Co-Authored by Adrian Tirados and Sean Dixon
Across various facets of cybersecurity, capture the flag (CTF) competitions come in many forms.
To red team-focused security practitioners, a CTF refers to attack and defense competitions like the DEF CON CTF, in which teams of sophisticated pen testers and reverse engineers try to break into their opponents’ machines to attain flags while also patching their own systems against possible attacks. To students of SANS security courses, a CTF refers to the SANS NetWars competitions, in which individuals are given a digital environment and clues on what security tools to use in order to find flags to submit.
In both cases, flags are submitted to a judge or scoreboard that determines the number of points awarded per flag. However, most capture the flag competitions (which rely heavily on vulnerability detection, fuzzing, application injects, penetration testing, and even cryptography) lack challenges for OSINT or cyber threat intelligence professionals to participate in.
Knowing this, we wanted to conduct a CTF that offered a different perspective. At the seventh annual Recorded Future User Network (RFUN) conference, held in October of this year, we decided to launch a pilot program featuring our first threat intelligence CTF. To accomplish this, we created a fake breach conducted by an invented threat actor and set up breadcrumbs for analysts to follow. Here’s how it turned out.
The Threat Intelligence CTF Scenario
Our CTF was partially inspired by DEF CON’s iCTF (not to be confused with the attack and defense competition described above). Our overall goal was to have contestants start with only a Twitter post and server logs from a breach, and then follow hints given to them by a scoreboard (using Recorded Future) and eventually identify the actor behind the breach.

We began the competition by creating a fake actor, Gregory. We decided that he was going to be a native English speaker who had traveled abroad to Beijing in 2008, and was now using his technical knowledge and Mandarin language skills to sell stolen data on the internet. Gregory had multiple email and Twitter accounts, a Jabber account, and handles set up on multiple forums. After all of the accounts had been set up, we started posting using the accounts.
This individual had one personal Twitter account under his real name, Gregory, and one business account under his nom-de-hack, “Zao_An.” While Gregory would retweet English and Chinese news sources, as well as ask for technical advice, Zao_An would post about his exploits and which forums he was active on. Zao_An was also active on Pastebin, YouTube, and three underground forums, and we made sure that he left a few OPSEC mistakes within his posts. We ingested a majority (but not all) of the actor’s posts from various forums into Recorded Future, put hints on our scoreboard, and set up our flags for contestants to find.
Scenario
A Recorded Future client company, “Recorded Furniture,” has been breached! The only initial indicator is a tweet claiming to sell their company data. The contestants were initially given the following items:
- A link to @zao_An’s Twitter account containing the tweet below
- Server logs from the company’s webserver and database
- A link to the RFUN CTF scoreboard

The CTF Flags
1. Get the C2 server.
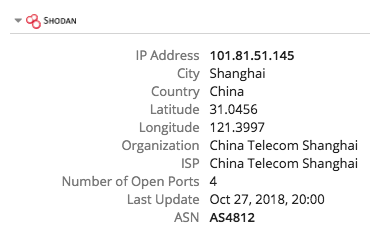
Flag: FLAG{101.81.51.145}
Information Gleaned: Infection vector, C2 server, some connection to a Chinese VPN
Contestants could determine from the server logs that the attack was conducted from the host 101.81.51.145 in China, which also served as the C2 server. The attack was launched via Metasploit and leveraged communications over port 4444. Within the Recorded Future Intelligence Card for this IP address, the Shodan integration in the product shows that 101.81.51.145 is a known VPN host.
2. Never paste(bin) your code.
Flag: FLAG{IJustWantToExpressMyself}
Information Gleaned: Code used to steal information, multiple user accounts
Contestants discovered that the server was reaching out to an IP belonging to Pastebin. Additionally, by searching for @zao_An as an actor on PasteBin within the Recorded Future product, contestants found some code in a deleted paste, which seemed to be post-exploitation code. The same code contained a video link describing the actor’s “favorite” Metasploit exploit — likely the same one used in the attack. The flag was in the YouTube video description.

3. My Twitter game is hen hao.
Flag: FLAG{winning the flag}
Information Gleaned: Actor’s personal information and language skills
By going to the originally linked Twitter page, contestants realized that the actor has a personal motto — “FLAG{旗开得胜}.” However, Twitter’s translation function does not give the correct English translation for the answer, and it was up to the analyst to ensure that the actor’s original meaning was maintained in order to obtain the correct answer, either through understanding the language or by using a different translation function.
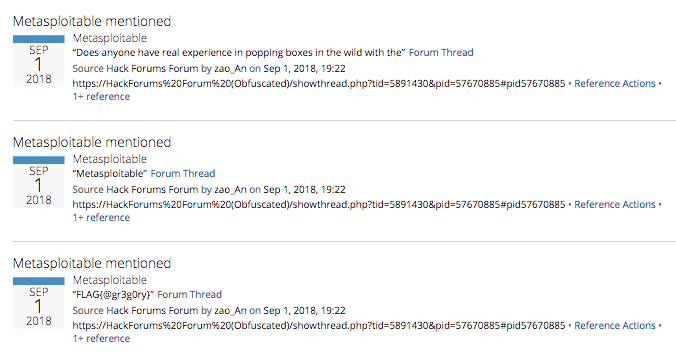
4. Always read the forum comments.
Flag: FLAG{@gr3gory}
Information Gleaned: Additional forum accounts, forum history and specialty
Although contestants could find that Zao_An was active on Chinese hacking forums (and mentioned one in his original tweet), contestants searching for the actor within the Recorded Future product discovered that Zao_An also had a similar handle on Hack Forums, a lower-level, English-speaking forum. By looking through Zao_An’s posts within the product, contestants could see that Zao_An asked about Metasploit and requested access to Chinese underground forums. Contestants were able to find a flag in one of the posts that revealed Zao_An’s personal Twitter handle.
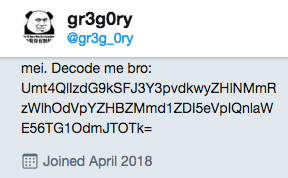
5. If at first you don’t decode, try, try again.
Flag: FLAG{https://gr3glesnewich.wordpress.com}
Information Gleaned: True identity of actor
While the original handle, @gr3g0ry, did not seem to be the actor the contestants are looking for, a similar handle, @gr3g_0ry, appeared likely to be someone like Zao_An, if not the same person. @gr3g_0ry’s tweets indicated that he is a rather inexperienced, English-speaking hacker. His bio contains a base64 string that reveals the flag when decoded twice. The WordPress link within the flag revealed that Gregory, a native English speaker, is interested in hacking and traveled to Beijing in 2008.
6, 7. What happened?
Flag: FLAG{BAD-ACTORS-ARE-MISUNDERSTOOD}, FLAG{RFUN-APPROVED}
By sending a short write-up on the actor and the breach with all of the IOCs and handles from the actor found to the CTF admins, contestants had the chance to receive the above two flags.
8. ET phone home.
Flag: FLAG{JabberingOnAndOn}
If the CTF admins returned the write-up claiming that it was insufficient, contestants could get a separate flag by engaging directly with the actor on Jabber.
The RFUN CTF Results
We ran this capture the flag competition at RFUN over the course of 29 hours. We opened email signups at noon the first day of the conference, started the competition at 5:00 PM, and closed the competition at 5:00 PM the next day (although our scoreboard showed one individual trying to score points even after the prizes had been given out).
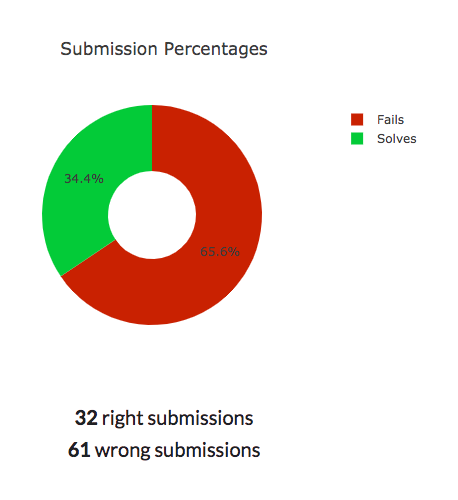
Running the numbers, we’d call this pilot CTF a success. We had 31 signups, 15 contestants register on the scoreboard, 10 contestants with answers on the board, and ultimately, one winner — someone who stayed up until 2:30 AM the first day to complete the entire challenge! The answers seemed to be the perfect balance of difficulty, as well — for every correct answer, each contestant averaged around two incorrect submissions.
Parting Thoughts
Capture the flag competitions, regardless of format, can act as accurate simulations of real-world scenarios. While the actor Zao_An was fake, actors like him exist in various forums, seeking to learn how to penetrate vulnerable systems. Thus, participating in competitions like this one is a low-risk method for analysts to develop their skill sets and keep their minds sharp.
We hope to expand this capture the flag competition at RFUN in the coming years and provide more time during the conference to play. Crafting the scenario was incredibly enjoyable, and we hope that our competitors had fun playing!
The post Creating a Threat Intelligence Capture the Flag Competition: An Overview appeared first on Recorded Future.
Article Link: https://www.recordedfuture.com/capture-the-flag-overview/