Earlier this month Check Point Research reported discovery of a 19 year old code execution vulnerability in the wildly popular WinRAR compression tool. Rarlab reports that that are over 500 million users of this program. While a patched version, 5.70, was released on February 26, attackers are releasing exploits in an effort to reach vulnerable systems before they can be patched.
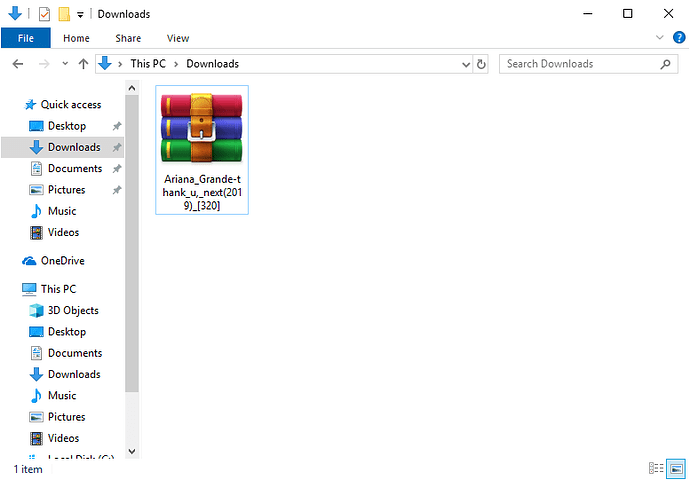
One recent example piggybacks on a bootlegged copy of Ariana Grande’s hit album “Thank U, Next” with a file name of “Ariana_Grande-thank_u,_next(2019)_[320].rar”
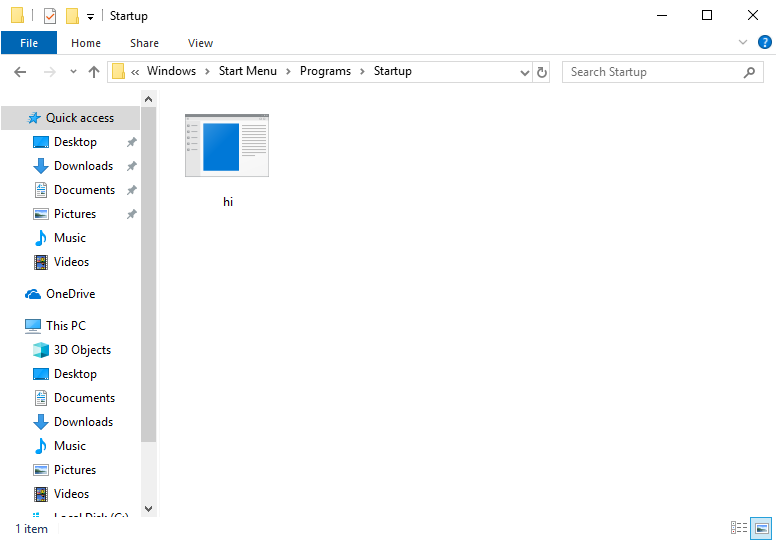
When a vulnerable version of WinRAR is used to extract the contents of this archive, a malicious payload is created in the Startup folder behind the scenes. User Access Control (UAC) is bypassed, so no alert is displayed to the user. The next time the system restarts, the malware is run.
Figure 1 – Malformed Archive detected by McAfee as CVE2018-20250!4A63011F5B88
SHA256: e6e5530ed748283d4f6ef3485bfbf84ae573289ad28db0815f711dc45f448bec
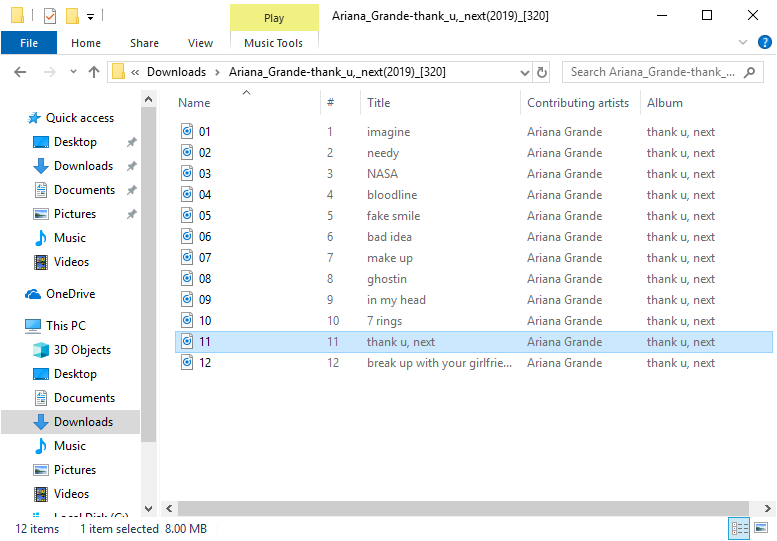
Figure 2 – Extracted non-malicious MP3 files
Figure 3 – Extracted Malware payload detected by McAfee as Generic Trojan.i
SHA256: A1C06018B4E331F95A0E33B47F0FAA5CB6A084D15FEC30772923269669F4BC91
In the first week since the vulnerability was disclosed, McAfee has identified over 100 unique exploits and counting, with most of the initial targets residing in the United States at the time of writing.
McAfee advises users to keep their anti-malware signatures up to date at all times. McAfee products detect known and unknown malformed ACE files exploiting the vulnerability as CVE2018-20250![Partial hash] starting with the following content
- V2 DATs version 9183 released March 2, 2019
- V3 DATs version 3634 released March 2, 2019
Additional GTI coverage exists for email-based attacks, in tandem with the Suspicious Attachment feature. When this feature is enabled, Artemis![Partial hash] detections will occur on known exploits.
The post Attackers Exploiting WinRAR UNACEV2.DLL Vulnerability (CVE-2018-20250) appeared first on McAfee Blogs.