Fun Fact: The Extension "pysa" is probably derived from the Zanzibari Coin with the same name. Apparently it's quite popular with collectors. But enough of the pocket change, so let me put my two cents in on this sample :D

A general disclaimer as always: downloading and running the samples linked below will lead to the encryption of your personal data, so be f$cking careful. Also check with your local laws as owning malware binaries/ sources might be illegal depending on where you live.
Mespinoza (.pysa) @ AnyRun | VirusTotal | HybridAnalysis
--> sha256 a18c85399cd1ec3f1ec85cd66ff2e97a0dcf7ccb17ecf697a5376da8eda4d327
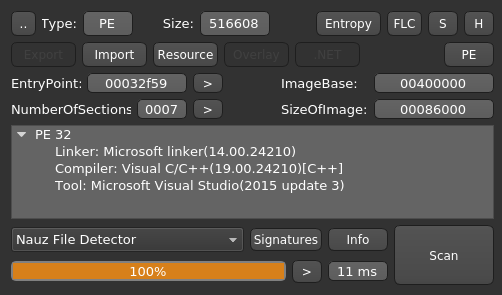
As always: Running Detect it easy on the executable:
One of the first things it will do is modify the SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System Registry Key to set the following values. Unfortunately I couldn't confirm this action in a sandbox with RegShot yet.

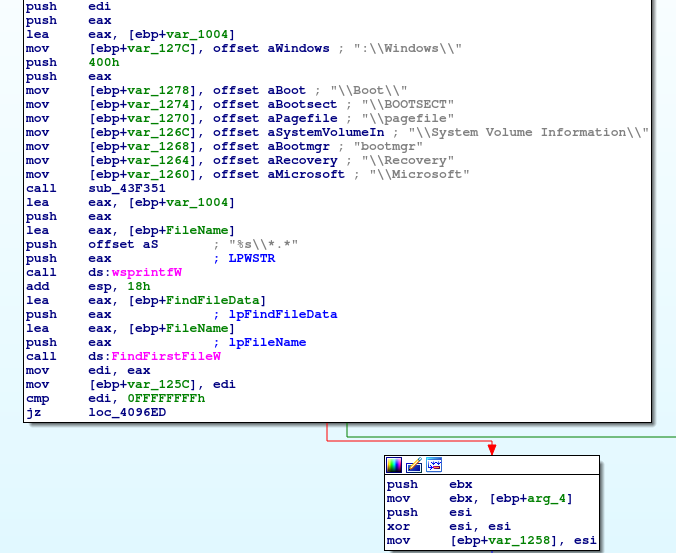
To retain basic functions of the Operating System Mespinoza will spare certain directories related directly to Windows and critical files.
It will also specifically look for SQL related processes. I will have to confirm this with a debugger, but most of the time database processes are killed by Ransomware to disrupt the service and make the files available for encryption.

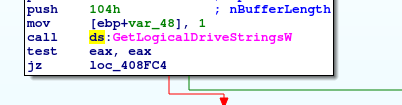
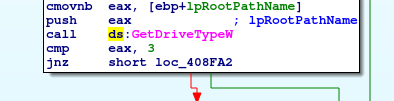
Of course Mespinoza won't stop with the system drive so it will check for connected removable media or shared network drives. GetDriveTypeW will tell it which type of media the selected device belongs to.
Up until now I have not seen a ransomware sample running verclsid.exe, so let's investigate: {0B2C9183-C9FA-4C53-AE21-C900B0C39965} corresponds to C:\Windows\system32\SearchFolder.dll and {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} matches the CLSID of IDBProperties which is part of the Microsoft SQL Server.
C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401
After looking at a string dump I found this hex string which is probably the key blob. I'll try to verify this with x32dbg later.
30820220300D06092A864886F70D01010105000382020D003082020802820201009CC3A0141B5488CD31B7D2DD49F9221483CF5FADB558A52CE7670169223BDA9B3C65785F411F22E2B5D0CB890B393A4ADDAAF5D650F7F6EAD43EB5F31002B04A97873A8044D5A8D4BAB19C05FBF645EEA9E2458BB4B2A73E1EF5D1955DD000C6C626C7805B683B3EA64AEA62D50D8A45D956DDB8691BC838406291F2FC3FC707F4C9DA763D62AC7F029A4616AE883004A912CA5EAE2C6211ADF8EA56532A5BDE53DAE58B6ED6B86D9780CB3B5B884FDC7487DAC357A42276E97C3DEFAB6A458063EBE9AFECBDF89B1BB9A7CFD5313D10D2D7CD6E14170B5C36F69508E8B5610C08328F2593E32D48B6BE378A2FDF58BB3ECDDAD9B69304F9936E93F84EE3660A42758F39D4EF8428E84551F3583602BB3230D662362C43A8E90B5B413A7416A1FCC89BD37A6A793192CF3E8552975E55FDA9472F7666CA4E6F59317AB7195B91C6B18959C6B91E70E40533F40126FECCCFB8E3BA2BE1804EEC3C54847A828C6F6665138E6E38D315198372B85B906E08EDC081A959B504E6583BA05D58D71BF7BD019B3F2C4BA800B5C7FFE04B0B8EF48095025E553B13304EAE76E23242266E6F8E7A1FEFF4F23B586F092932A765C8141F84A91D296F1EA2DCF5DB31E66BE8B76E1BB6DC1353CE5D2F998A2BA1C4ACF6CFEE7FB349A0B6A5E9D0CE010BD4D834F7EE2E265241D65C9B347BB69368DC59308EBE884EFB8389F4E31A20339B79020111
Turns out that the encrypted key is appended to the end of each file affected by the ransomware (which is a common tactic for some strains).

As this article is work in progress I will update it as soon as I can. As I did not see the Malware deleting the Volume Shadow Copies until now, so one option for possible victims would be to run Photorec or Recuva to check for recoverable files.
MITRE ATT&CK
T1215 --> Kernel Modules and Extensions --> Persistence
T1045 --> Software Packing --> Defense Evasion
T1012 --> Query Registry --> Discovery
T1114 --> Email Collection --> Collection
IOCs
Mespinoza (pysa)
1.exe --> SHA256: a18c85399cd1ec3f1ec85cd66ff2e97a0dcf7ccb17ecf697a5376da8eda4d327
SSDEEP: 12288:aVchT6oi+OeO+OeNhBBhhBBpiOTn5CjGGc4dXOsOjKf:aVc1Jiin5yGpMIj
File size: 504.50 KB
Associated Files
Readme.README %temp%\update.bat
E-Mail Addresses
aireyeric@protonmail[.]com ellershaw.kiley@protonmail[.]comUsed in previous campaigns:
mespinoza980@protonmail[.]com
alanson_street8@protonmail[.]com
lambchristoffer@protonmail[.]com
Ransomnote
Hi Company,Every byte on any types of your devices was encrypted.
Don’t try to use backups because it were encrypted too.To get all your data back contact us:
[email protected]
[email protected]FAQ:
Q: How can I make sure you don’t fooling me?
A: You can send us 2 files(max 2mb).Q: What to do to get all data back?
A: Don’t restart the computer, don’t move files and write us.Q: What to tell my boss?
A: Protect Your System Amigo.
Article Link: https://dissectingmalwa.re/another-one-for-the-collection-mespinoza-pysa-ransomware.html