the 3.0 release
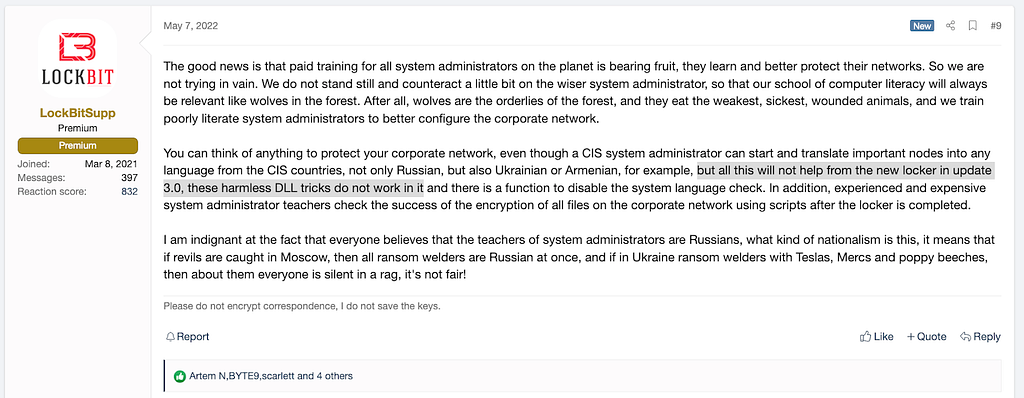
Tox Profile after the 3.0 release- (May 07, 2022) LockBit mentioned that the DLL vulnerability will not work in the next LockBit 3.0 release, and additionally, the feature to check the system language can be turned off.
2. Updates of Loading page
- For Anti-DDos Protection, in LockBit 2.0, the leak site had a loading time of about 7 seconds and 9 mirror sites and 1 web mirror were shown.
- LockBit 3.0 is showing only 9 mirror sites and has an additional loading page with Bitcoin, Monero, and Zcash icons rotating around the LockBit logo.
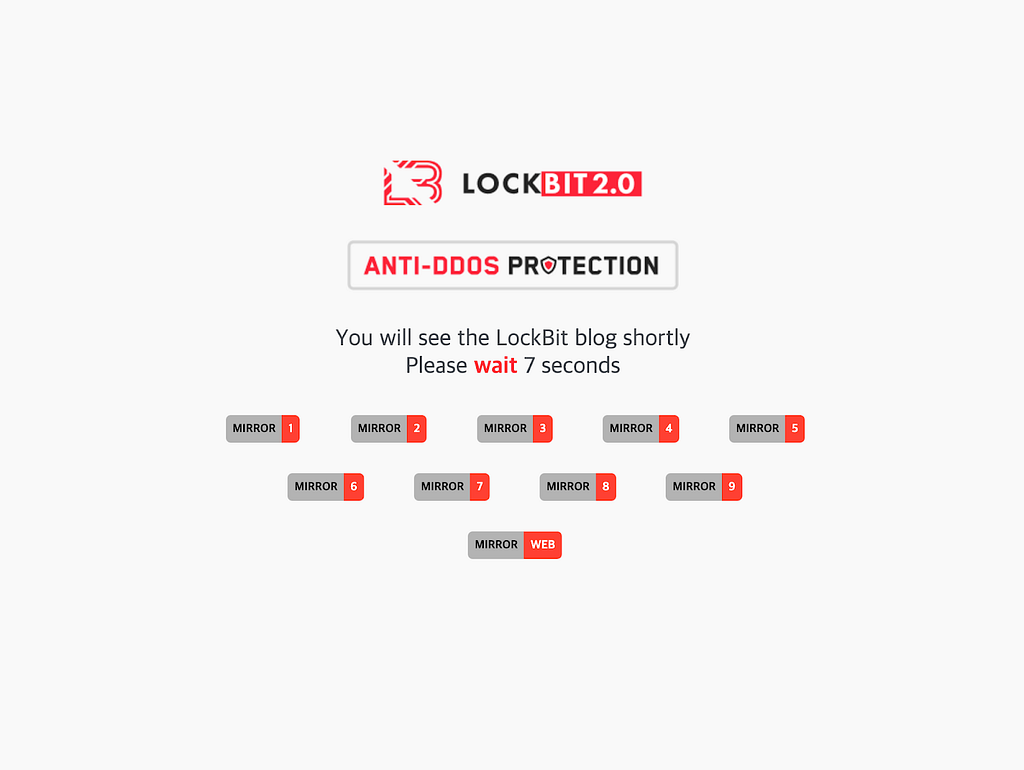 LockBit 2.0 loading page
LockBit 2.0 loading page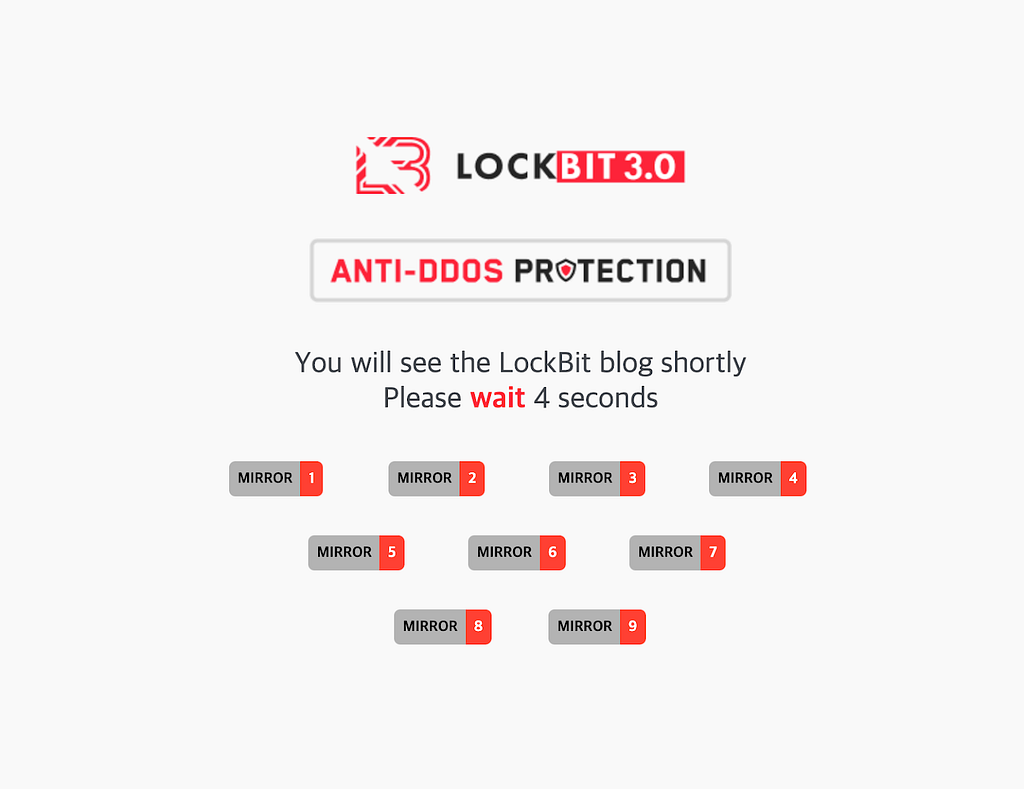 LockBit 3.0 loading page
LockBit 3.0 loading page LockBit 3.0 loading page
LockBit 3.0 loading page3. Updates of the Main page
- The overall leak site UI from LockBit 1.0 to 3.0 did not change much, but detailed pages such as “AFFILIATE RULES”, “MIRROR”, “WEB SECURITY & BUG BOUNTY” were added to the main LockBit 3.0 leak site.
- In the newly opened LockBit 3.0 leak site, all existing victims infected during LockBit 2.0 operation have been deleted, which means that LockBit 3.0 is expected to continue its new campaign, starting with the new 2 victims on June 28, 2022.
 Leak site changes by LockBit version
Leak site changes by LockBit version- LockBit 3.0 disclosed a ransom payment policy split into 3 payment options.
- For each option, Bitcoin and Monero payment addresses are all the same.
— EXTEND TIMER FOR 24 HOURS
— DESTROY ALL INFORMATION
— DOWNLOAD DATA AT ANY MOMENT

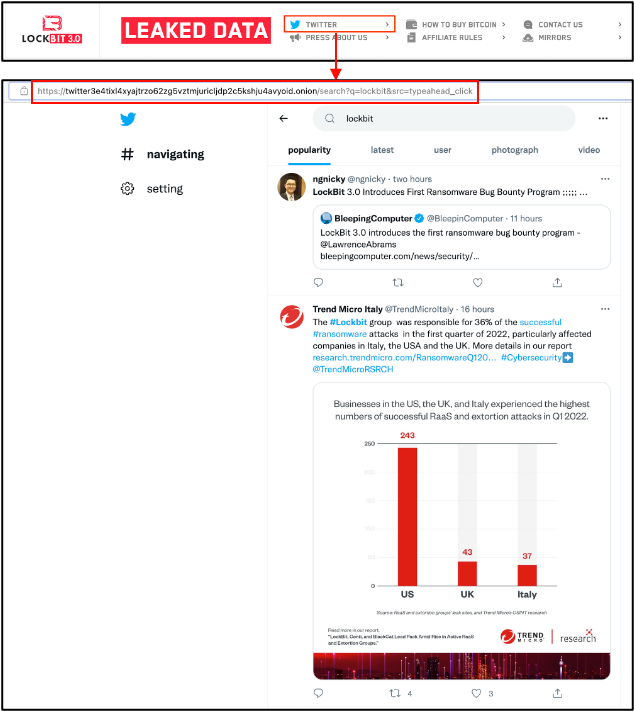
Added Twitter redirecting link
- Added link for searching “lockBit” keyword from the Twitter on the Tor network.
4. Affiliate Rules
- LockBit 3.0 updated Recruitment Details.
- Compared to the previous LockBit 2.0 Affiliate Recruitment on underground forums, the detailed requirement has been added on LockBit 3.0.
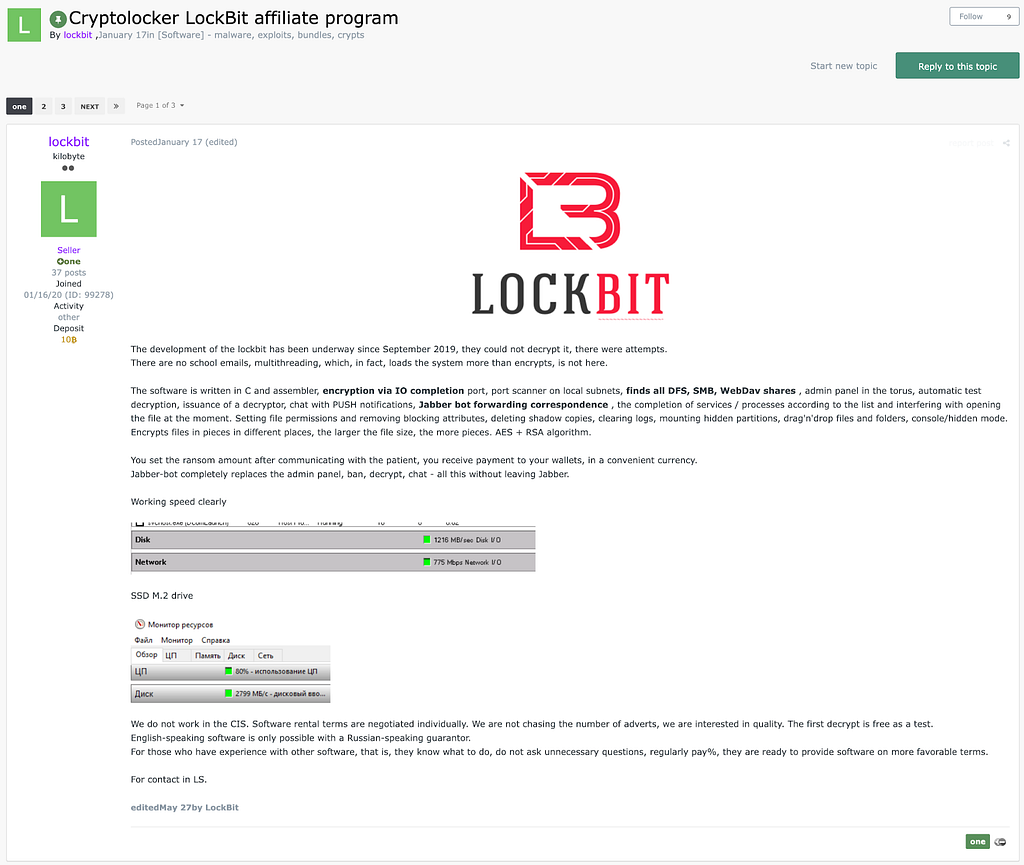 (Jan 17, 2020) LockBit 1.0 Affiliate Rules
(Jan 17, 2020) LockBit 1.0 Affiliate Rules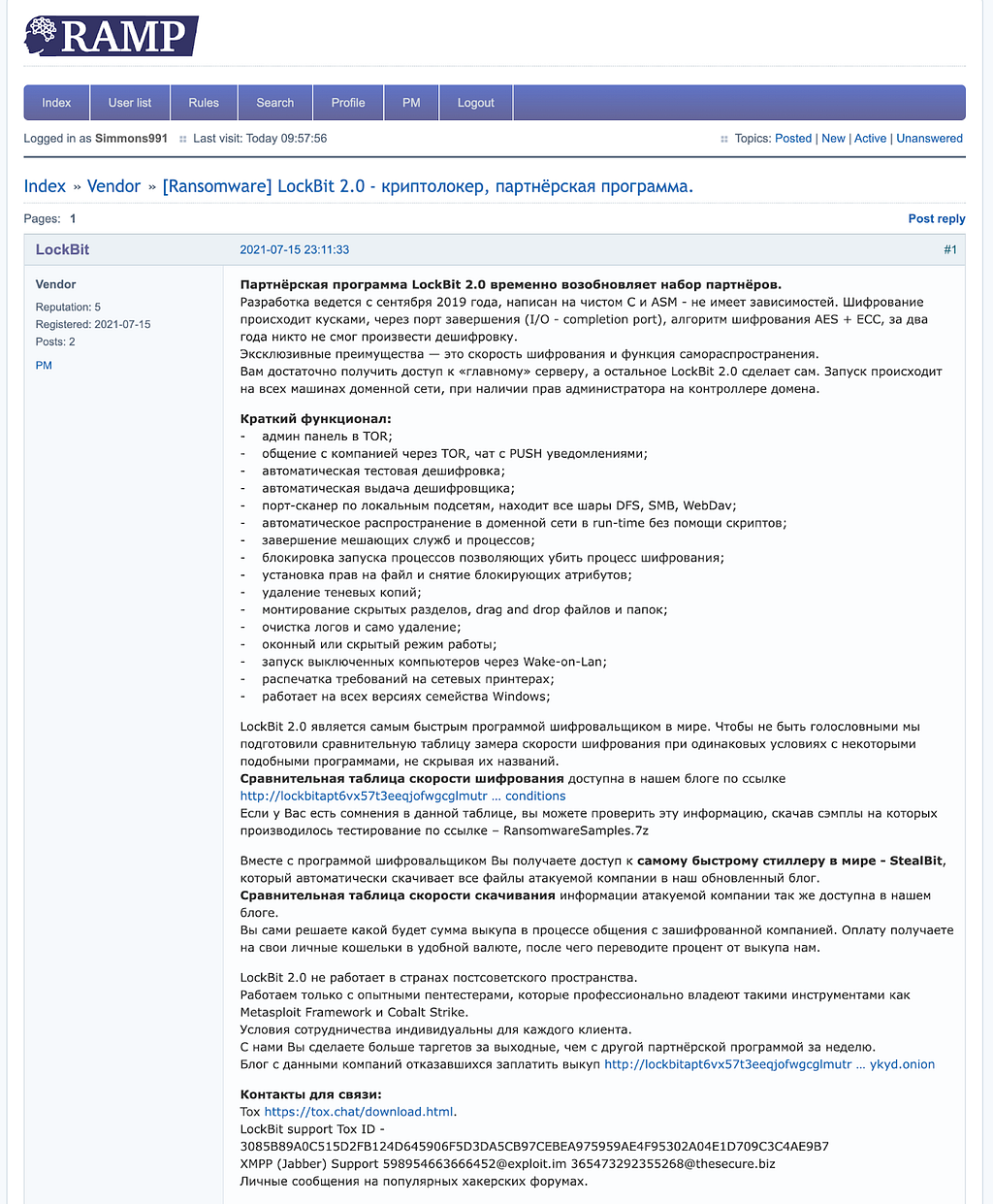 (July 15, 2021) LockBit 2.0 Affiliate Rules
(July 15, 2021) LockBit 2.0 Affiliate Rules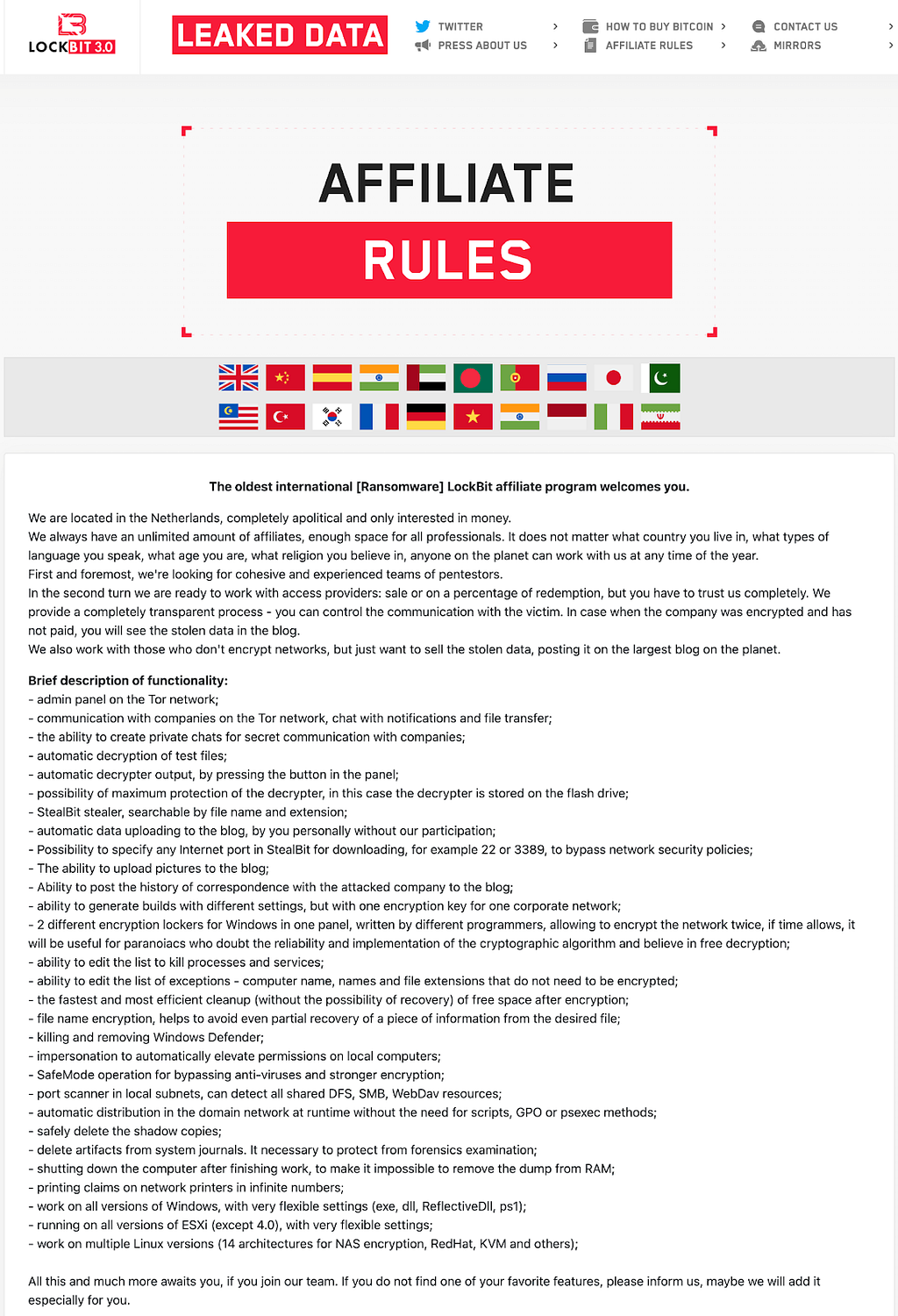 (June 27, 2022) LockBit 3.0 Affiliate Rules
(June 27, 2022) LockBit 3.0 Affiliate RulesSummary of LockBit 3.0 Affiliate Rules
1. We are located in the Netherlands
2. Categories of targets to attack
a. [illegal encrypt / Allowed steal data] critical infrastructure, such as nuclear power plants, thermal power plants, hydroelectric power plants, and other similar organizations.
b. [forbidden to encrypt / Allowed steal data] institutions where damage to the files could lead to death, such as cardiology centers, neurosurgical departments, maternity hospitals and the like, that is, those institutions where surgical procedures on high-tech equipment using computers may be performed.
c. [selectively attack] medical related institutions such as pharmaceutical companies, dental clinics, plastic surgeries, especially those that change sex and force to be very careful in Thailand, as well as any other organizations provided that they are private and have rhubarb
d. Percentage rate of affiliate program is 20% of the ransom(Affiliate 80%)
3. Affiliate Rules
a. Required
- 1 Bitcoin deposit
b. Recommended
- Links to your profiles on various hacker forums
- Show your balance in cryptocurrency at the moment
- Explain the reasons why you left another affiliate program and want to work with us
- It is desirable to have already downloaded information for the blog from the intended target for the attack and provide evidence of the existence of this information, such as screenshots, file tree or access to these files
- Ask your friends or acquaintances who already work with us to vouch for you
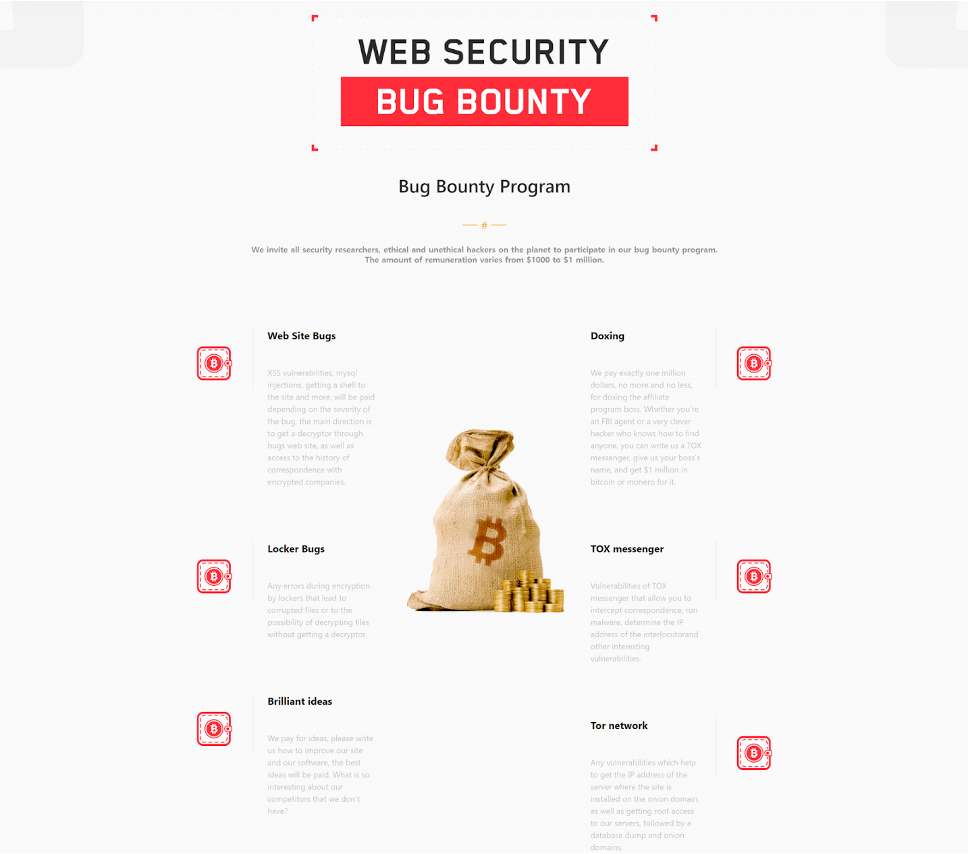
5. Web Security & Bug bounty
- LockBit 3.0 has opened 6 bug bounty items and reward from $1,000 to $1,000,000.
- WebSite Bugs: Web site vulnerabilities
- Doxing: Doxing the affiliated boss
- Locker Bugs: Ransomware encryption bugs
- Tox messenger: Tox messenger vulnerabilities
- Brilliant ideas: Any ideas for improving LockBit ransomware
- Tor Network: Any vulnerabilities which help to get the IP address of LockBit’s server
Conclusion
- As the Conti ransomware group — had the most victims along with LockBit-stopped their ransomware campaign, it is speculated there will be a shift between affiliates with LockBit.
- LockBit 3.0 has opened a bug bounty program and published a list of mirror sites, demonstrating strong confidence that they will not be caught by law enforcement.
- Despite large ransomware groups have been arrested, seized by law enforcement agencies, or rebranded themselves, LockBit is still active.

Homepage: https://s2w.inc
Facebook: https://www.facebook.com/S2WLAB
Twitter: https://twitter.com/S2W_Official
Evolution of LockBit to 3.0 was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Evolution of LockBit to 3.0. Author: HOTSAUCE | S2W TALON | by S2W | S2W BLOG | Jun, 2022 | Medium