There will be times in your career when you will be presented with a traffic capture and get the task to determine what happened and if any data was stolen.
In this post, I will show you how you can squeeze all those juicy information from a PCAP traffic capture from an Azorult infection.
At the end, you will be able to answer which data has been stolen so you can act accordingly. Let’s start!
Getting sample data
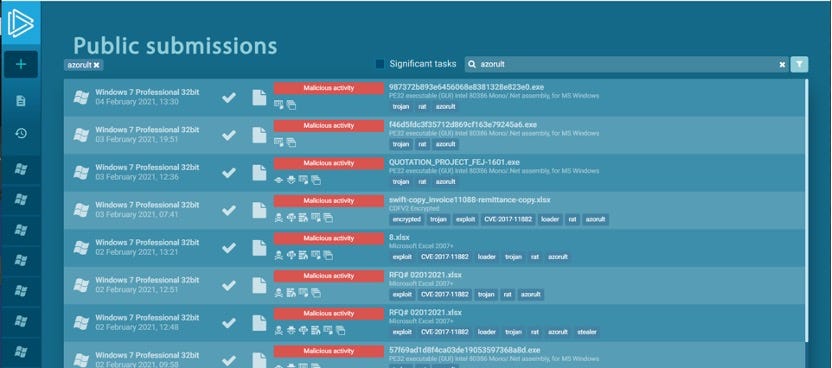
Head over to https://any.run and search for “Azorult” in public submissions or use the PCAP you already got
Most likely you will find a lot of samplesYou will find a lot of samples without actual network traffic since the command and control server was already offline when any.run analyzed the sample. Have a look at samples which show POST requests
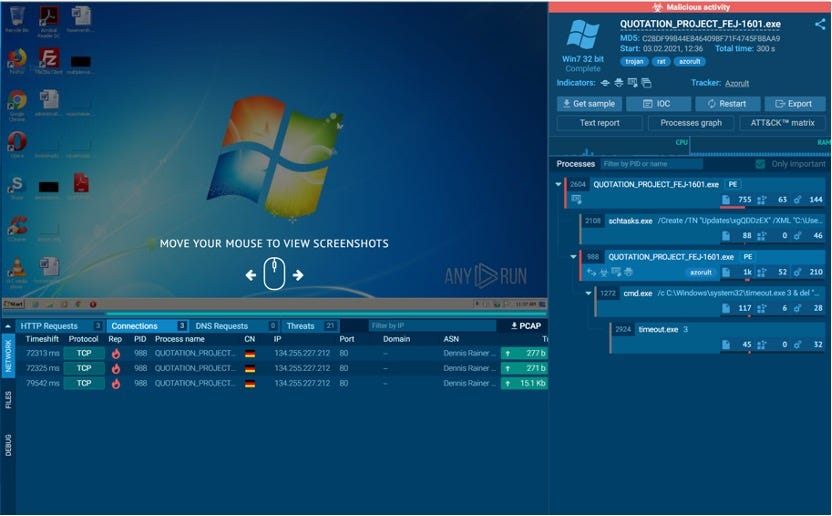
A good candidate for further investigation since you can see multiple POST requestsOnce you found an appropriate sample, download the PCAP to your machine and open it in Wireshark.
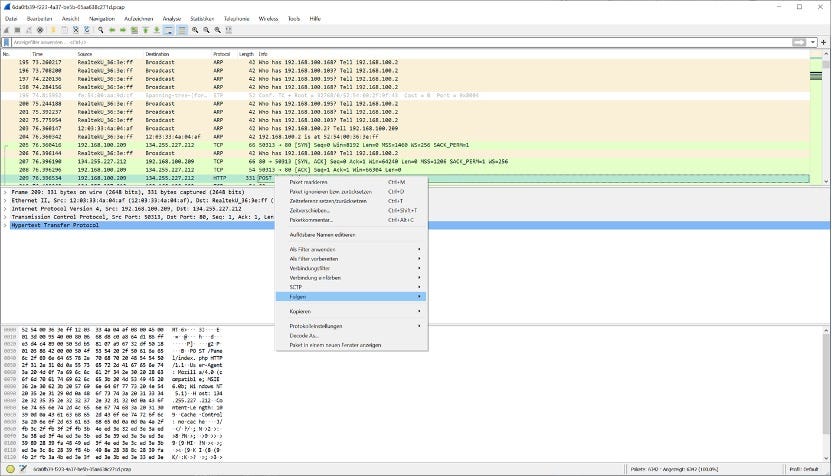
Using Wireshark to follow HTTP streamsYou then have to be on the lookout for HTTP POST requests. If you want to see the content of the request, you can right click the appropriate row and click on “Follow” and “HTTP stream”
The “Check-in” which does not contain any interesting infoYou will notice multiple POST requests while the first is pretty small and functions as a check-in to the Command and Control server. Skip this one since this does not contain any valuable data for us.
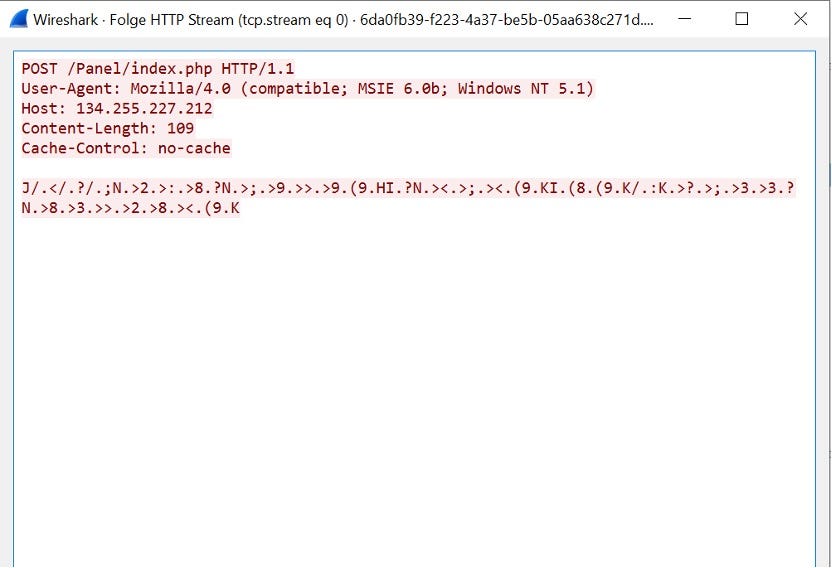
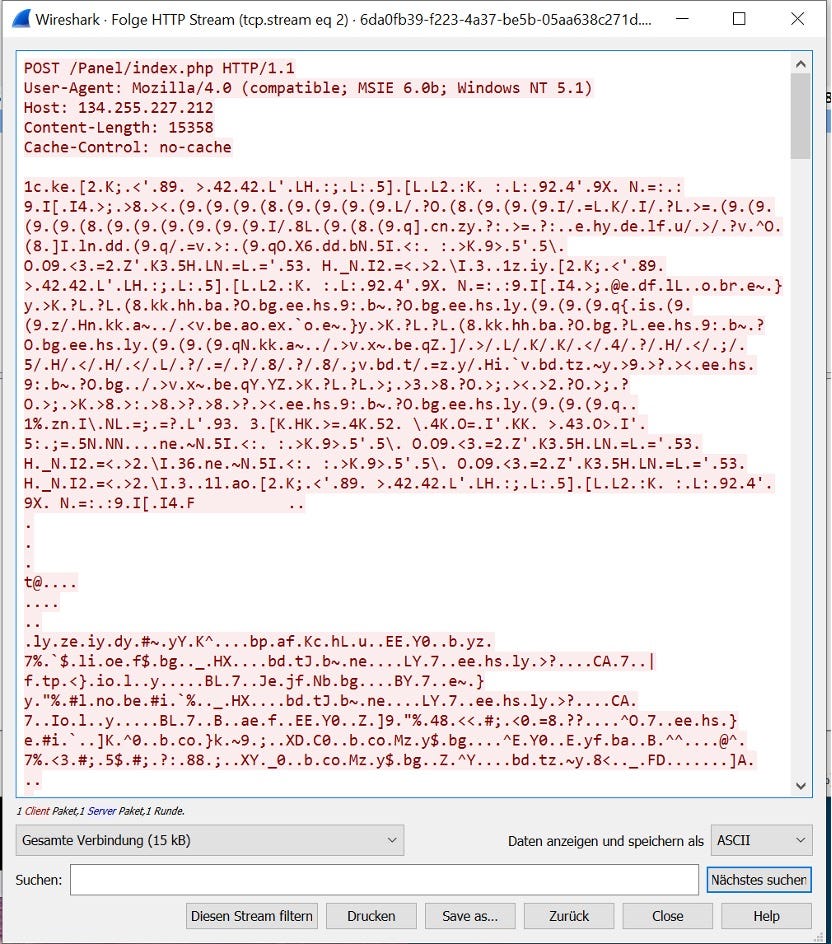
Size matters! The biggest POST request in the PCAP is our targetOne man’s trash is another man’s treasure! Looks like trash but is actually the stolen data getting exfiltrated! That’s the request we are interested in! Notice, that this request contains much more data!
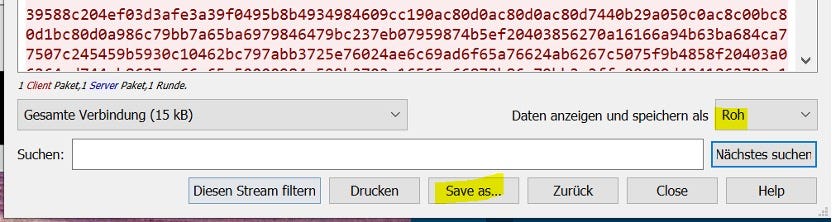
Change view and saveChange the view to “Raw” and save the output to disk so we can further process it.
You might need some patienceNow comes the fun part! As you might have noticed, the POST request data is encrypted in some way. Turns out, it is just XORed with a 3 byte key which unfortunately is not the same for all variants. What now? Make “some” educated guesses?
Fear not, I created a tool which first tries to decrypt it with keys I found in the wild and if this is not successful, it will start to brute force the key. This is possible with the help of a known plaintext attack since I learned through manually reversing AzoRult that the plaintext stolen data contains strings like “<info” which we can look for after every decryption try.
You can get it here: https://GitHub.com/hariomenkel/AzoBrute
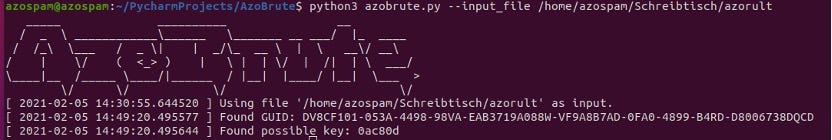
Once downloaded, let it run against the extracted POST request and hopefully, you’ll receive the key.
Please consider creating an issue at the AzoBrute GitHub repository with your key so I can add it to the list of keys which are tried before trying brute force. Sharing is caring!
Once you have the key, copy it — you will need it for another tool
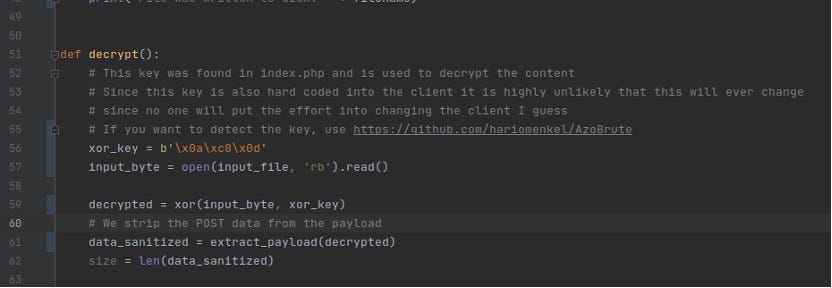
Change the value of “xor_key”Now when you have the key, you might want to extract the stolen data don’t you? To do so, get https://GitHub.com/hariomenkel/AzoDecrypt and open it in an editor to change the value of “xor_key” to the value you found earlier. Don’t forget to add \x before every byte so the format is the same as before. When you are finished, save it and run that bad boy!
Decrypt that bad boyAs you can see, the tool was able to use your key to find the payload, extract it and also squeeze out a ZIP archive containing all stolen credentials, cookies, system infos etc.!
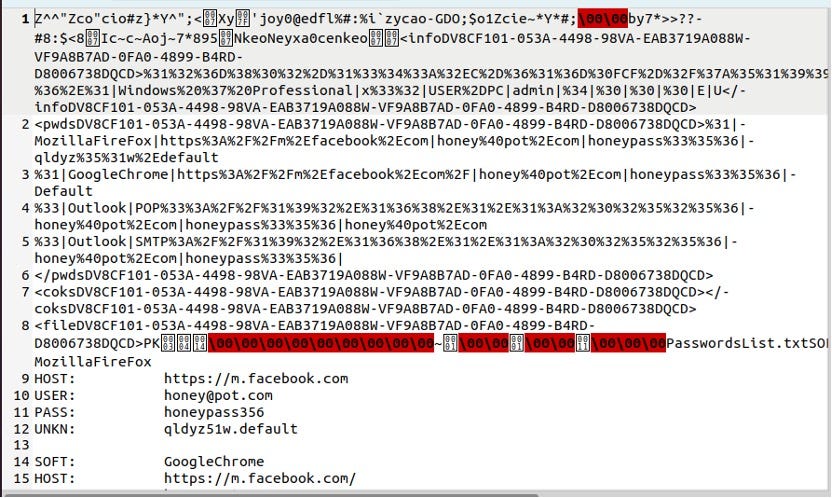
Beauty lies in the eye of the beholderThis is the POST request which has been XORed which already shows some information
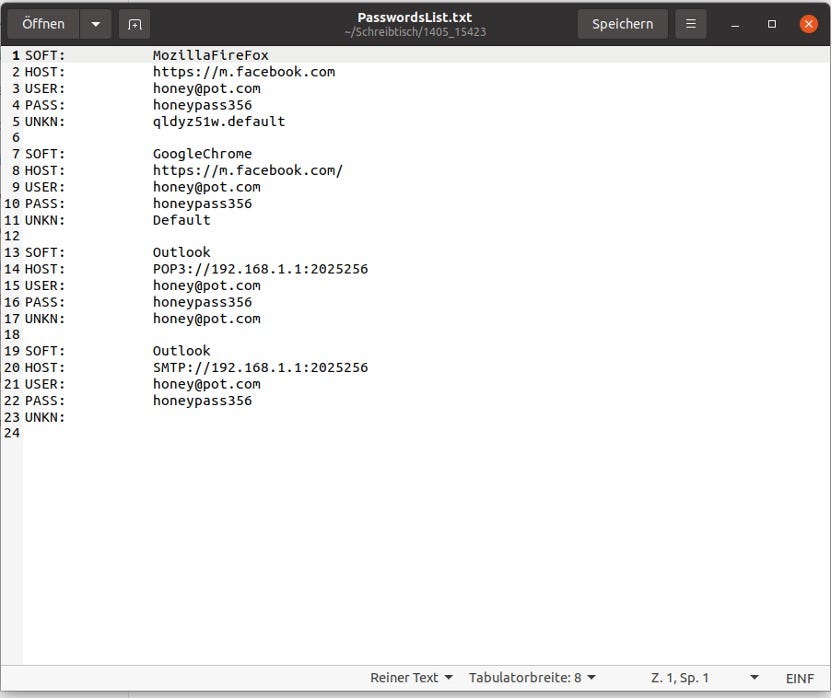
 Content of ZIP file
Content of ZIP fileThe really interesting data is in the ZIP file. You might want to have a look at it!
PasswordsList.txtHere you can see the Fake credentials any.run was hosting while running the sample
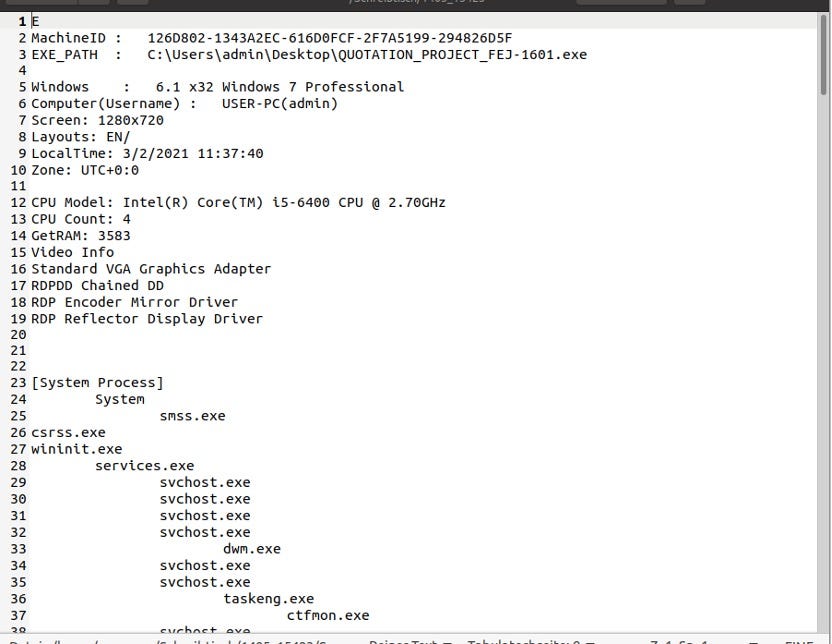
Systems.txtThe attacker is also able to gain a lot of information from your system through system.txt
What next?
Now that you have the correct XOR key and GUID you can use another tool I created to annoy the attacker through flooding his/her AzoRult panel with real looking fake data which makes it hard to distinguish between real and fake victims and ultimately may stop the attacker from selling the data due to its bad quality.
You can get it here: https://GitHub.com/hariomenkel/AzoSpam
Article Link: https://medium.com/@mariohenkel/decrypting-azorult-traffic-for-fun-and-profit-9f28d8638b05?source=rss-79556bb72cbb------2