As the value of cryptocurrency continues to rise, a new form of malware has grown in popularity: crypto-malware. Though “crypto” may seem like a buzzword that’s popping up everywhere, it is very real when it comes to cyber threats. Crypto-malware is one of the latest malware threats, and it’s particularly insidious because it only requires CPU cycles to do its best work. It is classified as a “silent threat” – the longer it remains undetected, the better it is for the criminal.
As the value of cryptocurrency continues to rise, a new form of malware has grown in popularity: crypto-malware. Though “crypto” may seem like a buzzword that’s popping up everywhere, it is very real when it comes to cyber threats. Crypto-malware is one of the latest malware threats, and it’s particularly insidious because it only requires CPU cycles to do its best work. It is classified as a “silent threat” – the longer it remains undetected, the better it is for the criminal.
For most businesses, the first step towards protection is understanding. Yet, with all of the new crypto terminology, it can be difficult to grasp what’s what when it comes to crypto-based threats. For example, what is crypto-malware? And what is cryptojacking? How do they relate to cryptomining?
In this post, we will talk about all things crypto (with the exception, perhaps, of cryptokitties), discuss the dangers of crypto-malware, and discuss how your organization can best protect itself from this rapidly emerging threat.
Crypto Terms Defined
Before we go any further, there are some important terms that need to be defined. As the crypto industry has grown, new terminology has been invented, and many of these terms can seem very similar.
- Cryptocurrency. This is what most people associate with crypto technology: a type of currency that is based on a cryptographic algorithm. While the vast majority of cryptocurrency is used for legitimate reasons, cryptocurrency also has become the preferred currency of cybercriminals because some of the currencies can’t be traced. Bitcoin is one of the most popular cryptocurrencies, but Monero has become popular among cybercriminals.
- Crypto Exchange. This is where a cryptocurrency is exchanged. If you want to turn USD into Bitcoin, a crypto exchange is where you might need to go. These crypto exchanges, often ironically, frequently have poor security in place, resulting in them being regular targets for attack.
- Cryptomining. This is the process of creating a unit of cryptocurrency. Popular cryptocurrencies are based on high-level mathematical problems that have to be solved. When these problems are solved, it creates an additional unit of that currency that can be traded. In essence, it turns work into money.
- Criminal Cryptomining. The process of mining cryptocurrencies is typically legitimate and legal. But criminals have gotten into the act with various techniques for using someone else’s computer to mine cryptocurrency to their benefit. One technique is to install a malicious payload (see crypto-malware below) into a victim’s computer that diverts CPU processing time to cryptocurrency mining, which doesn’t really do any harm to the computer or data, but can dramatically slow down performance.
- Crypto-malware. This is the program that is actually performing the criminal cryptomining. Crypto-malware is one of the latest malware threats, and it’s particularly insidious because, unlike ransomware, it can go about doing its work completely undetected. The goal of a crypto-malware isn’t to steal data – it is to remain in place for as long as possible, quietly mining in the background.
- Cryptojacking. This is a specific form of criminal cryptomining that temporarily hijacks victims’ systems via web servers and web browsers. Javascript is injected into vulnerable web servers so that when a user visits that webpage, the Javascript is run in their browser, turning the computer into a cryptominer. When the visitor leaves the webpage, the browser returns to normal, so the criminal is mining cryptocurrency only as long as the user keeps the infected webpage open.
- Mining Pool. This is an assortment of devices that are all being used together to mine the same “block” or mathematical problem for currency; it is a shared system that is often used due to the extreme amounts of work that it may take to make money.
- Ransomware. This is a type of malicious program that is designed to encrypt a system and its files, asking for a ransom to return, or decrypt, them. It is included here because many ransomware programs ask for payment in cryptocurrency.
Are Attacks Based on Crypto Technology Really a Threat?
While cyberattacks that use crypto technology have been getting a lot of buzz lately, that doesn’t necessarily mean they present a clear and present threat to businesses.
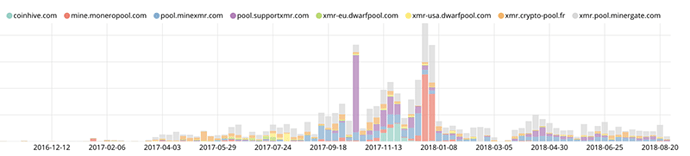
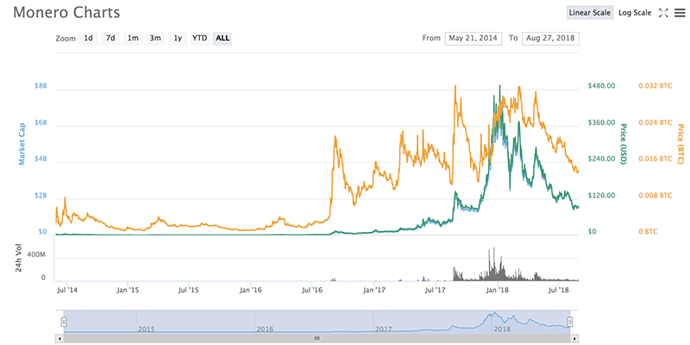
In late 2017, attacks against certain mining pools increased dramatically (see Figure 1), coinciding with the sudden rise of Monero (see Figure 2). Not too long after that, however, attacks dropped right back down again in Q1 2018, presumably as security systems added protection to block the crypto-malware network connections.
Figure 2: Market Cap and Volume of Monero.
While the threat of cryptojacking is not as big as it was at the end of 2017 and the beginning of 2018, these attacks are still more common than they were before the rise of Monero. On top of that, as new strains of crypto-malware are created and new cryptocurrencies rise in popularity among bad actors, we may very well see more of these types of attacks.
Crypto-malware vs. Ransomware
Ransomware is becoming less common due to the rise of criminal cryptomining, though it is unlikely to ever go away completely. Both ransomware and crypto-malware are designed with a simple goal in mind: making money initially in the form of cryptocurrency, which can then be used as an exchangeable commodity.
However, crypto-malware as a whole may be more effective. Ransomware requires that someone pay the ransom, while crypto-malware can operate indefinitely on a system, benefiting the criminal without the victim having to do anything, and may never be noticed. Thus, a criminal attacker may be virtually guaranteed some amount of returns with crypto-malware while ransomware had no guarantee of paying off.
Crypto-malware can also impact the DDoS market. Instead of botnet CPUs being used to generate packets to blackmail the victim, who may or may not pay the ransom, the DDoS botnet could be repurposed to mine cryptocurrencies, guaranteeing a payoff for the criminal.
Having said that, don’t expect ransomware to go away; it’s still a strategy that works for criminals. Like crypto-malware, it takes very little in terms of resources and time for malicious attackers to send ransomware out to new targets. As long as some targets are still paying ransoms, it still presents a compelling opportunity for attackers to make money.
The Impact of Cryptojacking
Since criminal cryptomining and cryptojacking are generally not about stealing data, they may be easier for some to dismiss. However, mining cryptocurrency puts a substantial amount of wear on a system. It eats up bandwidth and processing power, thereby slowing down your systems and potentially impacting productivity as a result. Companies that ignore cryptomining may see the graphics cards in their computers die, the processors burn out, or the memory starting to act erratically.
Crypto-malware is insidious because it often goes undetected for long periods of time. Crypto-malware may be, for example, hidden within other useful programs, and consequently, the user may never notice that their system has been impacted. As a program or application runs, it can be mining coins in the background.
Defending Against Crypto-Malware
Like many other forms of cyberattacks, all forms of criminal cryptomining relies on some form of malicious payload. A behavioral intelligence solution will be able to identify and block the payload from initially being installed. For threats that have already found their way onto a system (e.g., through social engineering, phishing, or an unprotected gateway), an AI driven counter intrusion platform can recognize the anomalous signals of cryptocurrency being mined, and initiate an appropriate incident response.
The post Crypto-malware – A Look At The Latest Malware Threat appeared first on Lastline.
Article Link: https://www.lastline.com/blog/crypto-malware-a-look-at-the-latest-malware-threat/