 Since 2015 there has been a steady increase in threat actors’ use of SSL certificates to add an air of legitimacy to malicious websites. By the end of 2017 almost a third of phishing sites had SSL certificates, meaning their URLs began with HTTPS:// and (most) browsers displayed the all-important padlock symbol.
Since 2015 there has been a steady increase in threat actors’ use of SSL certificates to add an air of legitimacy to malicious websites. By the end of 2017 almost a third of phishing sites had SSL certificates, meaning their URLs began with HTTPS:// and (most) browsers displayed the all-important padlock symbol.
In recent months, however, our team has observed an even more dramatic increase in the use of SSL certificates on phishing sites, with the rate reaching 49.4 percent by the end of Q3.
To find out more about this meteoric rise in SSL certificate usage — and the reasons behind it — you can read our annual Phishing Trends and Intelligence (PTI) report and previous blog posts (1, 2) on the subject. These show that threat actors have doubled the number of malicious sites using SSL certificates on them to trick unknowing users into falling for their schemes. We’ve also recently spoken on the subject with Brian Krebs and CNET.
In this article we’d like to share the latest numbers with you, and briefly summarize a few key learning points.
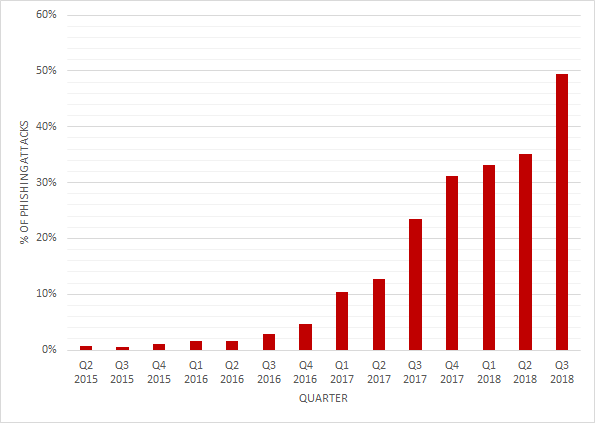
Q3 2016: 2.81%
Q3 2017: 31.20%
Q3 2018: 49.42%
Notice how quickly uptake of SSL certificates has risen — From less than three percent in 2016 to almost 50 percent by the end of Q3 this year. There are several reasons for the shift:
“In Q3 nearly half of all phishing sites, 49 percent, were using SSL, up from 35 percent the prior quarter,” said John LaCour, PhishLabs Founder and CTO. “PhishLabs believes that this can be attributed to both the continued use of SSL certificates by phishers who register their own domain names and create certificates for them, as well as a general increase in SSL due to the Google Chrome browser now displaying ‘Not Secure’ for websites that do not use SSL.”
The bottom line is that the presence or lack of SSL doesn’t tell you anything about a site’s legitimacy.
More specifically, this is not to say that Chrome’s use of Secure (padlock) or Not Secure isn’t inherently wrong, but it is at best misleading. In most cases, users simply don’t understand what component of a site is considered secure, in this case, encrypted communication, and that leads to misconceptions about the site and its legitimacy.
This is no different than how users may quickly agree to a website's Terms of Service without reading it or try to build an Ikea desk without using the instructions. At first glance, there shouldn’t be any issues, but later on, the repercussions could become problematic.
In a perfect world, it would be easy to blame software vendors and sit around waiting for them to improve their messaging, and ultimately solve this problem for us, but that won’t fix things in the short-term.
In the interests of minimizing the risk of average Internet users getting hoodwinked by phishing campaigns — both at home and at work — security awareness is key. Improving the security awareness of users at your organization can have a profound impact on cyber risk, and substantially reduce the number of security incidents (and ultimately breaches) you have to deal with.
Regardless of how much gamification, pop culture, or humor you put into your training, users still won’t love security awareness training. And ultimately, unless your users are truly retaining the information you’re trying to impart, all those annual or biannual sessions are for naught.
This is specifically why we suggest taking a short, focused, and frequent approach to security awareness training. Instead of attending long, infrequent training sessions, users digest new information on a monthly basis through engaging and interactive digital training sessions — and best of all, it all takes less than five minutes to complete.
If you’re interested in learning more about how to implement a short, focused, and frequent security awareness training program at your organization, reach out to our team.
For more insights into how threat actors are abusing HTTPS and SSL certificates, stay tuned to our site, as we’ll be releasing the next Phishing Trends and Intelligence report ahead of RSA in 2019.
Article Link: The Leader in Digital Risk Protection | Intelligence & Mitigation