MS-SQL servers are mainly the attack targets for Windows systems. Attackers scan vulnerable MS-SQL servers that are poorly managed and install malware upon gaining control. Malware strains installed by attackers include CoinMiner, ransomware, backdoor, etc., and may vary depending on the purpose of the attack.
 Figure 1. Types of malware that targeted MS-SQL in Q1 2022
Figure 1. Types of malware that targeted MS-SQL in Q1 2022
Most backdoor strains are remote control types such as Remcos RAT and Gh0st RAT, but there are also infiltration testing tools used to dominate companies’ internal systems such as Cobalt Strike and Meterpreter.
The attack case that will be later discussed in this post installs Cobalt Strike and Meterpreter in vulnerable MS-SQL servers to gain control. The attacker then installs AnyDesk to control the infected system in a remote desktop environment. As explained in the following blog post, the Kimsuky group also used Meterpreter to gain control and install VNC malware strains for remote desktop features. The group customized HVNC feature of TinyNuke released on GitHub, and TightVNC.
AnyDesk is a remote control application that is similar to that of TeamViewer, providing various features such as remote desktop and sending files. Remote desktop is a program that allows a user to remotely access an environment installed with RDP or AnyDesk and control it in the GUI environment.
 Figure 2. AnyDesk remote desktop application
Figure 2. AnyDesk remote desktop application
When a user has AnyDesk installed in its environment and there is external access to the system, a message pops up. If the user allows access, the system can be remotely controlled. There is another way to set password for AnyDesk. When another method is used, simply entering the password makes it possible to remotely control the system without the user’s permission. As such, AnyDesk is known to be used alongside Cobalt Strike by attackers wishing to dominate a company’s internal network, such as the Conti ransomware group.
The infected system shows various attack logs including Remcos RAT. It appears this particular system has been targeted by various attackers in the past as its account credentials were poorly managed. The following image shows AhnLab’s ASD (AhnLab Smart Defense) log of the attacker attempting to install Cobalt Strike.
 Figure 3. AhnLab’s ASD log for Cobalt Strike
Figure 3. AhnLab’s ASD log for Cobalt Strike
The attacker then installed Meterpreter. Meterpreter is an infiltration testing tool provided by Metasploit, a framework to test infiltration. Similar to Cobalt Strike, it is a backdoor that can perform various malicious behaviors by receiving commands from the attacker. The infected system shows Meterpreter’s Elevator DLL as shown below.
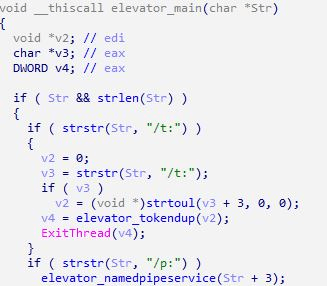 Figure 4. Meterpreter’s Elevator DLL created in the infected system
Figure 4. Meterpreter’s Elevator DLL created in the infected system
Elevator DLL is a DLL used to escalate privilege with system permission after Meterpreter is initially executed. It is used when the Dropper method is used among GetSystem commands.
 Figure 5. Privilege escalation command provided by Meterpreter
Figure 5. Privilege escalation command provided by Meterpreter
 Figure 6. Process tree of dropper-method GetSystem command
Figure 6. Process tree of dropper-method GetSystem command
After privilege escalation, Meterpreter operates in the rundll32.exe process and ultimately downloads and runs the powershell script that installs AnyDesk.
 Figure 7. Log of Meterpreter installing AnyDesk
Figure 7. Log of Meterpreter installing AnyDesk
The powershell script “wc.ps1” installed by Meterpreter installs AnyDesk in silent mode from the application’s official webpage and sets AnyDesk’s password as “wocaoybb”.
 Figure 8. Powershell routine for installing AnyDesk
Figure 8. Powershell routine for installing AnyDesk
If AnyDesk is installed on the infected system using the method mentioned above, the attacker can access the infected system and remotely control it without the user’s permission by entering a password.
 Figure 9. Logging in to the remote system installed with AnyDesk
Figure 9. Logging in to the remote system installed with AnyDesk
 Figure 10. Remote control using AnyDesk
Figure 10. Remote control using AnyDesk
Typical attacks that target database servers where account credentials are poorly being managed include brute force attacks and dictionary attacks. Although it seems like these methods make up the majority of the attacks, there can be other types of vulnerability attacks against systems where their vulnerability has not been patched.
Because of this, administrators should use passwords that are difficult to guess for their accounts and change them periodically to protect the database server from brute force attacks and dictionary attacks, and maintain the latest patch to prevent vulnerability attacks. They should also use security programs such as firewalls for database servers accessible from outside to restrict access of external attackers.
AhnLab’s anti-malware software, V3, detects and blocks the malware using the following aliases:
[File Detection]
– Malware/Win.Exploit.C5159648 (2022.06.05.01)
– Downloader/PowerShell.Generic (2022.06.27.02)
[Behavior Detection]
– Malware/MDP.Behavior.M2330
– Fileless/MDP.CobaltStrike.M3650
[Memory Detection]
– Backdoor/Win.CobaltStrike.XM78
[IOC]
MD5
Meterpreter Elevator DLL
– 5d3ae879e4bd09f824f48b49f4782e75
Powershell for installing AnyDesk
– 0863ab6d606dea63b76eaa846ca9effd
C&C
Download URL for powershell installing AnyDesk
– hxxp://3.101.101[.]56/wc.ps1
Cobalt Strike C&C
– hxxp://212.193.30[.]228:8080/a11
– hxxp://212.193.30[.]228:11280/ca
Meterpreter C&C
– 194.31.98[.]133:12443
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Case of Attack Exploiting AnyDesk Remote Tool (Cobalt Strike and Meterpreter) appeared first on ASEC BLOG.
Article Link: Case of Attack Exploiting AnyDesk Remote Tool (Cobalt Strike and Meterpreter) - ASEC BLOG