ASEC analysis team has confirmed the distribution of malicious e-mail disguised as a free Bitcoin reward that targets specific individuals in Ukrainian Ministry of Defense. This malware uses a recent hot topic, Bitcoin, and tricks people into downloading the end-stage malware through various methods.
Upon downloading the PDF file attached to the e-mail, the user can see the content of the PDF file which states that Bitcoin can be received for free if the user accesses the short URL written in the file. There are a total of 3 URL links in the PDF file, and clicking either one of them redirects the user to the same address.
Currently, the website does not have both shortened and final connection URL, but at the time of analysis, it was possible to download the compressed file (bitcoin.zip). As shown in the figure below, the compressed file contains a shortcut (.lnk) file and a text file (password.txt). The text file looks as if it is there to provide the wallet URL and the password, but its true goal is to prompt users to click the ‘folder’ type Ink file. (‘Wallet in folder.’)
A closer look into the LNK file shows the malicious URL that downloads the executable file using powershell and names of saved files and folders.
When the user downloads the lnk file as the attacker intended, the malware is downloaded from the malicious URL, and is saved as WindowsUpdate.exe file in %Temp% directory.
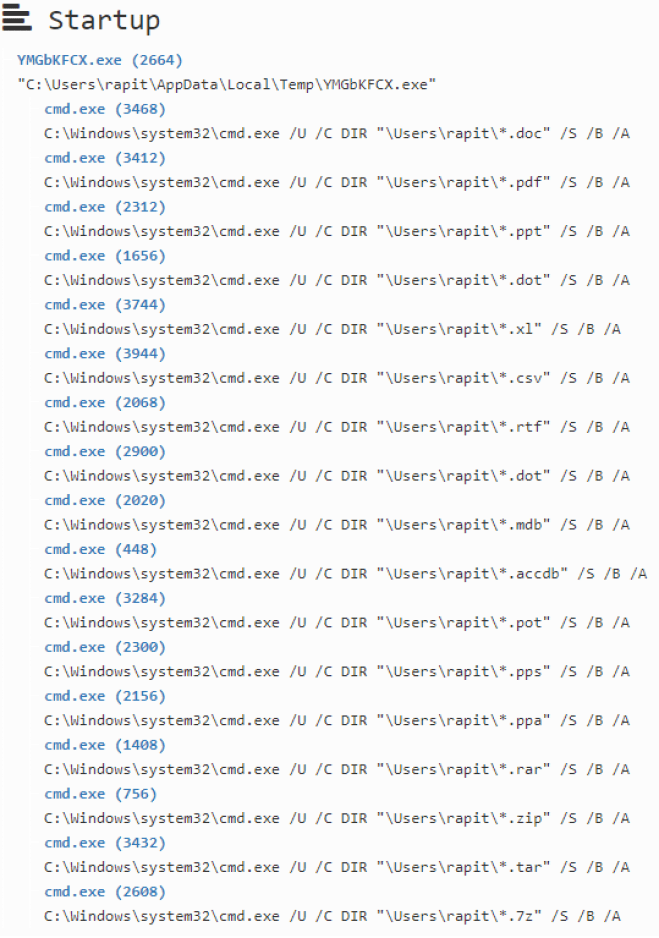
When the downloaded file is executed, it uses CMD dir command to check information of various folders and files. Seeing how it attempts network connection with the external URL, it seems the malware leaks the obtained information. Detailed information of the packet cannot be checked now as when a connection is attempted, the server sends an RST packet.
Attempts to exploit recent hot topics are being continuously discovered. Therefore, users must take extra caution when opening e-mails with attachment files. As introduced at the above, there is a chance that the attacker will utilize sneaky methods other than executable attachment files to deceive the users. This is why users should not download or run the attachment file even if it contains a theme that invokes intrigue.
It is also recommended to update the running anti-malware software to the latest version regularly, and maintain their security level as high as possible.
V3 detects and blocks the introduced malware using the following aliases:
[File Detection]
- LNK/Runner.S1
- Trojan/Win.Wacatac.R415645
[Relevant IOC Info]
- hxxp://1924[.]site/doc/bitcoin.zip
- hxxp://1924[.]site/soft/09042021.exe
- hxxp://31.42.185[.]63:8080/upld/30BC8771
- c717265dc91b1980921320c8d6257b53
- 5ab92ca35e41b9a7aa07cc7efc60bbd1
- d377c71f7df1c515705eb6b0cc745f7d
The post Attack Against Ukrainian Ministry of Defense Using E-mail Disguised as Free Bitcoin Reward appeared first on ASEC BLOG.
Article Link: Attack Against Ukrainian Ministry of Defense Using E-mail Disguised as Free Bitcoin Reward - ASEC BLOG