 The cyber risks posed by vulnerable internal, open-source and third-party software that make up a modern supply chain are a source of intense concern for both for development teams and security operations centers within enterprises, according to a recent Dimensional Research survey of more than 321 IT professionals commissioned by ReversingLabs.
The cyber risks posed by vulnerable internal, open-source and third-party software that make up a modern supply chain are a source of intense concern for both for development teams and security operations centers within enterprises, according to a recent Dimensional Research survey of more than 321 IT professionals commissioned by ReversingLabs.
The ReversingLabs Software Supply Chain Risk Survey polled executives and IT professionals responsible for software at enterprise-scale companies. Respondents were split between North America (67%) and Europe (33%), with a plurality working in technology (19%), financial services (13%), healthcare (9%) and telecommunications (8%).
The findings underscore the growing alarm over a perceived protection gap within both software development firms and their customers as software supply chain attacks and breaches such as the 2020 SolarWinds attack, or the more recent compromise at voice over IP (VoIP) vendor 3CX, become more common.
Here are four key insights from the survey.
[ See and share the related infographic | Plus, see the related report: Why Traditional App Sec Testing Fails on Supply Chain Security and its sister Webinar ]
1. Software supply chain risks are a major issue
The risks posed by the software supply chain loomed large for most survey respondents.
Eighty eight percent of respondents said that software supply chain security presented an “enterprise-wide risk” to their organization, while nearly two thirds (65%) said their organization’s software supply chain security program was not as mature as it should be.

Close to 9 in 10 (87%) respondents said their company detected software issues in its software supply chain in the last 12 months. Those risks came from a variety of sources, including internally developed software, software licensed from third-party suppliers, and open-source software.

Most organizations focus on vulnerabilities when assessing software supply chain risk, but that understanding of cyber risk is broadening. Asked what issues pose the biggest business risk to their organizations 82% of respondents cited software containing vulnerabilities, but other, less visible software risks ranked high as well. Fifty-five percent cited the exposure of secrets such as sensitive information, access tokens and credentials in software code, followed by malicious code (52%) and suspicious code (46%) inserted into applications.
Software vulnerabilities in code were also the most common issue survey takers reported, with 65% listing them as an issue they encountered in the last 12 months. But respondents also cited certificate misconfigurations (37%), exposed secrets (25%) and suspicious code (24%) as common issues that have affected their organizations' software supply chains.
2. Those risks go beyond open source
The complexity of the software supply chain security picture reflects the complexity of modern software development. Most respondents said their organizations relied on non-employees to help them develop software, including contractors (67%) and third-party software development firms (59%). And their organizations relied on internally developed (82%), commercial (79%) and open-source (74%) code in about equal measure.
When asked to name the source of software security issues such as tampering, vulnerabilities and malicious code, 70% pointed the finger at open-source software. But far fewer cited internally developed software (59%) or software developed by contractors and third parties (57%).
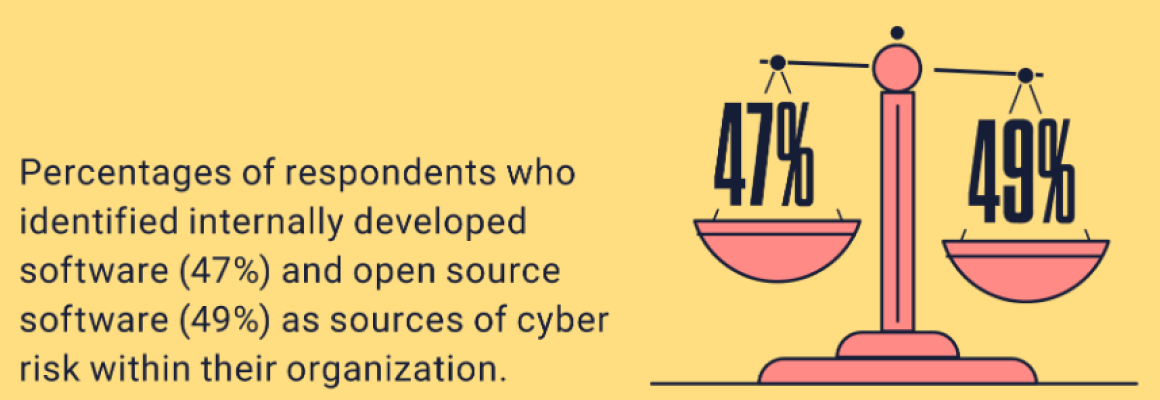
However, when asked to reflect on the issues within their own organizations, the picture was more mixed. Forty-seven percent said internally developed software was a major source of issues affecting their software supply chain, nearly as many as the 49% who named open-source software.
3. Companies are retooling to secure the software supply chain
Despite the prevalence of supply chain risk, enterprise defenses for supply chain risks and threats are not where they should be. Asked whether their organization’s software supply chain security (SSCS) program was “as mature as it should be,” nearly two thirds of survey respondents (65%) said no.

That could be the result of a tooling gap. Existing application security technologies such as static- and dynamic application security testing (SAST and DAST) focus on the problem of identifying software vulnerabilities in code under development. Software composition analysis (SCA) technology — another common application security tool — uses an inventory of the open-source modules used in enterprise code bases to root out issues related to licensing, compliance and code quality.
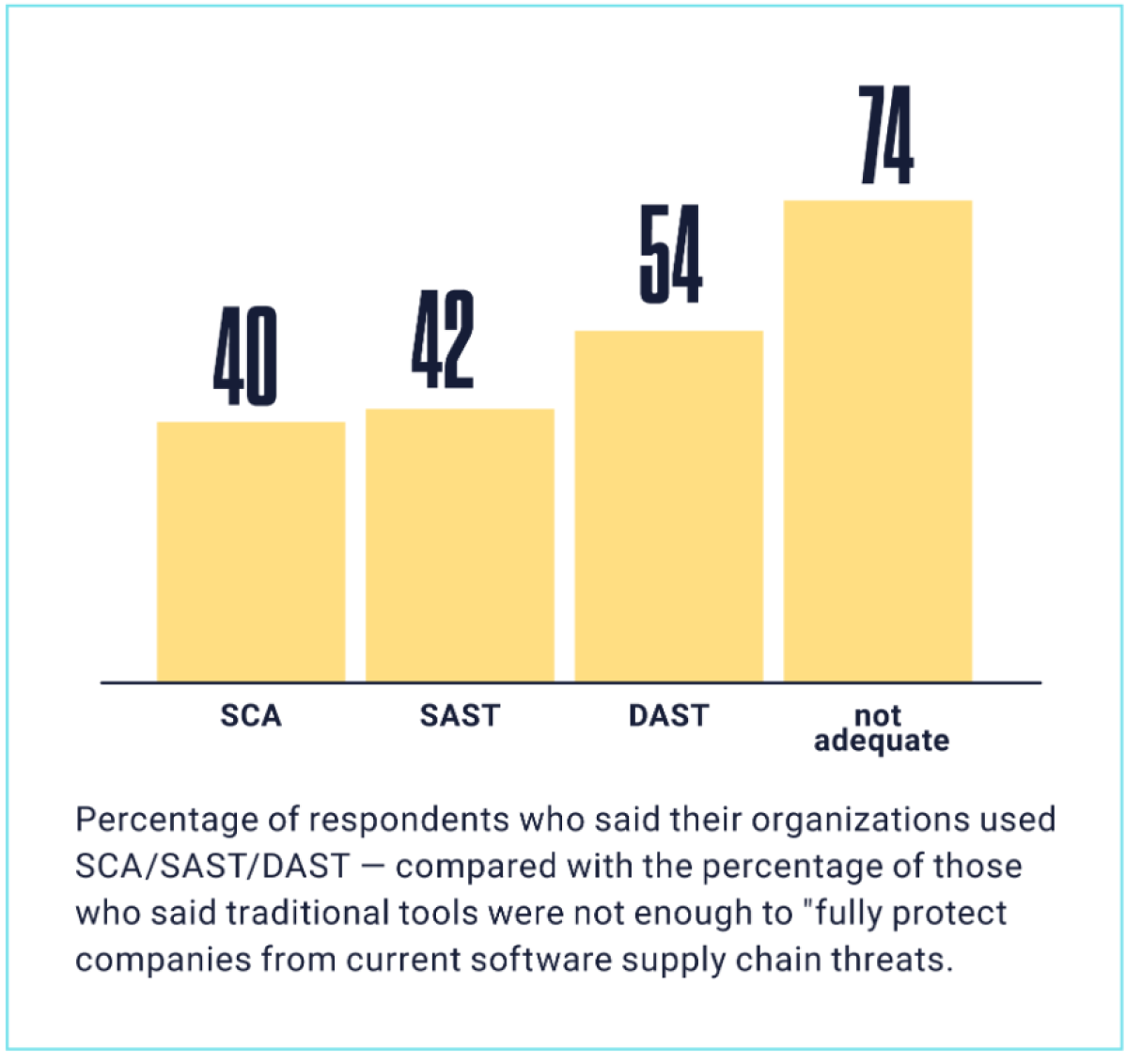
Both technologies are in wide use. More than half (54%) of respondents said their organization used SAST technology, 42% use DAST and 40% use SCA tools. But most survey respondents felt that that these legacy technologies aren’t adequate to address the full spectrum of supply chain risks. Asked whether SAST, DAST and SCA solutions “fully protect companies from current software supply chain threats,” 74% said “no.”
 Enterprises are already taking steps to address the gaps. Eighty percent of respondents said their organizations had an initiatives under way to improve software supply chain security. The exact shape those initiatives will take isn’t clear, but 70% of respondents said solutions to mitigate software supply chain threats were “extremely” or “moderately” important.
Enterprises are already taking steps to address the gaps. Eighty percent of respondents said their organizations had an initiatives under way to improve software supply chain security. The exact shape those initiatives will take isn’t clear, but 70% of respondents said solutions to mitigate software supply chain threats were “extremely” or “moderately” important.
Rising awareness is driving supply chain security changes
Current events are likely to drive even more attention to supply chain threats and attacks. IT professionals surveyed were showing a strong interest in supply chain security technologies before the recent revelations of a supply chain attack on the voice over IP firm 3CX, which led to compromises at several of that company’s customers.
Such attacks may in many cases be preventable. For example, a ReversingLabs analysis of the compromised software update to 3CX’s Windows and Mac OS desktop clients revealed clear signs of tampering. Had 3CX been able to detect those signs in advance, it it never would have released the update to customers.
Incidents like SolarWinds and 3CX have raised awareness of software supply chain risk, including threats posed by software tampering, malicious code and secrets exposure from public and private code repositories used in software development. Those high levels of awareness are just the beginning what's likely to be a much larger transformation in how enterprises handle software supply chain security.
[ See and share the related infographic | Plus, see the related report: Why Traditional App Sec Testing Fails on Supply Chain Security and its sister Webinar ]
Article Link: Companies scramble to cover software supply chain security gaps: 3 key survey takeaways