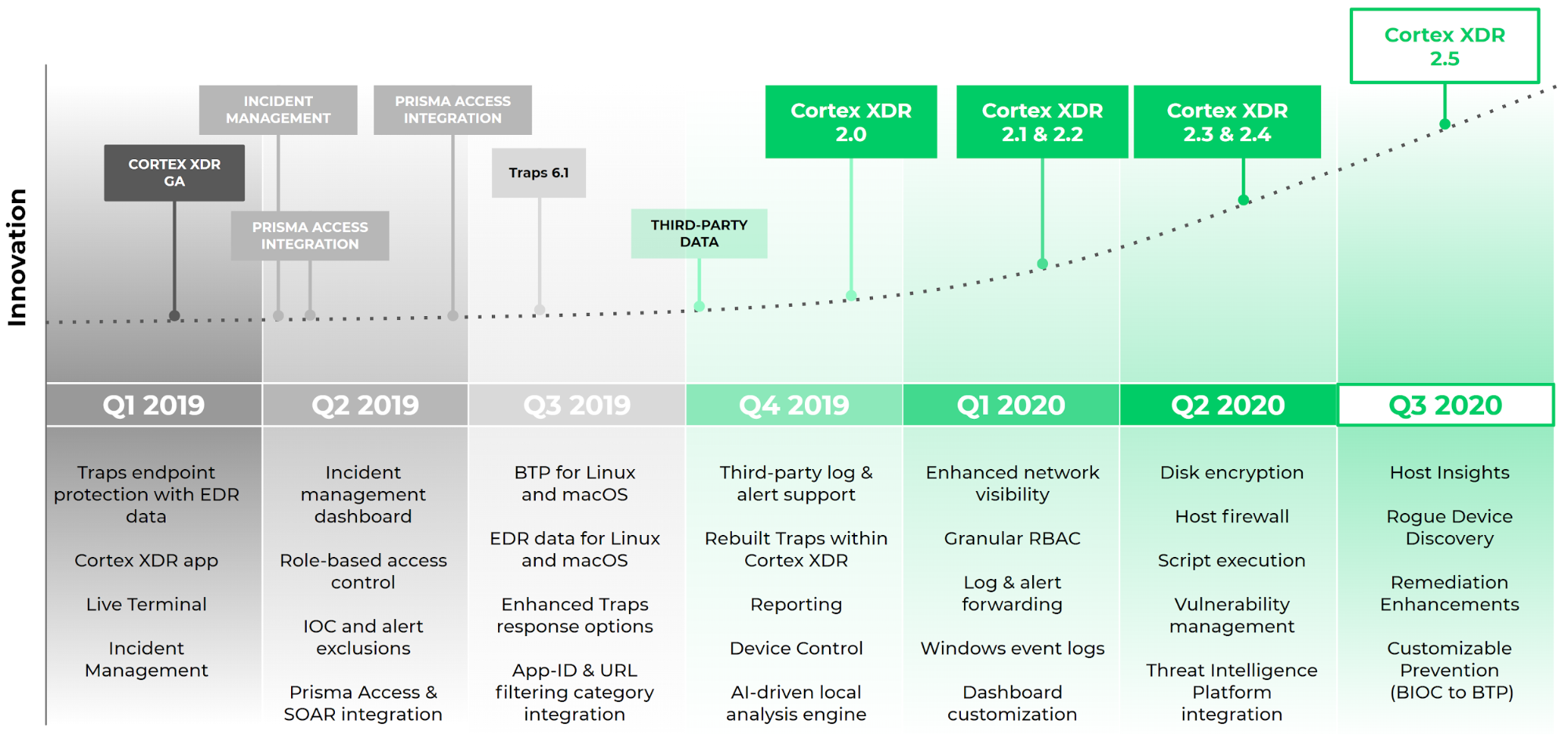
When we launched Cortex XDR a year and a half ago, we upended a status quo of siloed security tools by introducing the industry’s first extended detection and response platform. But that was only the beginning. As part of our commitment to deliver the world’s best detection and response platform, we continue to listen to your needs and invest heavily in product innovation, building new features to help your security team root out advanced adversaries and simplify operations.
We’re excited to share the launch of Cortex XDR 2.5, which introduces a massive list of new host visibility and protection capabilities to help your team further bolster endpoint security and streamline operations.
A timeline of innovation since Cortex XDR was introduced in March 2019.
What’s New in Cortex XDR 2.5
Over the past several months, we’ve talked to security professionals like you to understand the challenges you face finding, containing and recovering from threats, and we believe we’ve introduced a robust set of features to solve these challenges. Take a look – we think you’ll like what you see!
Key Features in Cortex XDR 2.5:
- Host Insights module.
- Asset management with rogue device discovery.
- Host restore.
- Closed-loop prevention.
- Expanded protection for macOS endpoints.
- New Asset View and enhanced Hash View.
Host Insights for Unprecedented Visibility and Swift Response
Safeguarding your endpoints starts with getting a clear picture of all your endpoint settings and contents and understanding your risks. Once you’ve identified a threat, you need to stop it quickly and ensure it hasn’t spread to multiple endpoints.
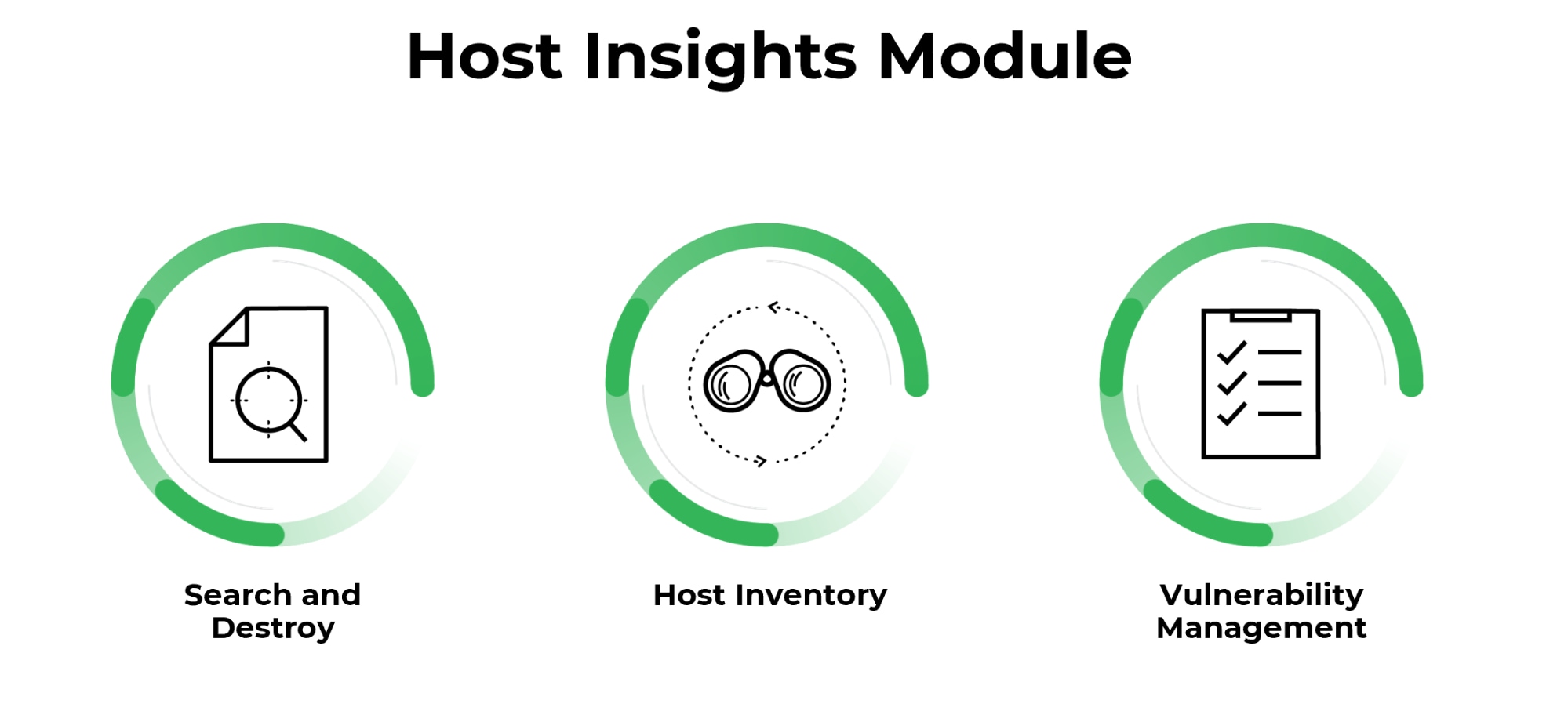
With Host Insights, an add-on module for Cortex XDR, you get all these capabilities and more. Host Insights combines vulnerability management, application and system visibility, along with a powerful Search and Destroy feature to help you identify and contain threats. Host Insights offers a holistic approach to endpoint visibility and attack containment, helping reduce your exposure to threats so you can avoid future breaches.
Host Insights is available to all Cortex XDR Pro per Endpoint customers during a Community Access period. After the Community Access period, customers will be able to purchase the Host Insights Module.
Here’s what the Host Insights module provides:
Search and Destroy enables you to instantly find and eradicate threats across all endpoints. This powerful feature indexes all the files on your managed Windows endpoints so you can sweep your entire organization to find and remove malicious files in real time. Granular settings allow you to exclude files and directories on specific hosts.
Host inventory lets you identify security gaps and improve your defensive posture with complete visibility across key Windows host settings and files. You can view information about users, groups, applications, services, drivers, autoruns, shares, disks and system settings. By getting all your host details in one place, you can quickly identify IT and security issues in your environment.
Vulnerability Management provides you real-time visibility into vulnerability exposure and current patch levels across all endpoints to prioritize mitigation. Cortex XDR 2.5 reveals the vulnerabilities on your Linux endpoints, with up-to-date severity information provided by the NIST National Vulnerability Database. You can also see the Microsoft Windows Knowledge Base (KB) updates installed on your endpoints.
Asset Management With Comprehensive Rogue Device Discovery
To shield your endpoints from threats, you need to know what devices are on your network at any point in time.
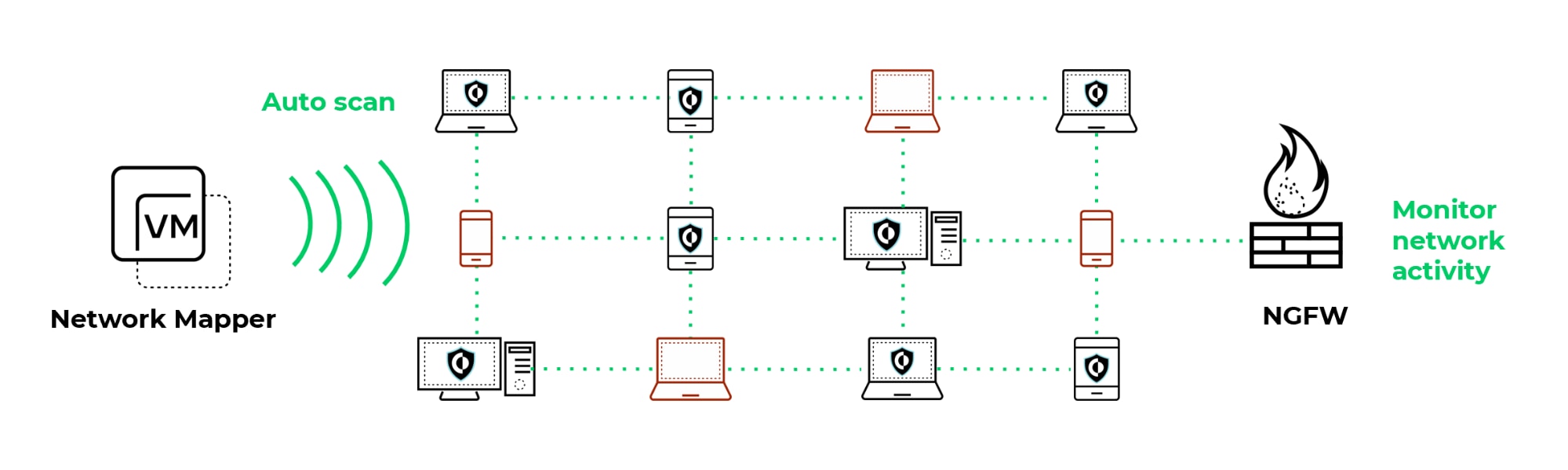
Cortex XDR has introduced a new Asset Management feature that streamlines network management and reveals potential threats by showing you all the devices in your environment, including managed and unmanaged devices. After you’ve defined your network segments, Cortex XDR goes to work assembling a list of assets including the associated IP address, the host name, when the asset was observed on the network and whether it is managed by the Cortex XDR agent.
But what really sets Cortex XDR apart from traditional solutions is that it combines proactive scans with monitoring of endpoint, network and third-party data to deliver comprehensive rogue device discovery. Cortex XDR uses a Network Mapper to scan for every endpoint on your network. It also detects hosts that evade scans by analyzing network traffic and authentication logs. As a result, you get a view of your entire environment.
Cortex XDR combines proactive scans from our Network Mapper with network monitoring to reveal all the devices in your network.
Host Restore for Swift Attack Recovery
When attacks occur, you need to restore compromised hosts quickly. All too often, this means re-imaging affected endpoints. But wiping endpoints back to their original state can impact user productivity as employees attempt to recover files and reapply their personal settings. To minimize business disruption, you need a way to quickly reverse all the elements of an attack without deleting user files and data.
Cortex XDR’s new host restore feature allows you to speed recovery and revert to a clean state easily. Remediation suggestions simplify response by recommending next steps and allowing you to resolve all activities identified in an incident. You can rapidly recover from an attack by removing malicious files and registry keys, as well as restoring damaged files and registry keys – without re-imaging or building custom scripts.
Closed-loop Prevention to Granularly Block Threats
Once you’ve developed a set of laser-accurate detection rules, you may not want to wait for your analysts to manually triage and respond to attacks.
With Cortex XDR 2.5, you can transform granular custom detection rules into automated protections to stop complex threats. You can even copy and edit out-of-the-box detection policies and convert them into prevention policies, called Behavioral Threat Protection rules. Cortex XDR allows you to build laser precise prevention rules based on any endpoint behavior or attribute. Before you push prevention rules to your agents, you can gain confidence that your rules will accurately block attacks by testing rules against real-world data.
Expanded Protection for macOS Endpoints
The new Cortex XDR agent 7.2 introduces end-to-end protection capabilities for macOS endpoints that lower the risk of data loss, reduce the attack surface of your endpoints, and help satisfy certain data security compliance requirements, such as those found in the PCI standard or regulations that call for encryption. These powerful capabilities augment existing endpoint protection for Windows endpoints.
New endpoint security features for macOS include:
- A host firewall with location-based host firewall rules.
- Disk encryption using FileVault.
- Device control for USB-connected devices.
- DMG file analysis.
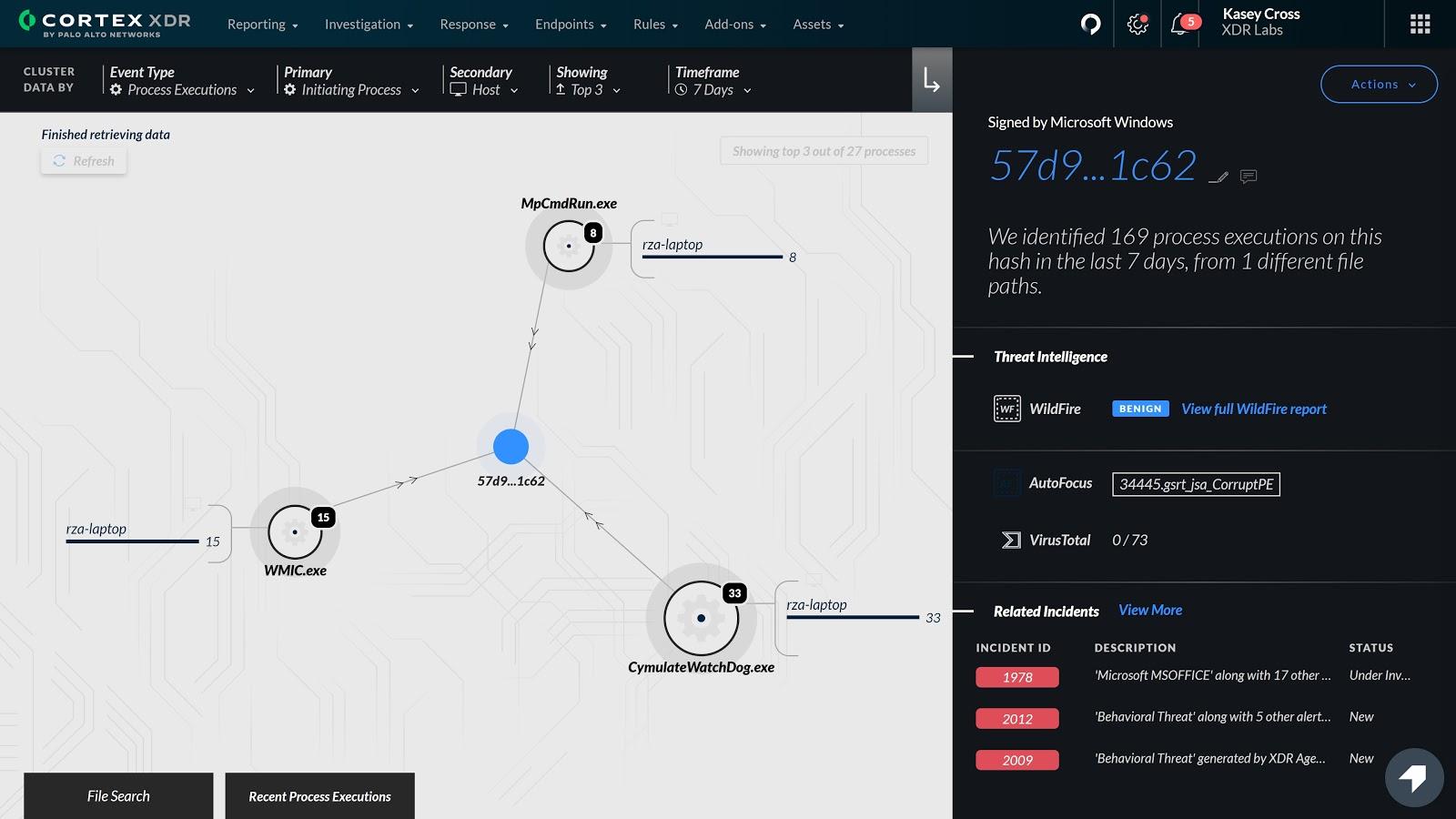
New Asset View and Enhanced Hash View for Fast-tracked Investigations
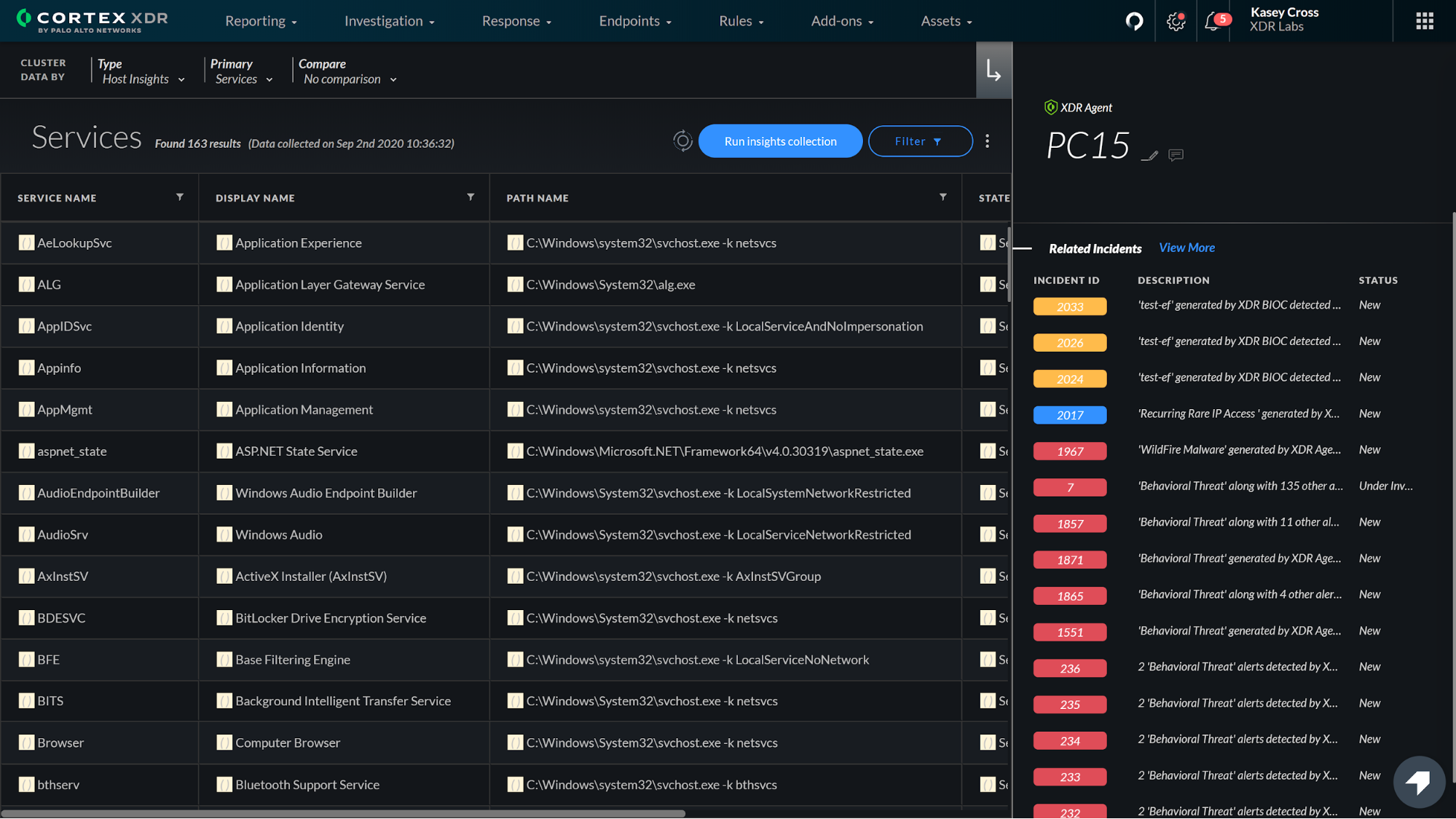
You need rich investigative details at your fingertips to quickly analyze and respond to threats. To augment Host Insights, we’ve introduced a new Asset View that displays the related incidents and information about a specific host, including services, users, groups, shares and more. Armed with this knowledge, your analysts can quickly determine if a host is compromised and review all the activity involving the host to assess the scope of an attack.
The Asset View reveals host and incident information to help you expedite investigations.We have also updated the Hash View to provide 360-degree visibility into files, while maintaining a consistent format with our IP View and Asset View displays.
The Hash View shows essential threat intelligence, incident and process information in one consolidated view.…But wait, there’s more. We’ve also added:
-
- Web shell exploit protection for Linux.
- Cryptomining protection for Linux.
- “Agentless” EDR that deploys a non-persistent data collector for up to two weeks to endpoints that have triggered an alert.
- Enhanced analytics with more flexible alert exceptions, improved alert accuracy and a shorter baselining period before analytics alerts are triggered.
- Management and usability enhancements to improve investigations.
For a complete list of new features in Cortex XDR 2.5, see the Cortex XDR release notes. See Cortex XDR licenses to find out which features are available with Cortex XDR Prevent, Cortex XDR Pro per Endpoint and Cortex XDR Pro per TB.
If you want to see Cortex XDR 2.5 in action, sign up for our Sept. 29 webinar, “Cortex XDR 2.5: Future-Proofed Security Operations.”
The post Cortex XDR 2.5: Future-Proofed Security Operations With Host Insights appeared first on Palo Alto Networks Blog.
Article Link: http://feedproxy.google.com/~r/PaloAltoNetworks/~3/YFqk7-5lMGw/