Attacks on the domain name system continue
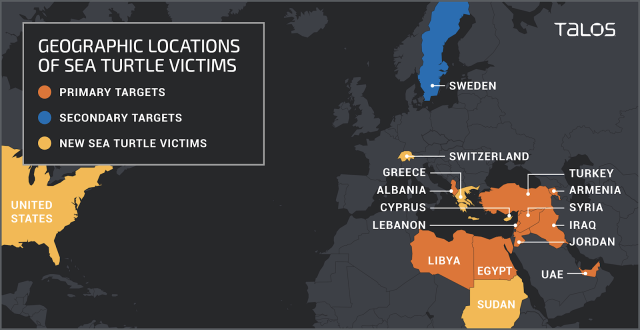
Talos, the intelligence group of CISCO reported in their blog that their monitoring shows that attacks on the domain name system (DNS) by “Sea Turtle” continue. The attack technique used is similar than before, the actors compromise name server records to take ownership of the domain. They then provide false information to selected parties (e.g certificate authorities, mail users) which leads to the disclosure of email credentials of the targeted organisations. These credentials give initial access to the victims E-mails accounts and other resources and are a starting point for further attacks.
Victims in Switzerland
For the first time, Talos also reported victims in Switzerland.
While Talos didn’t disclose the targeted organizations they identified these groups as primary targets:
- Government organizations
- Energy companies
- Think tanks
- International non-governmental organizations
- At least one airport
Technologies to defend against DNS hijacking attacks not widely used
While technologies to defend against these DNS hijacking exist, they where apparently not used by the victims.
Talos suggests the following mitigation methods based on a presentation by Bill Woodcock:
- Multi-factor authentication
- Using a registry lock service on your domain names
- DNSSEC sign your domains, either in-house, or using a DNS service provider which performs DNSSEC key-management services.
- DNSSEC validate all DNS lookups
- Make Internet Message Access Protocol (IMAP) email servers accessible only from your corporate LAN or VPN
Unfortunately most of these mitigation methods are not widely used in Switzerland. While multi-factor authentication is a good way to protect individual users, DNSSEC is a technology that protects the authenticity and integrity of domain name resolution. Unfortunately, only 4% of all .ch domain names are DNSSEC signed to protect their users, but the number is rising sharply as more and more DNS hosters in Switzerland offer DNSSEC signing to their customers. The number of ISPs that use DNSSEC validation is relatively low with 22% of all DNS responses in Switzerland being validated. Currently there is no registry lock for .ch and .li domain names available, but SWITCH is working on a solution.
Light at the end of the dark DNSSEC tunnel
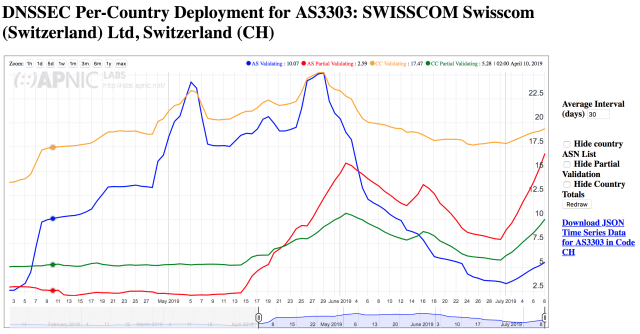
But there is also good news. Swisscom, Switzerlands largest ISP started validating DNS responses on its public reachable DNS resolvers 195.186.1.110/195.186.1.111 and 195.186.4.110/195.186.4.111 recently.
dig switch.ch @195.186.1.110; <<>> DiG 9.14.3 <<>> switch.ch @195.186.1.110
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 3002
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;switch.ch. IN A;; ANSWER SECTION:
switch.ch. 252 IN A 130.59.31.80;; Query time: 3 msec
;; SERVER: 195.186.1.110#53(195.186.1.110)
;; WHEN: Wed Jul 10 13:41:31 CEST 2019
;; MSG SIZE rcvd: 54
The ad flag shown on the highlighted line above indicates that the DNS resolver is DNSSEC validating the response
Due to its market share this also affects the total rate of DNSSEC validation in Switzerland as measured by APNIC:
The percentage of DNSSEC validation is Switzerland is rising, but below the European average. The same is true for the DNSSEC signing of .ch domain names, where Switzerland is far behind the leaders from Scandinavia and .nl, but we see clear improvements. With both trends continuing, we hopefully get a Domain Name System in Switzerland that offers better mitigation against DNS based attacks in the near future.
Article Link: https://securityblog.switch.ch/2019/07/10/attacks-on-dns-infrastructure-continue/