GermanWiper Ransomware was found distributed via spam email campaign in Germany. It’s a data-wiping malware and the ransom note was written in German language. The malware pretends to be ransomware but is actually a wiper that destroys the data instead of encrypting it.
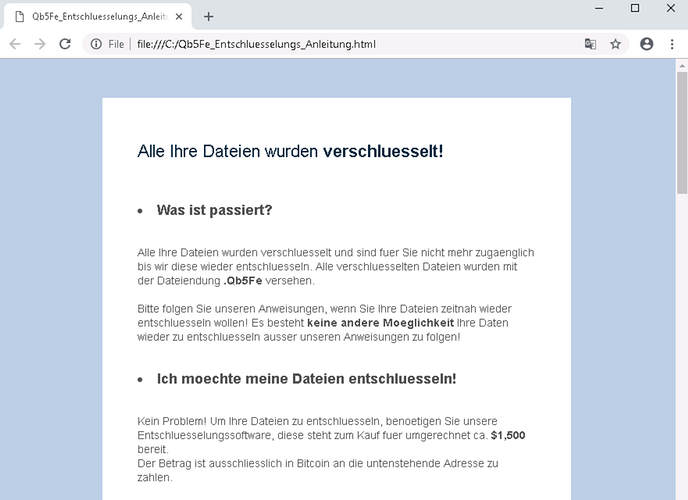
Figure 1: Screenshot of the ransom note
This post serves to inform our customers about detection and protection capabilities within the Carbon Black suite of products against GermanWiper ransomware.
Behavioral Summary
The detailed analysis of this malware is underway and a link will be found here once completed.
Unlike ransomware that encrypts data, German Wiper will overwrite the data content with null values and append five randomly generated characters as file extension to the wiped file.
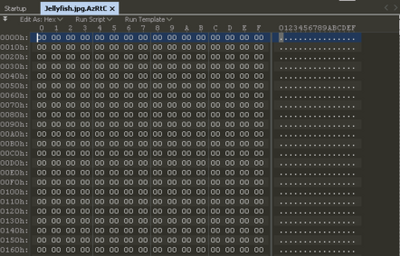
Figure 2: File wiped by GermanWiper
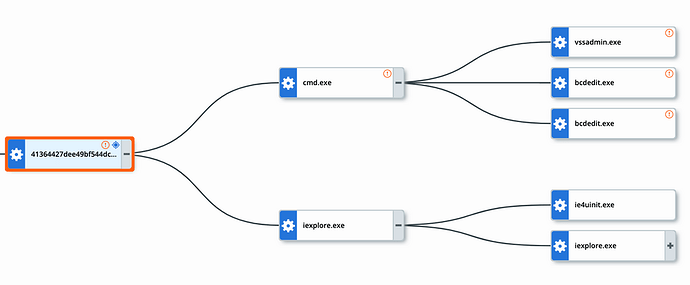
After that, it will perform the deletion of volume shadow copies and disable Windows automatic startup repair to ensure all the data cannot be restored easily with the following command:
“C:\Windows\System32\cmd.exe” /k vssadmin.exe delete shadows /all /quiet & bcdedit.exe /set {default} recoveryenabled no & bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
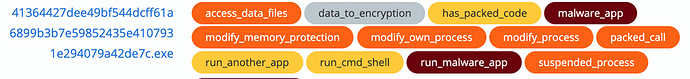
The following is the screenshot of CB Threat Hunter process chart by GermanWiper.
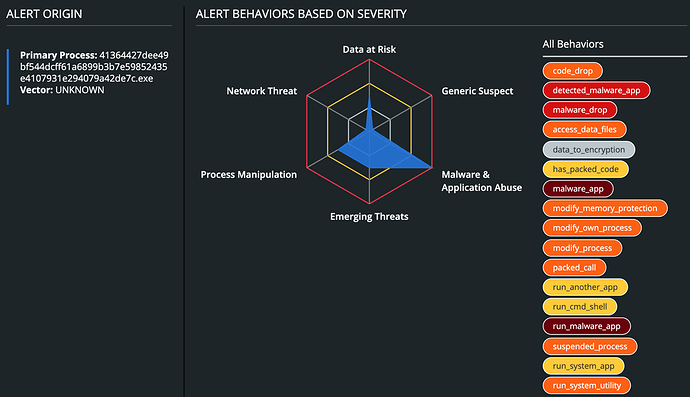
Other than that, CB Defense will display the malware’s overall triggered TTPs.
If you are customer looking to learn how CB solutions defend against this attack, click here.
Remediation:
MITRE ATT&CK TIDs
| TID | Tactic | Description |
|---|---|---|
| T1193 | Initial Access | Spearphishing Attachment: GermanWiper was delivered via spearphishing emails with malicious attachment |
| T1204 | Execution | User Execution: It delivered via spam email, then user to open the malicious attachment |
| T1086 | Execution | PowerShell: PowerShell command was executed to download malicious payload |
| T1083 | Discovery | File and Directory Discovery: It will scan file and directory during the encryption process |
| T1059 | Execution | Command-Line Interface: Cmd was used to execute vssadmin and bcdedit |
| T1107 | Defense Evasion | File Deletion: Shadow Copy Deletion by WMIC Or VSSAdmin |
| T1067 | Persistence | Bootkit: BCDEdit Or BCDBoot Use |
| T1485 | Impact | Data Destruction: GermanWiper will overwrite data |
| T1486 | Impact | Data Encrypted for Impact: Ransomware demands a ransom be paid for decrypting the file |
Indicators of Compromise (IOCs)
|
Indicator |
Type |
Context |
|
41364427dee49bf544dcff61a6899b3b7e59852435e4107931e294079a42de7c 36ccd442755d482900b57188ae3a89a7 |
SHA256 MD5 |
GermanWiper Ransomware |
|
7a0c1477bdde6eef3646fe8e4ba7b68c366ed9b1209799bc5d437a9320878602 901a3a1ff5182b5583be5745db98a9ce |
SHA256 MD5 |
Malicious Attachment (lnk file) |
|
8ecd960adaf6609eb8ed9ed46ccbeeb181d1e32f1cda016cde47e35f9748f716 eecef3ce3d40ad0c092183b6c4b0c0e5 |
SHA256 MD5 |
Malicious Attachment (zip file) |
|
6e7cb518f13564ae5a899d4cef77246eeae12ab1dc73b27d91af028e85232901 bc1ba6013db121e92548eaa24ee6fecd |
SHA256 MD5 |
Malicious Payload (hta file) |
The post CB TAU Threat Intelligence Notification: GermanWiper Ransomware appeared first on Carbon Black.
Article Link: https://www.carbonblack.com/2019/08/20/cb-tau-threat-intelligence-notification-germanwiper-ransomware/