Achieving anonymity while browsing the internet is the main concern for many people; everybody wants to make their communications secure and private. However, few in the world have really achieved this objective and many are still facing difficulties and trying different techniques to achieve online privacy.
The InfoSec community has produced various tools and techniques that utilize the TOR network to send the data securely and privately. There are advantages and disadvantages of TOR, and I do agree that many are using this for malicious purposes, but we can’t stop advancing technology because a few people have bad intentions.
WHONIX is an ideal example; it can act as an Internet gateway for any operating system and it can send data through the TOR network. However, Whonix is not the only option.
Tails OS is another option. It got immense visiblity after it was revealed that NSA whistle-blower Edward Snowden used Tails to hide his identity while sharing NSA secrets with journalists Glenn Greenwald and Laura Poitras.
How is Tails OS Unique?
Unlike Whonix, Tails OS is a live system that is designed to be used from a USB and DVD. Whonix is on the hard-drive and utilizes the hard-disk space, whereas Tails runs via RAM. Thus, it leaves no trace, even to someone with physical access to your computer/system. Tails is a free Debian-based OS. It has been designed to conserve your privacy and anonymity. It also comes with all the necessary applications, such as a web browser, messaging client, office suite, email client and more.
Tails does not depend on the host operating system or hard-drive. Since you can use Tails via USB/DVD, it is a plug and play device. You can use Tails from your friend’s computer, public library or from anywhere. It also leaves no traces because it uses RAM storage, which is automatically erased when the computer shuts down.
How to Configure Tails on a USB Drive
This section discusses the steps to configure Tails OS on a USB drive. You can download the live preview of the OS and create a bootable USB. Another way is to temporarily host the Tails OS in a virtual machine and create the bootable USB from there. To do this, you need the following:
- Tails OS ISO (download from the official website)
- USB stick (with more than 8GB of space)
- Virtual box
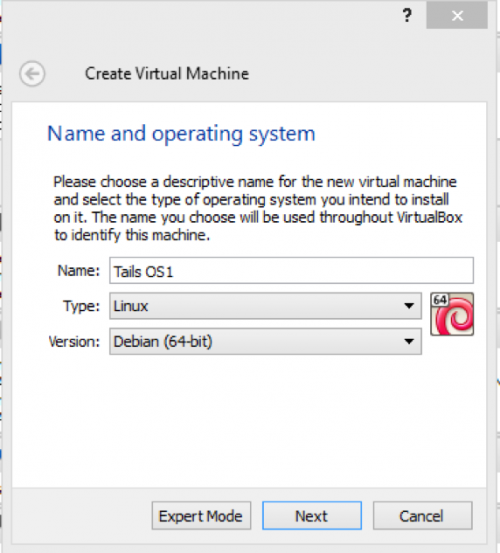
On your virtual box, click on new and give your image a name. Select Linux under type and Debian (64) for the version.
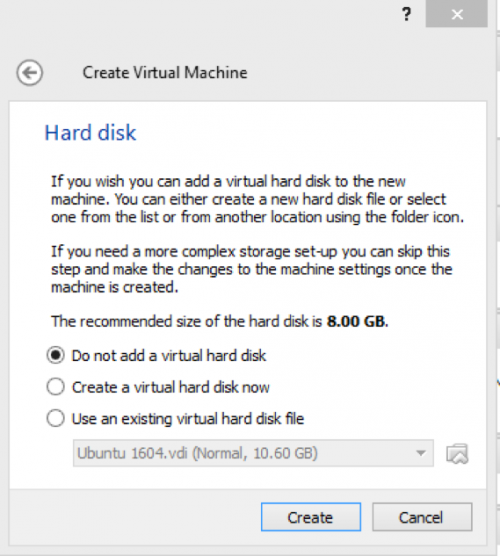
On the next screen, allocate the memory. 1024 MB is sufficient to start with. Do not create a virtual hard-disk, Tails is a live OS and it is not supposed to install on the hard-drive. So, in the next step, select the first option:
Create and continue. Go to the settings on the newly created virtual machine and load the downloaded ISO in the storage section. Don’t forget to enable the Live CD/DVD option:
Plug in the USB in the port and select the same device in the USB section of the VM settings:
Save the settings and start the machine. You will see the live preview of Tails OS. You can also see the installed and pre-configured software. Since we have not created any virtual disk for this, it will not store any information.
The next screen will ask you about more options, select no and login.
This is the live preview; you can use the TOR network securely here. Now let’s create the live USB. Select the application Tails and Tails Installer
Select the first option “Install by cloning”, since we are doing a fresh install. It will automatically detect the attached USB device, as we already synchronized via settings in the aforementioned step. Click on Install Tails and the process will begin.
Once it’s completed, you can simply plug your USB in any machine to use the secure and private operating system. Another method is to directly create the bootable USB instead of cloning. However, cloning is the recommended method to establish the stability of Tails.
Conclusion
The steps previously mentioned are for beginners who seek anonymity or want to learn how to achieve anonymity using Tail OS and the power of Tail OS over Whonix. Achieving anonymity has advantages that make it critical amongst cyber security practitioners; however, people rush to use TOR without exploring its power and end up giving away their critical information without knowing it. To achieve complete anonymity, one should explore TOR and Tail OS, as no tool or OS can be used for custom purposes without proper configuration. It is highly recommended to use such tools and an OS cautiously and for good InfoSec reasons.
Article Link: http://feeds.feedblitz.com/~/477624310/0/alienvault-blogs~Achieving-Online-Anonymity-Using-Tails-OS