DDoS attack...! Oh, scary...
But, what is a DDoS..? Is this kind of cyber weapon... Is this going to harm the digital world?
Let's find out how DDoS will affect enterprise safety, and how we can mitigate them...
This blog is intended to build a tool that simulates and helps mitigate the DDoS attack. In less than a decade ago, DDoS was a reasonably straightforward cyber-weapon with which the attacker sends a large number of requests to paralyze a web server and shut down online services. Over the years, as the Internet has evolved rapidly in terms of bandwidth and technology, DDoS attacks are no longer just a nuisance.
Nowadays, apart from being gigantic and more advanced in complexity, they are increasingly being employed as part of a more complex hacking plot— often targeting the sensitive or critical customer information, like credit card data, and even real money.
As an organization, whether it be big or small, relying on continuous presence online. The impact of such big mainstream attack can cause network, server or applications the downtime, degrading their performance with its bundle of risks added in it.
While certain on-premise appliances can take small-scale attacks to an extent, they may not mitigate large-scale and complex attacks at different layers of the network. Whether it be any size of the organization, a sudden traffic spike may overload the systems; even it is a service provider due to insufficient dynamic bandwidth.
To keep the business with its services running and giving the customer their uninterrupted responsive application, we propose to develop a tool or simulation engine over a Dynamic Security Framework. This tool can simulate various DDoS attacks and have a capability to Monitor, Detect and Mitigate DDoS.
But, What is DDoS?
In its most straightforward form, Denial of Service (DoS) is a deliberate attack on any system components to degrade its normal working process. It may be directed to specific OS, port or service to the target system, to a network, to a firewall or any other components and environment.
Distributed Denial of Service (DDoS) attack is a DoS attack that occurs from more than one source, to/from more than one location, in one or more forms simultaneously. Regularly, the DDoS assailants don't know that they are taking part in a DoS assault against a site, and are hoodwinked into joining the attack by an outsider.
This blog provides an overview of the common types of DDoS attacks, the negative impact of DDoS attacks on business, and mitigation steps to reduce the impact ratio of the DDoS attack on the system.
The vulnerabilities of the Open System Interconnect (OSI) layer are a doorway to variations of DDoS attack, starting from Layer 1 climbing up to Layer 7. But the most common attacks that we see on the OSI are at layer 3, 4 and layer 6,7 which are known as Infrastructure layer attack and Application layer attack respectively.
Detect level -focused on being able to pinpoint abnormal behavior
Respond level -focused on responding in case of a DDoS attack
The dynamic security framework configured over data centers and servers of the different organization over a secure channel maintained by a firewall help in the following:
We plan to build a controller with the following features
Where all these parameters can be monitored over an Event Management & Reporting which allows you to consolidate all management tasks into a single pane of glass making it simple to apply consistent policies across all your DDoS devices.
Security administrators can view a dashboard of DDoS attacks in real time, with a wide variety of policies and thresholds at your fingertips, regulate traffic and block suspicious activity with fine granularly.
Recommendation to overcome DDoS:
But, what is a DDoS..? Is this kind of cyber weapon... Is this going to harm the digital world?
Let's find out how DDoS will affect enterprise safety, and how we can mitigate them...
This blog is intended to build a tool that simulates and helps mitigate the DDoS attack. In less than a decade ago, DDoS was a reasonably straightforward cyber-weapon with which the attacker sends a large number of requests to paralyze a web server and shut down online services. Over the years, as the Internet has evolved rapidly in terms of bandwidth and technology, DDoS attacks are no longer just a nuisance.
Nowadays, apart from being gigantic and more advanced in complexity, they are increasingly being employed as part of a more complex hacking plot— often targeting the sensitive or critical customer information, like credit card data, and even real money.
As an organization, whether it be big or small, relying on continuous presence online. The impact of such big mainstream attack can cause network, server or applications the downtime, degrading their performance with its bundle of risks added in it.
While certain on-premise appliances can take small-scale attacks to an extent, they may not mitigate large-scale and complex attacks at different layers of the network. Whether it be any size of the organization, a sudden traffic spike may overload the systems; even it is a service provider due to insufficient dynamic bandwidth.
To keep the business with its services running and giving the customer their uninterrupted responsive application, we propose to develop a tool or simulation engine over a Dynamic Security Framework. This tool can simulate various DDoS attacks and have a capability to Monitor, Detect and Mitigate DDoS.
But, What is DDoS?
In its most straightforward form, Denial of Service (DoS) is a deliberate attack on any system components to degrade its normal working process. It may be directed to specific OS, port or service to the target system, to a network, to a firewall or any other components and environment.
Distributed Denial of Service (DDoS) attack is a DoS attack that occurs from more than one source, to/from more than one location, in one or more forms simultaneously. Regularly, the DDoS assailants don't know that they are taking part in a DoS assault against a site, and are hoodwinked into joining the attack by an outsider.
This blog provides an overview of the common types of DDoS attacks, the negative impact of DDoS attacks on business, and mitigation steps to reduce the impact ratio of the DDoS attack on the system.
The vulnerabilities of the Open System Interconnect (OSI) layer are a doorway to variations of DDoS attack, starting from Layer 1 climbing up to Layer 7. But the most common attacks that we see on the OSI are at layer 3, 4 and layer 6,7 which are known as Infrastructure layer attack and Application layer attack respectively.
DDoS Attack Categorization
DDoS assaults are a developing risk to endeavors and associations depending on continuous online nearness. In its most local shape, the assailant surges the objective server or system by sending monstrous solicitations to soak arrange limit or fumes organize assets, with the goal that real clients are denied get to. Bigger, increasingly advanced DDoS assaults are regularly planned by the assailant behind botnets, or systems of trade-off PCs or gadgets. DDoS assaults can be extensively separated into three general classes:
Attack |
Types | Description |
Volumetric |
UDP /TCP Flood,
ICMP(Ping) Flood,
Slowloris,
NTP Amplification,
DNS Reflection/ Amplification,
Chargen(Character Generator),
Zero-Day attack
|
Attacks use a massive amount of traffic saturating the bandwidth of the target.
They use amplification techniques, i.e. multiplies the packet too large numbers and flood them to the target machine crashing it.
|
Protocol |
Smurf Attack,
Fragmented packet attacks, SYN Flood,
Ping of Death
|
Attacks that cause a target inaccessible by exploiting a weakness in the layer 3 and layer 4 protocol.
They consume all the processing capacities of the target or intermediate critical resources.
|
Application |
HTTP Flood,
An attack on DNS services
|
These attacks exploit a weakness in the layer 7 protocol stacks.
The most sophisticated of attacks and most challenging identifying/mitigate.
Establish a connection with the target and then exhaust the server resources by monopolizing process and transaction.
|
It is essential to take note of that while most basic DDoS assaults extensively fall into these three classifications, a few assaults can likewise be a mix. For instance, the ongoing assault on Dyn's DNS foundation was a blend of an application and convention assault on DNS administrations that ventured into a volumetric assault. It is likewise vital to specify that while a few assaults focus on the DNS framework specifically, others can utilize DNS as a way to trigger an assault.
Impact of DDoS Attack
The impact of DDoS attacks can be devastating, especially if the organization or business relies heavily on uninterrupted online presence to maintain e-commerce business, online operations and/or brand equity. Unprepared for such threats, a sudden attack could cause direct revenue and customer loss, damage to brand and reputation, and incur extra costs in taking remedial actions.
Revenue Loss
Your clients will be vexed about your site and administration on the off chance that they have to hold up a while to stack the page or access to its applications, which thusly will debilitate them from paying for your item or conversely benefit once more. In the event that web-based business—anything from online toy store to security, exchanging stage— is your real income source, downtime causes coordinate income misfortune and it could be gigantic, taking into account the income misfortune amid the downtime and the reputational harm, consolidating negative expression of word and client disappointment, going ahead.
Brand Loss
While income misfortunes caused by downtime can be determined, the tarnished reputation is increasingly hard to measure. Past that, keep in mind that first-time guests, who were denied access to your site, were disinterested and the chance is they will stay away for the indefinite future. Existing clients are likewise prone to change to another merchant or specialist organization, particularly if the business is exceptionally aggressive, where items or administrations are to a great extent homogeneous (think about stock exchanging). On the off chance that you a specialist co-op that has benefit level assertions for uptime, you might be liable to penalties.
Data Loss
As known the DDoS is an attack that degrades the performance of the online process, it's a mere distraction by an attacker to compromise the system to steal the data. Small businesses are likely to lose data due to a DDoS attack—31% of SMBs reported data loss, compared with 22% of enterprises. The damage scope of such attacks goes far beyond the temporary downtime of a corporate website. Companies report total disruption to their operations, and in some cases—loss of sensitive data.
DDoS Mitigation
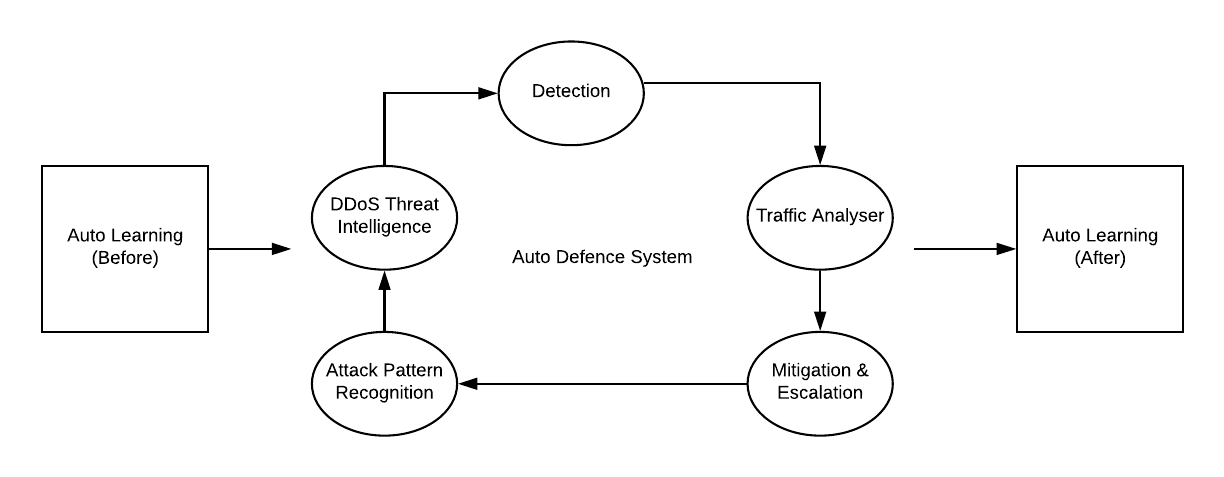
DDoS attacks are becoming the most prevalent type of cyber threat as a mainstream attack and they have grown rapidly over the years with changing technology. Though we don’t have a single approach to cover all DDoS risk, we can take multiple measures to prevent or minimize the risk. This is a small attempt to reduce the attack ratio by building a DDoS Simulation Engine with a capability to Monitor, Detect and Mitigate DDoS. So we plan to integrate the simulation engine over a dynamic security control framework.
The distributed nature of DDoS suggests a distributed mechanism is necessary for a successful defense.
Three main DDoS defense functionalities -
- Attack detection - at victim-end
- Rate limiting - at Core
- Traffic differentiation - at source-end
As we speak about the auto-learning before and after, the 5 step process is a mandatory procedure to mitigate and evolve with the growing threats and combinatorial attacks.
The Automation process would carry out the following :
- Service discovery.
- Real-time traffic monitor and analysis.
- Ranking the threats according to its criticality.
- 5 Level mitigation.
- Adaptive Learning.
- Event Management & Reporting.
The framework contains procedural controls and technical controls divided into function levels:
Identify -- Protect -- Detect -- Respond -- Recover -- Assess -- Adjust.
Technical measures in this framework would be:
- Protection level -focused on pre-eruptive measures
- An SYN Proxy is implemented
- Anomaly Recognition
- Dark Address Prevention (block IP addresses that are not yet assigned by IANA)
- White-List and black-List are maintained
- Connection Limiting
- Active verification through Legitimate IP Address Matching
- Implementing anti-spoofing measures
- Firewalls configured to apply filtering to monitor the traffic for certain protocols, the number of connections made from one IP-address
- Implement adequate storage facilities to retain logging files
Detect level -focused on being able to pinpoint abnormal behavior
- Setup of Intrusion Detection Systems (IDS) & Intrusion Prevention System.
- Flow-based accounting.
- Granular Rate Limiting.
- Dynamic Filtering.
- Source Rate Limiting.
Respond level -focused on responding in case of a DDoS attack
- Quality-of-Service (QoS)
- Null-routing
- ACL to block (or permit) certain source of destination IP -addresses and/or protocols
- Aggressive aging
- White-List and black-List are maintained
- DDoS wash street
- Specific DDoS appliances
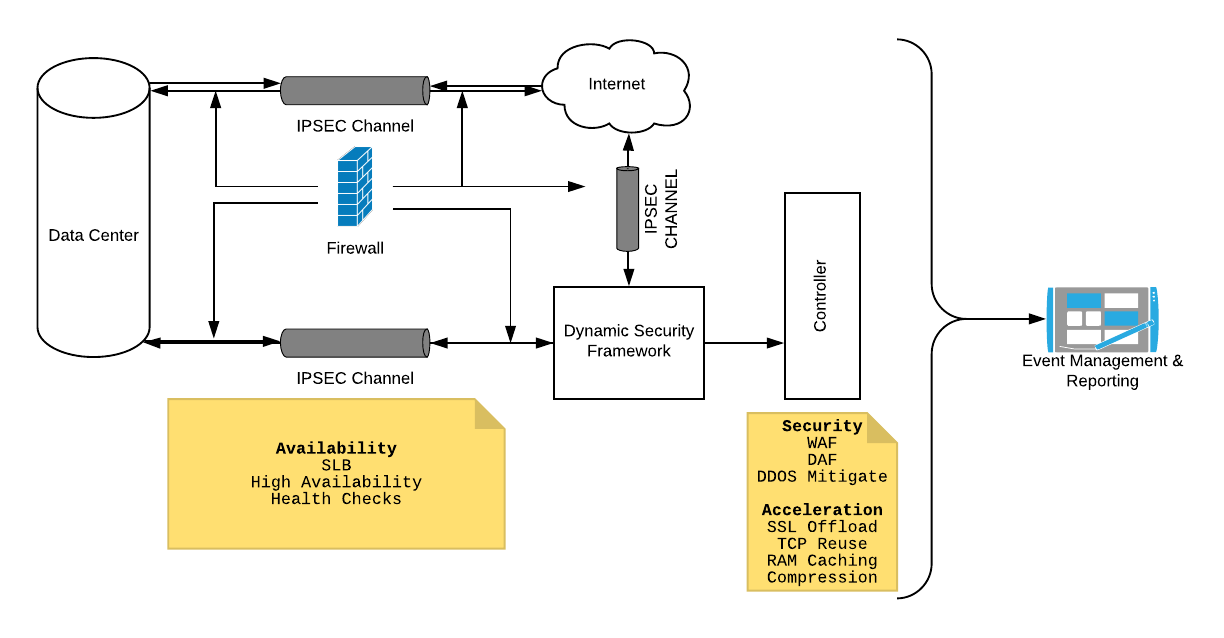
System Design

The dynamic security framework configured over data centers and servers of the different organization over a secure channel maintained by a firewall help in the following:
- High Availability
- Server Load Balancing
- Health Checks(overall)
We plan to build a controller with the following features
- Security
- WAF
- DAF
- DDoS Mitigation
- Acceleration
- SSL Offload
- TCP Reuse
- RAM Caching
- Compression
Where all these parameters can be monitored over an Event Management & Reporting which allows you to consolidate all management tasks into a single pane of glass making it simple to apply consistent policies across all your DDoS devices.
Security administrators can view a dashboard of DDoS attacks in real time, with a wide variety of policies and thresholds at your fingertips, regulate traffic and block suspicious activity with fine granularly.
Recommendation to overcome DDoS:
Attack Type |
Protection Recommendation |
DNS |
Acquire 2 DNS services for redundancy
2 Managed DNS providers
1 Managed DNS, 1 on-premises DNS
Secondary DNS can be low cost
|
HTTPS |
DDoS mitigation tech see traffic in clear text
DDoS Defense not too deep in the network
|
Hit-Run(Burst attack) |
Improve Detection time
Monitor Network Flood, Application Flood
|
APT DDoS attack |
DDoS Testing
Configuration and hardening
Emergency Procedures and policy
|
Generally, many security computation algorithms exhibit a trade-off between QoS and Execution time. For example, a firewall can be properly configured to drop only illegitimate traffic which can be generalized as Deep Packet Flow Inspection (DPFI).
So we propose a recursive flow model by analyzing and filtering illegitimate traffic flows from legitimate traffic flow this will prevent malicious packets from impacting the QoS performance while allowing legitimate traffics to complete appropriately. A firewall with two distinct components Traffic Anomaly Detector(TAD) and Guard alert trigger work together to deliver complete DDoS protection for virtually any environment.
This purification process consists of 5 modules :
- Filtering
- Active Verification
- Anomaly Recognition
- Protocol Analysis
- Rate Limiting
In context, between any DDoS attacks, the model will be in learning mode, passively monitoring traffic patterns and flows for each of the different resources it protects to understand the behavior of the system. Later used to fine tune the system to recognize and filter known and unknown attacks on real-time network activity.
As known DDoS can affect every layer of the OSI model, let us see how we can have a mitigation plan to patch the attack types of internet cookies before the organization can take a huge hit.
No |
Name |
Vulnerability |
Mitigation |
7 |
Application Layer |
PDF GET requests, HTTP GET, HTTP POST, Web forms |
One approach to check the DDoS assault on Layer 7 is to bring observing programming applications into training. By utilizing a lot of committed calculations and advancements which can identify zero-day assaults, powerful application checking can stop and track back the source from where the assault started.
|
6 |
Presentation Layer |
Malformed SSL Requests, Inspecting SSL encryption packets is resource intensive.
Attackers use SSL to tunnel HTTP attacks to target the server.
|
One approach to dodge this assault is to offload the SSL from the starting point foundation. Once, you have effectively done that, it's an ideal opportunity to assess the application traffic for any indications of pernicious exercises. Make sure to determine the status of any infringement of strategy at an application conveyance stage (ADP). A successful ADP will likewise ensure that the traffic is re-encoded and sent back to the birthplace foundation. |
5 |
Session Layer |
Telnet DDoS-attacker exploits a flaw in a Telnet server software running on the switch, rendering Telnet services unavailable. |
The best way to determine this helplessness is to stay up with the latest. Most regularly, the equipment supplier issues an adaptation refresh or a fix which empower clients to alleviate the weakness.
|
4 |
Transport Layer |
SYN Flood, Smurf Attack |
A run of the mill strategy to prevent DDoS assaults occurring on this dimension is through blackholing. It is a technique inferred by the ISPs to stop any DDoS assault that a client involvement with the vehicle layer. Notwithstanding, this way to deal with keeping the DDoS assault out of the framework stops all traffic (noxious and authentic) from getting into the framework.
|
3 |
Network Layer |
ICMP Flooding – A Layer 3 infrastructure DDoS attack method that uses ICMP messages to overload the targeted network’s bandwidth. |
You can keep this assault from occurring by rate-limiting ICMP traffic. |
2 |
Data Link Layer |
MAC flooding is an attack that inundates the network switch with data packets which usually takes place at the Data Link Layer. |
Advance switches can be arranged to constrain quantities of MAC tends to which are bound to be learned on ports associated with end stations
|
1 |
Physical Layer |
Physical destruction, obstruction, manipulation, or malfunction of physical assets |
Practice protection top to bottom strategies, access controls, responsibility, and evaluating to track and control physical resources |
Advantage:
Advantages of having this engine on the dynamic framework,
Growth: Scalability with respect to network growth.
Intelligence: Active mitigation capability.
Latency: Rapid DDoS response.
Deployment Ease: can be deployed at least adjacent to the router, switches over a framework.
Intelligence: Active mitigation capability.
Latency: Rapid DDoS response.
Deployment Ease: can be deployed at least adjacent to the router, switches over a framework.
Conclusion
For any association depending on continuous online presence, DDoS assault causes coordinate income misfortune, client misfortune, increment costs, and can harm their notoriety medium-term. Assailants these days utilize many hacking and attack methods to carry out increasingly serious digital crimes. So, to the extent we practice and evolve with the right architecture we are to be protected by such attacks.
Here is a small effort to build the right system with the right policies.
- Heuristic-based intelligence, and exact location and alleviation of utilization based assaults.
- Static and dynamic substance storing and speeding up to upgrade web application execution and the client encounter.
- Proprietary, dynamic test reaction component for high relief precision and non-troublesome client encounter.
- 100% uptime ensure; briefest alleviation reaction time; dependably on assurance.
- Constant dashboards with outwardly engaging maps, outlines, and diagrams, indicating live traffic, assault also, danger measurements, point by point occasion logs, guest socio-economic and many other valuable investigations.
Article Link: https://blog.lucideus.com/2019/05/ddos-engine-over-dynamic-framework.html