Author: Jaehak Oh, Sunhyung Shim | S2W DIA
 Photo by Nahel Abdul Hadi on Unsplash
Photo by Nahel Abdul Hadi on UnsplashDarkpedia
Delivers information of major events happening on worldwide.
Primarily focus on ‘how’ the event have impacted Darkweb users and trends.
Summary
- Ransomware groups’ activity at Russia Hacking Forum has dramatically decreased after Colonial Pipeline incident
- Despite, Dark Web Ransomware gangs are not only maintaining but increasing the number of cyber attacks, which resulted in increased number of corporate victims
- Russia Hacking forum users prove their hacking ability by selling corporate internal network access; eventually providing the source of attack to ransomware groups or be hired as a ransomware partners
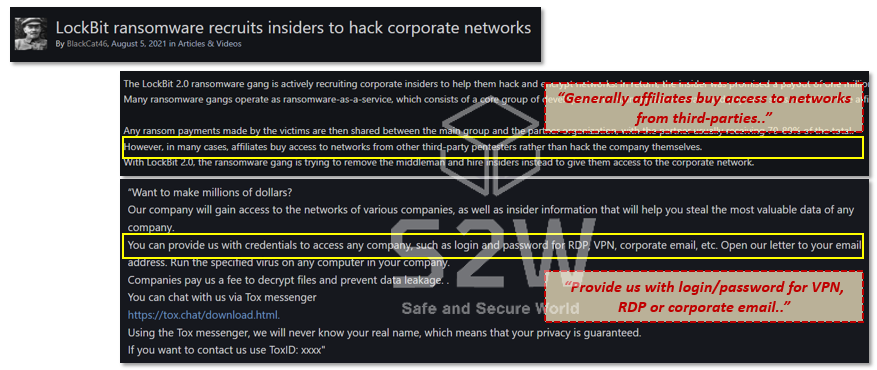
Russian Dark web hacking forum has been used as a communication channel for Ransomware groups
→ Particularly, forums are utilized to promote ransomware group’s site or share relevant information, also used as a channel to provide ‘recruitment’ information for recruitment.
 Recruitment posts by ransomware groups seeking for hackers
Recruitment posts by ransomware groups seeking for hackersAfter Colonial Pipeline incident, role as a ransomware communication channel decreased
→ Ransomware Group’s ‘job search’ posts, which have been on a steady rise starting 2020, have plummeted since May 2021, and related posts have rarely been posted recently.
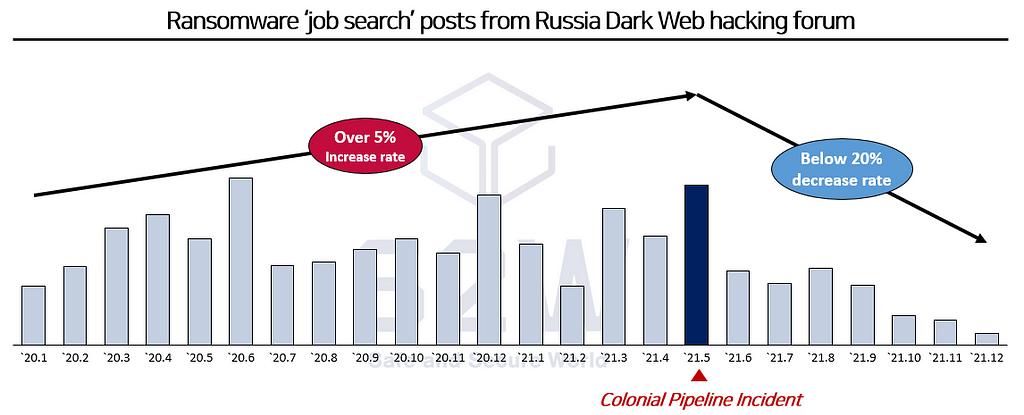 Source: S2W Dark Web Big Data
Source: S2W Dark Web Big Data[Appendix] What is Colonial Pipeline incident?
→ In May 2020, the dark web ransomware group “DarkSide” launched a cyber attack on the largest oil pipeline company in the United States, causing the pipeline to be suspended for about a week, which disrupted the delivery of oil and gas in the United States.
Summary of the incident
2021.05.07- Russia ransomware group “DarkSide”, launched a cyber attack on the largest oil pipeline company in the United States
(Colonial Pipeline: A pipeline that transports oil/gas, etc., accounting for 45% of the eastern United States’ transport)
~2021.05.12- System affected by cyber attack, causing the pipeline to be suspended for about a week
2021.05.12- Victim (Colonial Pipeline) paid approximately 75 Bitcoins (which accounted for around $US 5M at the moment) for ransom.
After the ransom payment was made, DarkSide provided system recovery tool
2021.06.07- United States counterattacked the gangs; then recovered approximately 85% of Bitcoins that were paid as a ransom
After the incident, U.S. government declared that they will no longer bear with ransomware groups; which caused the change for Russia Hacking forums
→ Major Russia hacking forums banned ransomware ‘job search’ posts or anything related to such.
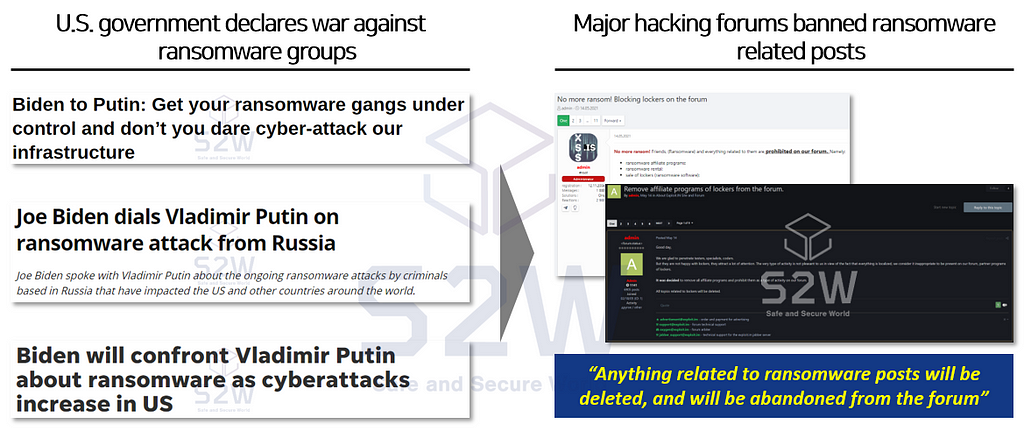
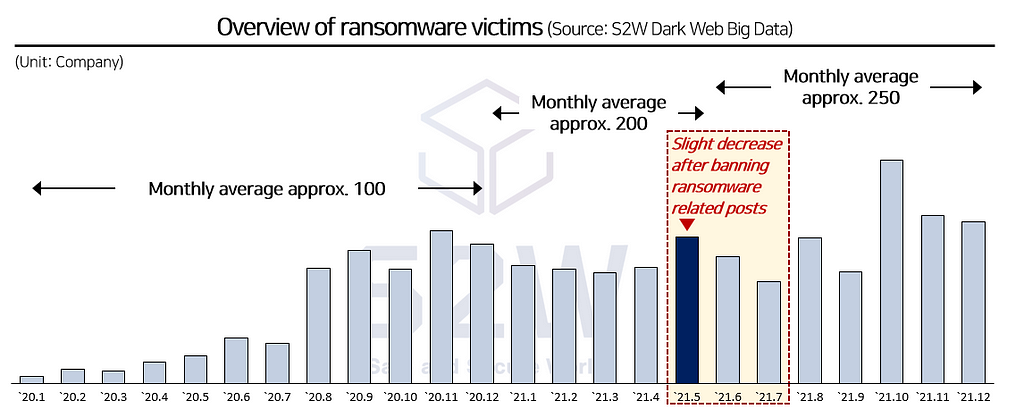
Banning ransomware related posts on the forum seemed effected for a while; however ransomware groups was unstoppable
→ On the end of year 2021, number of victims increased sharply, eventually ransomware groups showing off their abilities.
[Appendix] Dark Web ransomware group’s organization as an example
→ Most of the Dark Web ransomware groups operate systematically, especially in the case of affiliate partners, number of external personnel are required for successful ransomware attack.
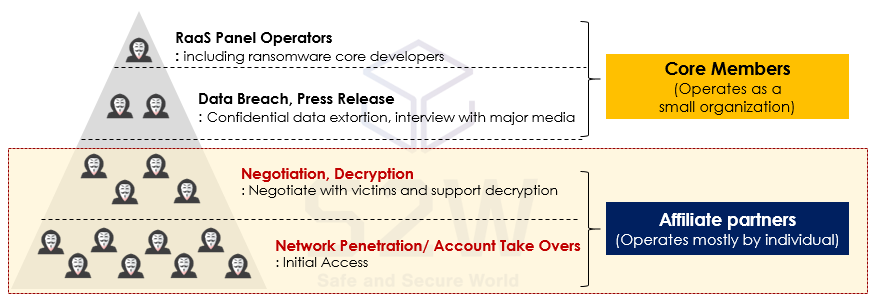 Source: S2W CTI (Talon) Ransomware Report
Source: S2W CTI (Talon) Ransomware Report[Appendix] Role of affiliates in ransomware groups
→ Partners play a role in directly attacking the affected companies. They are guaranteed 70–80% of the total revenue and play a key role in ransomware attacks.
How are ransomware groups continuing their activities by recruiting external partner personnel?

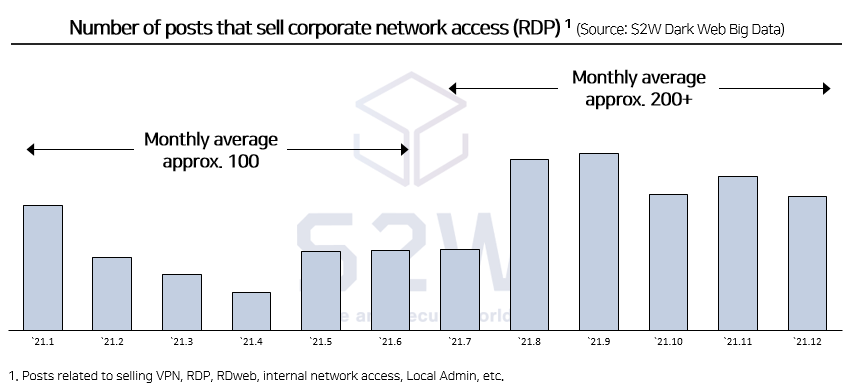
Recently, sharp increase of selling ‘corporate network internal access’ from Russia Hacking Forums was found
→ Dozens of related posts, that can penetrate to numbers of corporate internal networks, are found on a daily basis.
Cyber gangs sell corporate internal networks on hacking forum boards, with a competitive manner
→ Gangs actively show off the corporate’s scale that they have managed to attack; simultaneously promote themselves to work as a ransomware partners .
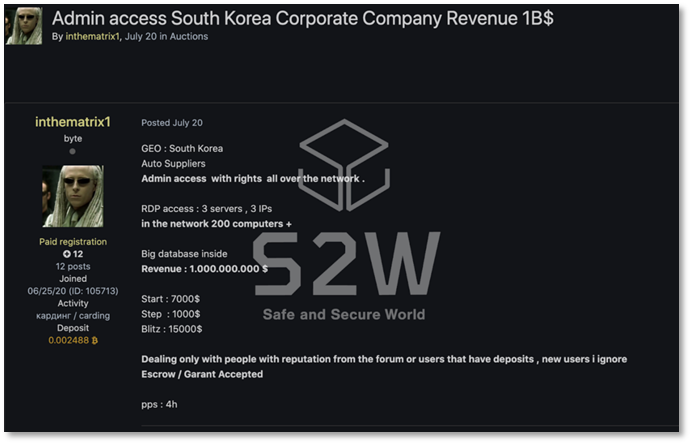 Example 1
Example 1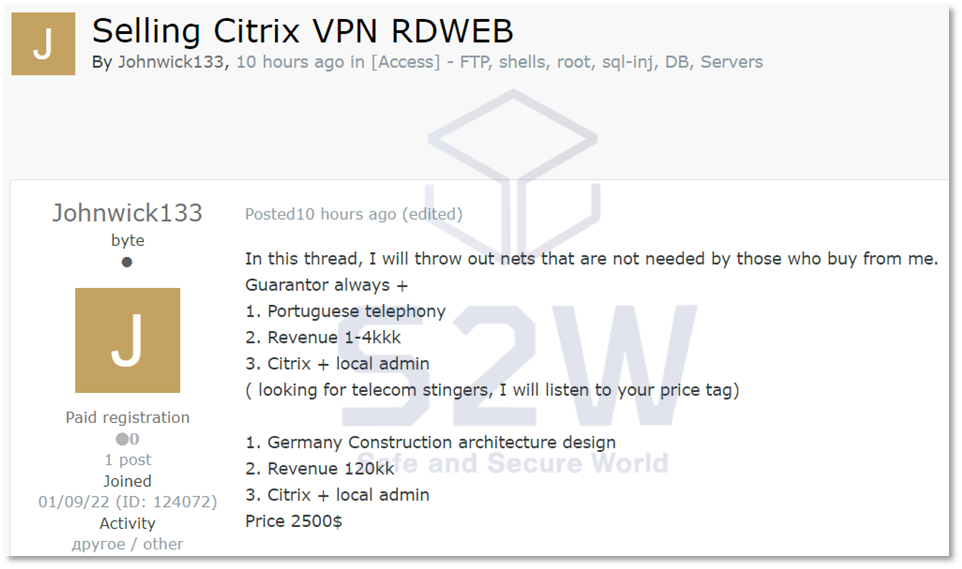 Example 2
Example 2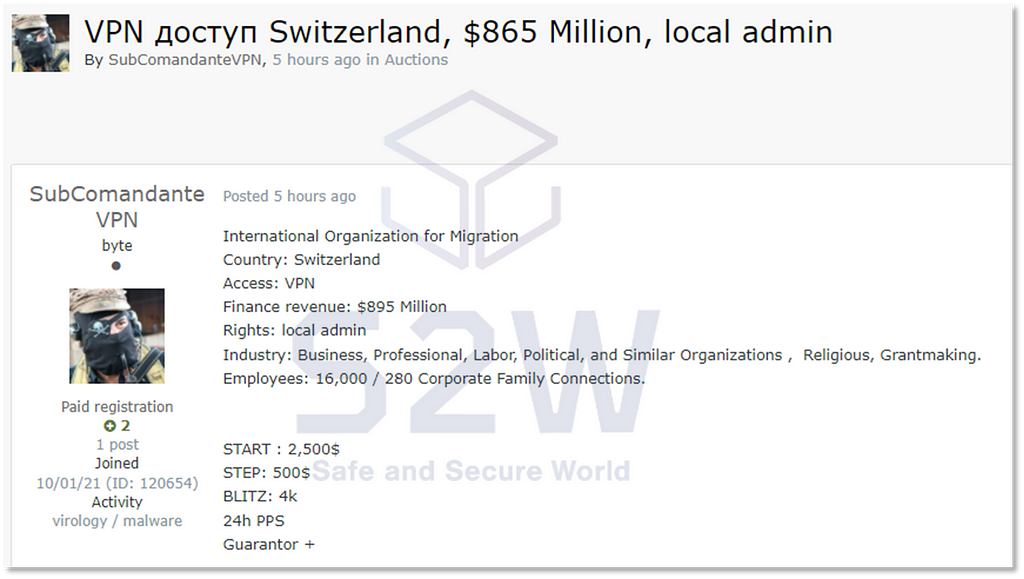 Example 3
Example 3[Appendix] Seller’s information
→ Majority of the posts are sold by a few ‘professional’ personnel.
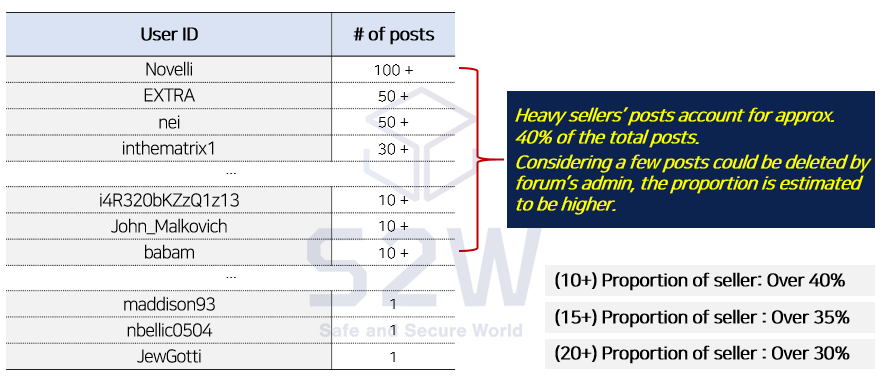
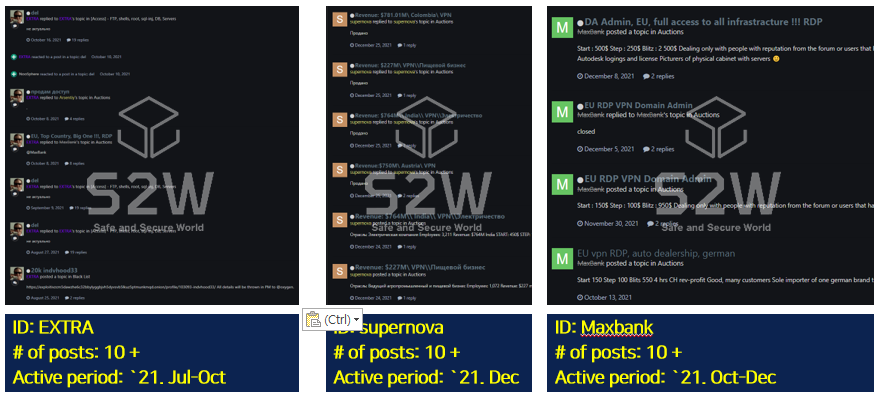
A few gangs posts dramatic number of posts in the course of short period, then stay non-active
→ Heavy sellers often show the characteristics of their specialty, industry, and region of the affected company.
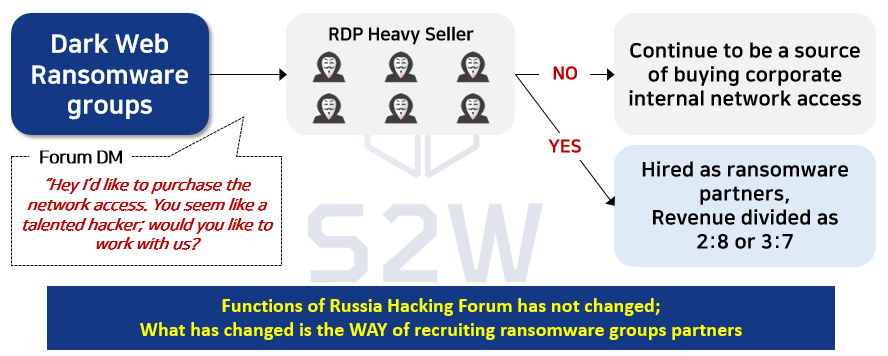
It is estimated that heavy RDP sellers are being used as a great source for the ransomware group
→ Ransomware groups continue to receive attack targets through heavy sellers, some of whom will be hired as partners, which brings ransomware groups with more power to continue engaging in aggressive activities.
[Darkpedia] Russian hacking forum, how has it changed after Colonial Pipeline was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: [Darkpedia] Russian hacking forum, how has it changed after Colonial Pipeline | by Darkpedia | S2W BLOG | Medium